AI in API Security
Carlo De Micheli, Zoran Gorgiev

We’ll spare you the unnecessary talk about how AI is taking over the world.
AI is here. So, what does that mean for API security? Read (skim) on, and you might stumble upon something worth your time.
How Much Does API Security Need Artificial Intelligence?
A lot. Desperately, urgently, badly.
Let’s look at some recent numbers to show that this is not an isolated, lonely, subjective opinion.
The “State of Cyber Security 2024” report by Darktrace revealed that 74% of the 1,800 cybersecurity leaders and practitioners surveyed stated that their organizations had already felt the impact of AI-powered cyber threats. As much as 96% thought security solutions employing AI were necessary to fend off these threats.
These findings are general—not specific to API security—and relate to only one category of cyber threat. However, they’re still relevant to API security since they show the recent tendencies in both attackers’ and defenders’ circles.
Artificial intelligence can play a role in every stage of the cyber kill chain—from reconnaissance (e.g., carrying out OSINT) to exploitation (network probing) to actions on objectives (account harvesting). Ethical hackers have already warned about the techniques that threat actors can use AI to automate attacks, improve phishing, obfuscate malicious code, and generate payloads at a highly efficient pace.
For instance, security researchers demonstrated how attackers can use generative AI to create pieces of code that are harmless separately (so that the LLM won’t refuse to generate them) but malicious when combined into a single program. And not just any malicious program but malware that evades detection.
These techniques can also be used to target APIs or underlying systems through vulnerable APIs. Add to this the fact that the unimaginably fast growth of API use is accompanied by the enormous expansion of the API attack surface, and you soon realize that securing APIs is indeed no longer a human-scale problem.
Besides, API security necessitates AI because of the lack of a qualified workforce. Studies show that the global shortage of cybersecurity professionals is around 4 million unfulfilled positions and that there’s an increasingly obvious connection between workforce gaps and security breaches.
Imagine how worse the API security predicament is in that regard, considering that we have recognized API security as a separate cybersecurity subdiscipline only in the last several years.
If you look at the available API security technical literature, courses, and other educational resources, you’ll mostly find material from the last few years. And with the lack of systematic, structured, and formal API security education that doesn’t revolve strictly around OWASP API Security Top 10, it’s hard to see how we can fill workforce gaps anytime soon.
In the meantime, the number of API security incidents is growing, and we must do something about it. AI can be that something.
What Can AI Do for API Security?
If we leave all the social and ethical discussions about the advent of a higher form of artificial intelligence aside, currently, AI is neither Lisan al Gaib nor Darth Vader.
On the one hand, this technology won’t solve your security problems by itself if you don’t have suitable people and processes in place. Moreover, overreliance on AI can be as harmful as overreliance on static, rule-based security technologies like WAFs (web application firewalls). If for no other reason than because AI can endanger data privacy and is prone to errors.
On the other hand, AI doesn’t bring demise to human skills, expertise, and decision-making in cybersecurity. Instead, it’s here to expedite the security and development teams’ efforts. Artificial intelligence enables you to catch up with the pace of unprecedented rapid change in the threat landscape and alleviate the pressure of high business demands.
More specifically, some of the areas in which AI can help API security are the following:
- Secure API coding
AI can help developers weave secure coding practices into API development. If applied to API component testing during the software development life cycle (instead of production), this can avert security risks stemming from code bugs and errors.
- API threat detection and response
AI can differentiate between users based on the way they typically engage with an API.
When a user’s behavior doesn’t fit into the usual behavioral pattern, an AI system can detect this change and take action. A deviation from the expected behavior, especially if it’s prolonged and highly atypical, often indicates an account compromise resulting from broken authorization.
This ability to recognize anomalous behavior and act upon detection can also allow AI systems to differentiate between human and bot activity and prevent automated API attacks.
- Zero-day API vulnerability discovery
One of the most powerful capabilities of artificial intelligence is to autonomously learn, evolve, and become increasingly efficient over time.
From the enormous amounts of security vulnerability data that engineers feed into it and its experience with security threats, an AI system can develop the ability to recognize traces of new threats and discover the occurrence of a zero-day vulnerability.
- API security posture management
By API security posture management, we mean primarily API discovery and data classification.
Artificial intelligence can discover unknown APIs, such as shadow APIs. For instance, an AI system can inspect and monitor GitHub repositories to identify API code. Among the identified APIs, it can find and report forgotten endpoints, thus improving your API inventory management.
In addition, NLP (natural language processing) engines can locate API endpoints that operate with sensitive data like PII (personally identifiable information). That allows you to see which endpoints require security hardening to prevent the leakage of sensitive data.
- API security testing
AI allows you to automate API security testing so you can discover vulnerabilities much faster than traditional manual testing.
