APIs in the Utilites Sector
Carlo De Micheli, Zoran Gorgiev

The utilities sector provides the essentials of life as we know it today. With it in crisis, we’d return to some distant, distant times.
Of course, we don’t mean the good side of those distant times, like riding horses, sharpening swords, or drinking ale (yes, water was a health risk for a long time due to contamination and poor sanitation).
We mean some next-level dark stuff, such as not seeing anything at night, having no internet and functional smartphones, and being unable to cook, drink clean water, shower, and brush away the morning breath. Yes, it’s dark there.
This imaginary darkness can quickly become real. How? Through exploited insecure APIs. How precisely? Bear with us, and you’ll discover.
A Few Remarks on Utilities
Is “utilities” a sector or an industry? People sometimes use the two terms interchangeably, disregarding their differences, which creates confusion.
“Sector” is a more general term than “industry.” One sector consists of multiple industries. For instance, the IT sector includes the cybersecurity, software, and artificial intelligence industries, to name a few. Apart from industries, we can also call these subsectors.
The appropriate term for utilities, or sometimes power and utilities, is “sector.” A sector is nothing else but an extensive group of companies performing related business actions.
The power and utilities sector comprises electricity, water, and gas provision companies. Electric power and oil and gas are two examples of industries that fall under this sector.
Some utility companies offer multiple aggregated utilities or multi-utility services. Iren Group in Italy is an example of a multi-utility company operating in the gas, electricity, integrated water, district heating, and environmental services areas.
Other companies specialize and focus exclusively on one service. Georgia Power in the United States is an example of this type.
APIs in Utilities
Today, economic sectors are undergoing profound digital transformation. Digitalizing utilities may be trickier because they fall within public services and are heavily regulated, but it is happening and is irreversible. And just like in other sectors, APIs lie at the heart of it.
APIs are communication interfaces that enable different types of software to talk to each other through the Internet. They allow us to operate with and consume more data than ever before. At the same time, they have mechanisms that make it possible to control what information we expose, to whom, and to what extent.
In the power and utilities sector, APIs allow:
- Legacy systems with previously locked-in data to communicate with each other and connect siloed services
- Internal systems to integrate with external systems, that is, third-party software
- Diverse data sources—such as sensors, connected meters, IoT devices, and SCADA systems—to exchange data
- Utilities to introduce mobile and web apps for partners and end users, for instance, to establish contracts and manage payments
- Users and regulatory bodies to gain insight into energy consumption
Automation is one of the utilities’ most significant API-driven digitalization benefits. A smart utility solution such as automated load balancing relies on real-time gauging of meteorological conditions and user consumption—a capability made possible through APIs.
Another significant benefit is enhanced user experience. APIs allow utility companies to meet the modern demands for convenience, accessibility, and transparency by enabling users to view, manage, and control their energy usage.
Higher energy efficiency is the third major benefit of API-driven digitalization. Better control and management of power consumption through API-extended capabilities leads to more efficient and intelligent energy spending.
However, like virtually everything else, the API-reliant digitalization of the utilities sector is not without its challenges.
On the one hand, immense volumes of invaluable business and private data are shared and exposed to third parties to allow the sector to thrive and democratize. On the other hand, with data openly and massively shared come new threats and a much larger attack surface.
How do we address this issue?
The responsibility falls mainly on API security or lack thereof.
API Security in the Utilities Sector in Numbers
Not much research has been done on API security in the utilities sector. Hence, there aren’t many reports that allow us to compare results and draw conclusions about general tendencies.
Nonetheless, the evidence from current research is sufficient to begin understanding what needs to be improved and how to fortify current and future APIs.
