Are Your DASTs Really Working?
We tested different Dynamic Application Security Testing (DAST) engines alongside Equixly to find out which API vulnerabilities they detect and which ones go unnoticed. The testing was carried out on the same vulnerable API.
The DAST engines were selected due to their widespread adoption and their role as the backbone of most commercial DAST solutions used for API security testing.
For example, Checkmarx and Noname Security incorporate ZAP as the core engine within their API security platforms.
We replicated the test to get consistent results.
This is what we found:
- Equixly discovered 80% more security issues than the traditional DAST solutions.
- Equixly found 8 types of high-severity vulnerabilities, as opposed to none found by the other engines.
The Test: Traditional DAST Engines vs. Equixly
Here are some highlights from the comparison
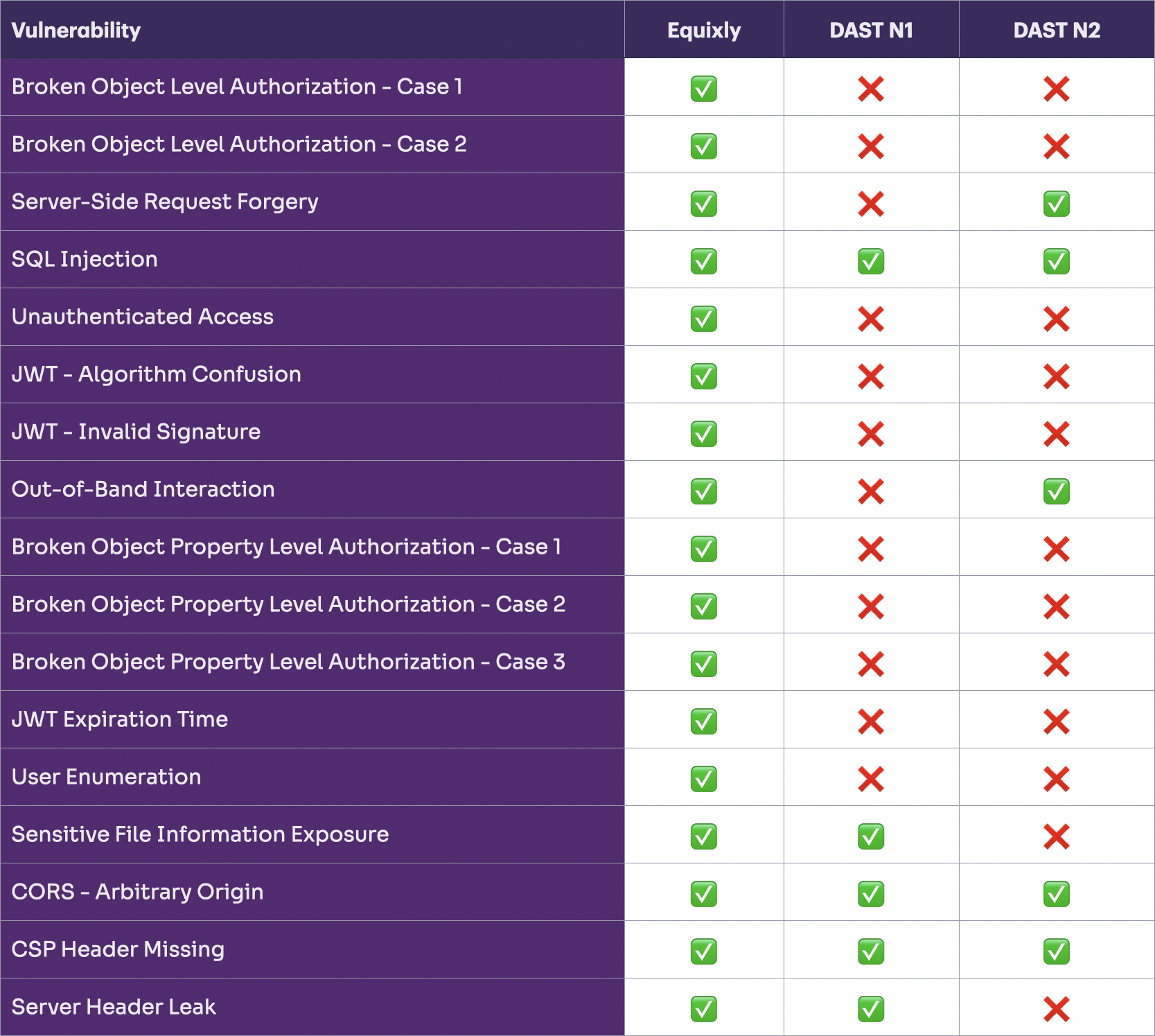
- High-severity vulnerability detection: Traditional DAST engines failed to identify any high-severity logic vulnerability. That’s highly concerning, given that the testing target was an intentionally vulnerable API designed with a slew of security risks. In contrast, Equixly discovered all the logic vulnerabilities present in the API.