Considering that artificial intelligence is much more efficient than humans in tackling and operating extensive volumes of data, it can scan even large APIs with numerous endpoints, analyze the responses, and report on any significant security vulnerabilities at high speed.
API penetration testing is where AI especially excels. An AI system can act as a malicious actor and launch cyberattacks, such as injections, to expose exploitable security vulnerabilities.
How Does AI Work in API Security Solutions?
The same “State of AI in Cyber Security 2024” report we referred to earlier provides another interesting statistic. Namely, 31% of the surveyed respondents:
- Weren’t sure which types of AI were used by security vendors
- Were confused by the way vendors talked about AI in their products
- Preferred security vendors to explain which AI type they used and the reason behind their choice
These findings come down to the following: Security leaders and practitioners must be informed consumers. Regardless of whether they’re (potential) customers, they deserve to know how a specific AI-powered API security solution works. Transparency and explanation in plain language are key in that regard.
Hiding trade secrets and proprietary technology is justified, but no one needs that many details anyway. Simply, as with any other product or service, people want to know what they look at, how it works, and how they can use it optimally. The usual marketing rhetoric and generic explanations that don’t really explain anything simply won’t do the job.
Besides, understanding and knowledge breed a sense of control over the product and confidence. With that in mind, let’s look at an example of an API security platform powered by artificial intelligence.
Equixly: How an API Security Platform Uses AI to Find Vulnerabilities and Strengthen Your Security Posture
Equixly is an API security platform that covers two domains: security testing and security posture. Its focal point is automated API pentesting, but it uses artificial intelligence to power multiple functionalities within its offering.
It’s worth noting that your data never leaves Equixly’s environment, and the platform doesn’t rely on third parties. Equixly’s team trains and fine-tunes the AI models itself and uses different algorithms for different purposes.
Smart API Fuzzing
During the initial exploration phase, Equixly’s machine learning models craft inputs to make sure the next steps get explored, for example, using a valid email address for a registration step. Also, the responses from the APIs are taken into account to craft the following requests.
Dumb fuzzing means sending static or random inputs that have very little to nothing in common with the shape of the predicted input. In contrast, Equixly’s smart fuzzing sends a wide range of unanticipated inputs that conform to the shape of valid input and can pass parser checks.
For instance, if an API sends a booking date as a parameter, Equixly’s AI engine allows the platform to create relevant and unanticipated variations on the theme date (say, past dates) to produce unexpected API responses and behavior and crash the server.
AI-powered smart fuzzing has much greater code coverage and allows you to get deep into the API/app logic and find more (subtle) vulnerabilities, such as business logic flows.
Zero-Day Vulnerability Discovery
Identifying exploitable vulnerabilities is one of the primary areas that security leaders and practitioners expect AI to affect in the future. Equixly is already making good use of artificial intelligence in API vulnerability discovery.
The API security platform relies on a proprietary machine learning, more precisely, reinforcement learning algorithm, to find security issues. This algorithm allows Equixly to act as an autonomous agent in highly complex environments, capable of making decisions leading to optimal solutions/results.
Equixly’s proprietary ML algorithm also enables the security solution to make sound inferences in and about previously unseen environments. That makes it possible to find signs of zero-day vulnerabilities in addition to the already known API security risks like the OWASP API Security Top 10.
Shadow API Detection
Equixly detects shadow API endpoints based on your API definition file.
The security platform’s AI engine allows it to query your API by sending data extracted from immense wordlists and inspecting the API responses. It compares the results to the specification file. Any differences between the two suggest that there are API endpoints in your environment that are hidden and undocumented and, hence, that you didn’t know about.
To support your API posture management efforts, Equixly creates a patched version of your API definition file with the detected unknown API endpoints.
Parameter Linking
Equixly uses AI to understand how different APIs link through parameters in a sequence of events.
Suppose a user wants to make an online purchase, and the e-commerce web app relies on multiple components that communicate with each other through different APIs to complete the checkout process.
API A passes a parameter data value, such as a user identifier, to API B, which passes the same parameter value to API C. The same data value is an output for one API and an input for another. This sequence is an example of parameter linking.
When you upload your APIs to Equixly, the platform uses AI to link them by understanding which parameters’ data values are outputs and which are inputs for the different APIs.