A 2022 study found that 78% of utility companies suffered an API security incident in the last 12 months. Among the top incidents were:
- Network firewall events
- Shadow or zombie APIs
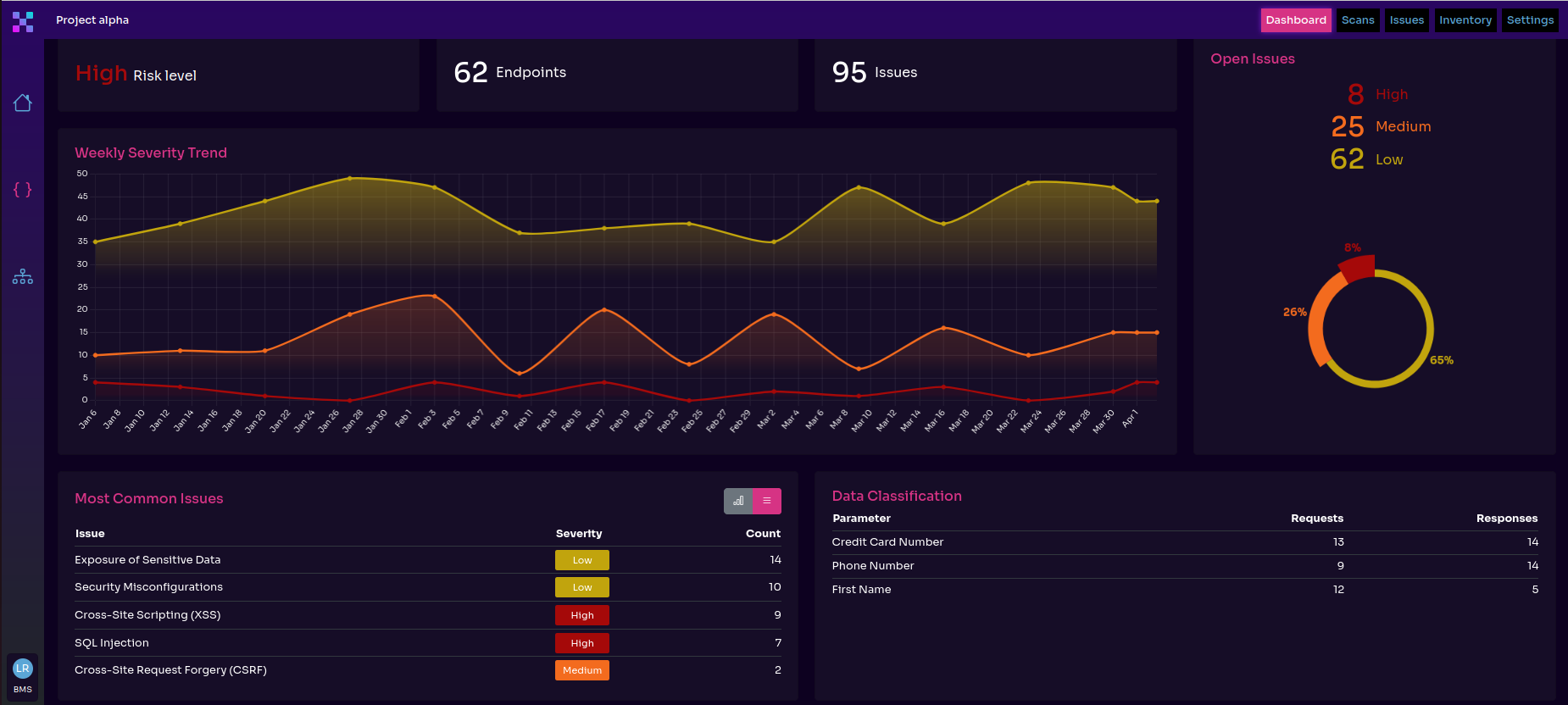
Speaking of shadow and zombie APIs, 81% of the surveyed companies lacked full visibility into their API landscapes. They didn’t know which API endpoints returned sensitive data—meaning they didn’t have data classification mechanisms in place—or didn’t know all the APIs they relied upon. These issues fall within the category of improper inventory management.
Only 7% tested their APIs in real time. 25% carried out an API security test at minimum once a day, 45% less than once a day, 21% less than once a week, and 4% less often than once a month. Those are truly sorrowful security testing statistics.