- Nomenclature and specialization: In the original reports, Equixly and DASTs had different vulnerability nomenclatures, with Equixly’s terminology clearly reflecting its specialization as an API security solution that adheres to the OWASP standards. That set Equixly apart from all the generic web application security tools using traditional DAST engines.
- Report quality and detail: Equixly’s reports were much more extensive and detailed compared to those generated by the traditional DAST engines, providing deeper insights into the detected vulnerabilities and the API security posture.
Why DAST Engines Are Not Suitable for API Security Testing
Traditional DAST engines were originally developed to secure web applications, not APIs. Over time, they’ve been adapted to include API security testing, primarily through the import of API specification files.
An example of such a DAST engine is ZAP, which was released in 2010. At the time, the primary security concerns included issues like SQL injection and cross-site scripting (XSS).
However, the API landscape has evolved a lot since then. Modern APIs introduce new complexities that traditional DAST engines were not originally designed to handle. For example, APIs often involve complex business logic, multi-API exploits, and different authentication mechanisms.
Traditional DAST engines fail to understand API workflows and business logic. As a result, even with enhanced UI interfaces, they continue to miss critical vulnerabilities that are essential to address to achieve robust API security.
Traditional DAST Engine Scanning Is Not Sufficient
There are three main reasons why traditional DAST engine API security testing is insufficient:
- Traditional DAST engines don’t test for the OWASP Top 10 API Security Risks, and testing for these is imperative for any API security testing solution.
- Traditional DAST engine active scanning is limited in scope and cannot detect logic vulnerabilities. Examples of logic vulnerabilities include access control issues, such as BOLA and broken authentication, which are among the most severe and frequent security risks plaguing the APIs today.
- APIs differ significantly from web applications and cannot be explored through the usual browsing and spidering techniques. While importing OAS files offers a superficial workaround, traditional DAST engines fundamentally fail when it comes to testing multiple APIs and interacting with endpoints within workflows. They’re built on outdated concepts that are not suited for the demands of modern API ecosystems.
To summarize, traditional DAST engines are built on obsolete principles that no longer align with the complexities of modern API security needs.
DASTs and API Testing
On top of being used for standalone API security testing, traditional DAST engines have served as the foundation upon which cybersecurity vendors build their own DAST solutions for both web application and API testing.
For example, industry leaders like Checkmarx and Noname Security integrate traditional DAST engines into their API security platforms. Similarly, companies such as PortSwigger utilize Burp Suite as the core engine for their security testing services.
These integrations demonstrate how traditional DAST engines remain integral components in various commercial offerings despite the evolving demands of API security.
However, the fundamental architecture of these tools has not significantly evolved. The primary enhancements often involve superficial changes, such as user interface upgrades, without addressing the core limitations inherent in traditional DAST engines. This results in an incomplete list of vulnerabilities detected.
Regardless of the vendor, traditional DAST solutions have generally proven insufficient for API security testing. If not for other reasons, then because they miss logic vulnerabilities, just as their foundational engines do.
It’s worth noting that the list mentioned above is by no means exhaustive. Popular API security solutions that are not on this list and are not traditional DASTs might also rely on these legacy DAST engines.
What Makes Equixly Different?
The key difference between Equixly and traditional DASTs is Equixly’s proprietary AI ecosystem.
Equixly leverages a multifaceted AI approach that includes custom Large Language Models (LLMs), specialized models for distinct security tasks, reinforcement learning algorithms, and an in-house, scalable infrastructure to preserve the privacy of our customers.
The platform is tailored to API security testing and pentesting and fine-tuned to produce optimal results.
Decreased Probability of False Positives
Traditional DAST engines not only fail to understand API logic but also often generate too many false positives.
Instead, Equixly’s AI efficiency in dealing with large volumes of data and possible scenarios allows it to minimize the likelihood of false positives.
In a Nutshell
Equixly’s proprietary technology enables you to:
- Conduct more comprehensive tests;
- Cover a much wider range of vulnerabilities, including the OWASP API Security Top 10 and logic vulnerabilities;
- Produce much more accurate testing results than any other DAST solutions.
Conclusion
To get better results when testing your APIs, you must look for a security testing solution built strictly for APIs.
Equally important, this solution should integrate a powerful, forward-looking technology such as artificial intelligence. Not because that’s trendy and sounds cool, but because it works.
Reach out to see the complete results of Equixly’s test and learn more about the technology and experience that made them possible. We’d be honored to help and answer any questions you have.

Alessio Dalla Piazza
CTO & FOUNDER
Former Founder & CTO of CYS4, he embarked on active digital surveillance work in 2014, collaborating with global and local law enforcement to combat terrorism and organized crime. He designed and utilized advanced eavesdropping technologies, identifying Zero-days in products like Skype, VMware, Safari, Docker, and IBM WebSphere. In June 2016, he transitioned to a research role at an international firm, where he crafted tools for automated offensive security and vulnerability detection. He discovered multiple vulnerabilities that, if exploited, would grant complete control. His expertise served the banking, insurance, and industrial sectors through Red Team operations, Incident Management, and Advanced Training, enhancing client security.