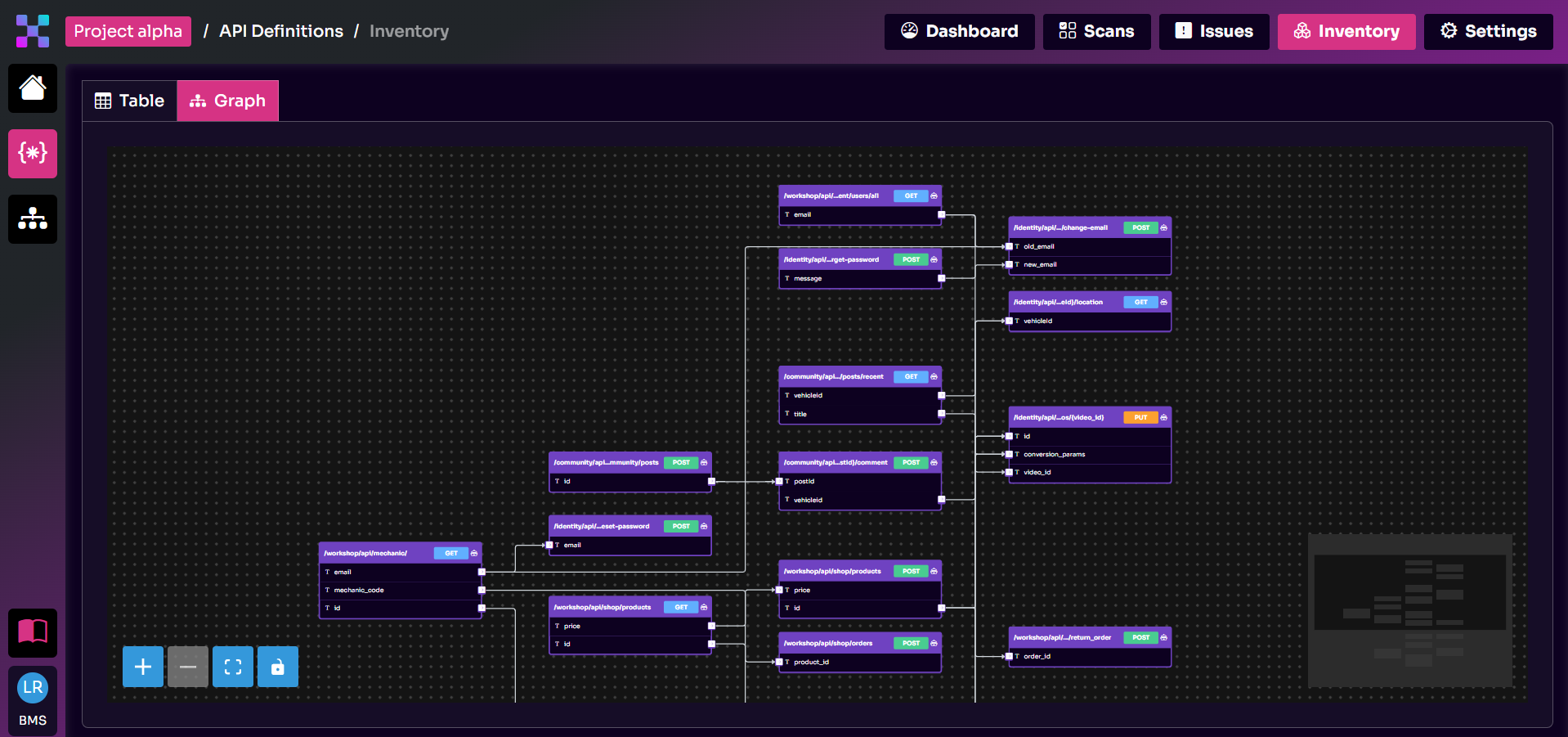
The most important side of this capability is that AI gives Equixly context awareness, so it recognizes parameter linking regardless of whether the variables that store the same data value have the same name in different APIs.
For instance, in the example above, the variable can be called userID in API A, user in B, and id in C; Equixly will still be able to find the connection. Moreover, it would locate the connection even if the parameter variables had completely unrelated names.