Regarding compliance, less than half, 47%, stated their API security solution allowed them to comply with GDPR, and 28% said it allowed them to comply with other regulations.
Blackouts, Sandworms, and APIs
We still fall short of extensive, in-depth material on API-related security incidents in the sector.
Indeed, utility digitalization is happening at a slower pace than, for instance, automotive digitalization, which can lead to the conclusion that utilities have yet to experience major newsworthy API security incidents.
However, as the stats from the previous section suggested, we can’t explain the shortage of material with a shortage of API security incidents, at least not entirely. There are incidents, but we just don’t know about them.
Why? It could be the lack of publicly available company reports or that security researchers are yet to turn their attention to these matters. Nevertheless, to express it dramatically, we’re not left in the lurch.
Sandworm
2015 saw the first official hacker-caused blackout in human history. The victims were three unrelated power companies’ substations in different parts of Ukraine.
This cyberattack started with a phishing email containing a malicious Word attachment that ran a macro in the background. The macro infected the systems with the BlackEnergy malware and affected a VPN the companies used to remotely access their systems, including control software.
It would later become clear that the perpetrator of the attack was Sandworm.
Sandworm is not the macabre creature from the 1984 Dune, though it bears a resemblance (hence the name). Sandworm is an elite and extremely powerful threat group that falls within the categories of APTs (advanced persistent threats) and state-sponsored hacker groups. Cybersecurity experts believe it’s associated with Russia’s military intelligence service.
Sandworm is unique for it’s the only hacking group that has successfully and repeatedly caused power outages through cyberattacks. One of them involved an API.
MicroSCADA and SCIL-API
The attack happened in 2022. Again, the target was the Ukrainian power grid, and the consequence was a new blackout.
This attack fit the threat group’s general tendency at the time to use a living-off-the-land technique. This technique allowed Sandworm to speed and scale up operations while decreasing detection probability.
To cause a power outage, Sandworm exploited a security vulnerability in an end-of-life version of the MicroSCADA X DMS600 control system. This obsolete and unsupported version allowed access to the SCIL-API interface by default, which would turn out fatal for the victim’s power substation environment.
MicroSCADA X DMS 600 is produced by ABB, now Hitachi Energy. This software solution helps utility companies automate and centralize control of power distribution networks. Loosely speaking, the solution consists of two main components:
- MicroSCADA for energy automation and centralized control
- DMS600 for network control and distribution management
The SCIL-API interface—where SCIL refers to the language used for MicroSCADA programming—allows communication between these two components.
Since the API interface became obsolete in 2014, this communication role was delegated to the OPC (open platform communications) interface. That’s why the SCIL-API should’ve been deactivated. However, it wasn’t, and it’s not clear why.
Security researchers couldn’t discover how Sandworm gained initial access to the victim. The reason for this and other unknowns was that the attackers used a variant of CaddyWiper, a wiper malware with anti-forensic capabilities written in C, to remove artifacts and externally uploaded files.
Nonetheless, what researchers knew for sure was that Sandworm accessed the MicroSCADA system by accessing the virtual machine that hosted it.
After the attackers gained unimpeded access to the SCIL-API, they abused the MicroSCADA “scilc.exe” program to execute a file with unauthorized SCIL commands through the SCIL-API (a file that was also impossible to recover for forensic analysis).
Since the substation RTUs (remote terminal units) are responsible for communicating with the MicroSCADA system, the MicroSCADA server probably forwarded these commands to them.
Security researchers believe these steps allowed the attackers to open circuit breakers in the substation and cause a blackout.
While there are many other fascinating details about this security incident, what’s essential for us is that an API was critical to the attack’s success.
What Could’ve Been Done Differently?
Some of the preventive measures would’ve been the following:
- Use an updated supported MicroSCADA version
- Do not allow external SCIL-API programs and unauthorized commands to run and execute in the MicroSCADA environment
- Enforce authentication
- Implement the principle of least privilege so that even if threat actors gain unauthorized access to the MicroSCADA system, they won’t have permission to execute files
It’s worth noting that an incident like this is not limited to obsolete MicroSCADA versions. With unprotected systems and APIs, threat actors can replicate attacks like this to exploit other SCADA systems, regardless of whether they rely on SCIL or another programming language.
How to Protect Utility APIs
We’re deeply aware of power and utility companies’ massive workload and the lengths they must go to ensure uninterrupted, quality service and regulation compliance. But somewhere along the way, they need to make room for cybersecurity, specifically API security. And not just any room, and not because we say so.
Examples such as the Sandworm-perpetrated blackout through a vulnerable API may look like distant threats to many utility companies. However, we must see them as a warning to take API security seriously and take preemptive action rather than cure the consequences of such cyberattacks. We don’t have to wait until the eleventh hour to act.
Power and utility companies must see API security as a priority to make timely adjustments to their digital systems and protect them as best as possible under their specific circumstances. Since this feat cannot be accomplished in a vacuum, and there’s no need to reinvent the wheel, they need to look at purpose-built API security solutions.
Why purpose-built? Because practice and authoritative security researchers/ethical hackers like Alissa Knight have shown that general-purpose web application security solutions like WAFs (web application firewalls) are, at best, insufficient and, at worst, utterly ineffective as API security mechanisms.
So, where can you look to find a suitable API security solution?
First, consider that no silver bullet will cover all your needs. Second, a thriving API security market is trying to address the pain points of organizations in different sectors, including utilities. Third, we can suggest one such solution.
Equixly in a Nutshell
Equixly is an AI-powered virtual ethical hacker covering two central API security areas: security testing and posture management.
Ethical hacking, that is, penetration testing, is an integral element of API security. Most of the vulnerabilities in APIs in the wild are discovered by none other than ethical hackers (and we’re fortunate that’s the case).
The “AI-powered virtual” part is the difference between human ethical hackers and Equixly. Equixly is an automated, AI-based API security solution. In other words, it’s a computer (loosely speaking) that takes full advantage of innovative technologies like artificial intelligence and machine learning. This aspect guarantees that it:
- Works efficiently
- Is adaptable
- Is cost-effective
- Has a short time to value
On the other hand, Equixly has internalized the operating principles of expert human hackers, like its creators, to ensure it approaches your APIs thoroughly with tested and proven methods and the creativity of hacking Jedis (as opposed to script kiddies).
Equixly works as both a production and a development security testing solution. Since its creators espouse the shift-left approach, Equixly is built to fit smoothly in your environment and work unobtrusively in pre-production, that is, SDLC (software development life cycle).
The AI-powered hacker supports your efforts to strengthen your API security posture in four ways:
- It looks for shadow and zombie APIs in your environment to help you build a comprehensive API inventory
- It tells you which API endpoints work with sensitive data so that you can do precise data classification
- It scans your APIs for the most common and severe API security risks according to OWASP (Open Worldwide Application Security Project) to help you manage vulnerabilities
- It generates reports that allow you to demonstrate compliance with regulations and security standards
Conclusion
The utilities sector is changing, and APIs play a unique role in this change.
However, as they bring massive benefits to companies and their customers, they can also bring massive security risks. If left unattended, APIs provide various entry points for threat actors to infiltrate deeply and wreak havoc on information systems. The Sandworm security incident clearly shows this danger.
Fortunately, the recent developments in API security have brought promising changes. Equixly is at the forefront of these developments. It’s the result of years of tackling concrete API security problems and hands-on experience in cybersecurity. It allows you to test your APIs in production and development and supports your posture management efforts.
Download Equixly’s Utilities Sector brochure:

Carlo De Micheli
Director of Product Marketing
Carlo is a versatile professional with extensive international experience. His enthusiasm for innovation extends across cybersecurity, automotive, and aerospace, where he actively engages in pioneering projects. Holding a technical background in aerospace engineering and supplementing it with independent studies in programming and security, Carlo has organized and presented at international conferences and established tech startups related to the sharing economy and fashion before embracing marketing and sales.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.