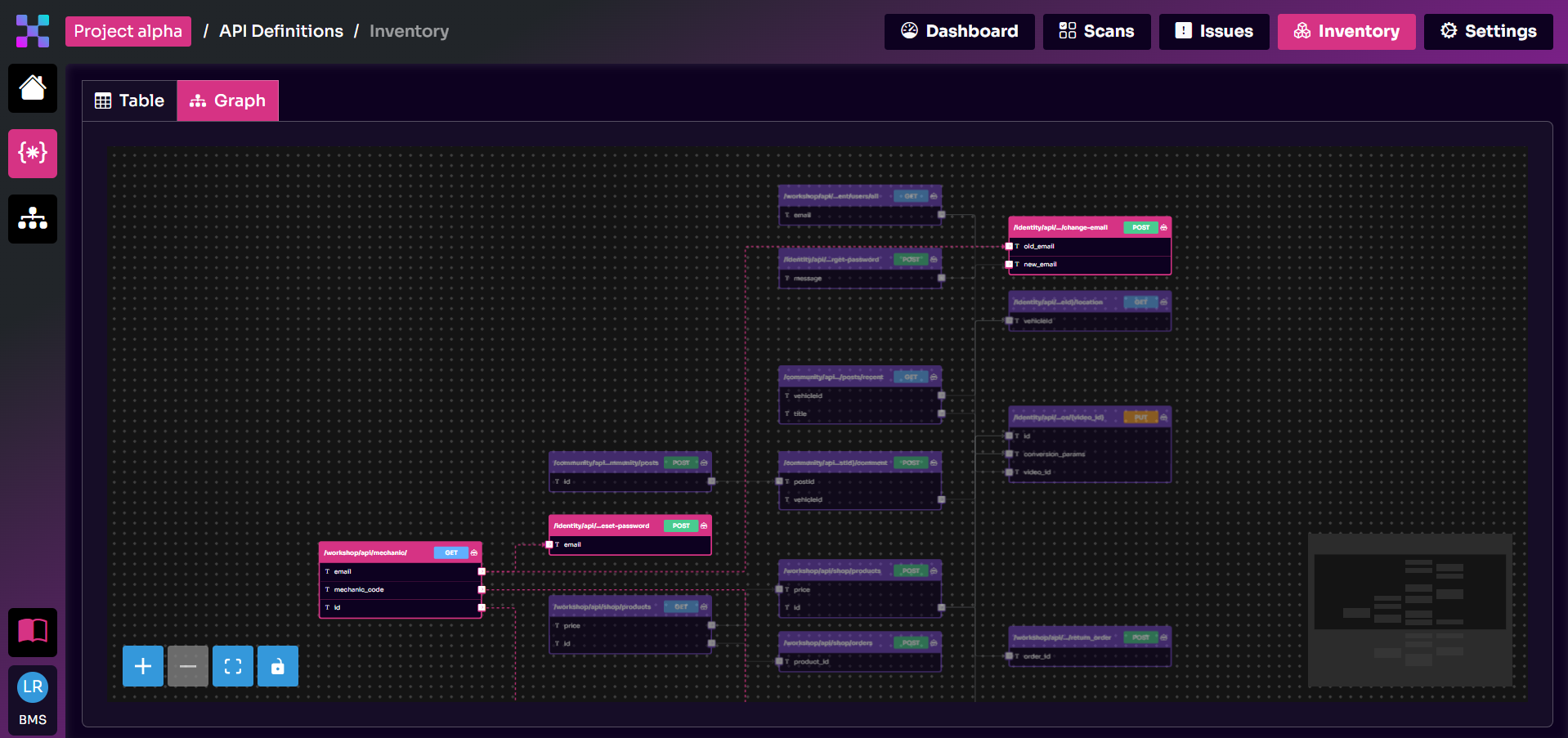
Another important aspect of Equixly’s AI parameter linking is that the platform can find APIs that connect to each other just from the API specification files. In other words, it doesn’t rely on recorded traffic and traffic analysis like other security solutions.
API traffic doesn’t necessarily give you all the possible API paths and flows that indicate the connection between different APIs. To eliminate this drawback, Equixly generates all the possible paths itself.
The point of Equixly’s AI parameter linking is to check for possible exploitable security issues in the way APIs link to each other.
Visual API Flow Graph
Equixly presents the results of the parameter linking operation in a visual API flow graph.
By using artificial intelligence, Equixly finds links between APIs even when they’re not specified in the documentation or Swagger files, creates those links automatically (without external intervention), and highlights them in a visual graph.
This functionality is unique to Equixly. As far as we know, there’s no other API security solution that offers a similar feature.
Conclusion
The large API attack surface, the subtlety and frequency of security threats, the almost unchecked proliferation of APIs, and the fact that threat actors already have artificial intelligence at their disposal make AI necessary for supporting our current API security efforts. But remember: AI can bear fruit only as part of an organization’s overarching security strategy that includes the right people and processes.
API security vendors already use AI in their products to offer better and more extensive coverage of the security of your APIs. Generally, what they need to improve is transparency about the concrete ways they take advantage of artificial intelligence.
In an effort to be more transparent, we described some of the ways Equixly utilizes artificial intelligence for security testing and posture management.
Contact us to discover more about Equixly’s AI-powered API security platform, dig deeper into AI in API security, and learn the new functionalities we’re preparing for you.

Carlo De Micheli
Director of Product Marketing
Carlo is a versatile professional with extensive international experience. His enthusiasm for innovation extends across cybersecurity, automotive, and aerospace, where he actively engages in pioneering projects. Holding a technical background in aerospace engineering and supplementing it with independent studies in programming and security, Carlo has organized and presented at international conferences and established tech startups related to the sharing economy and fashion before embracing marketing and sales.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.