Equixly: On Board with Automation in API Pentesting
Carlo De Micheli, Zoran Gorgiev

“Ozark” is an interesting series. The protagonist inadvertently gets into trouble with malicious people by simply doing his job well. When he works out a solution to the initial problem, that leads to a new, bigger problem. He tries to solve the new problem, but the new solution leads to another problem.
This could’ve easily been a story about an API security professional. You know, a day in the life of Maria, the cybersecurity pro. Whatever she does to protect her APIs inadvertently leads to another problem as long as people are willing to exploit the imperfections in Maria’s solutions. And there will always be imperfections.
With a ubiquitous digital transformation largely reliant on APIs, we’ve reached a point where API security, to borrow an expression from others, is no longer a human-scale problem. There’s a yawning gap between what we can do to protect APIs and their number/size. We need help from machines, that is, automatons, that is, computers.
Getting on board with automation in API pentesting is one logical step to reducing this gap. And, as you’ll learn in the following sections, an AI-powered hacker such as Equixly can be an invaluable help in your efforts.
No, Really, Why Do I Need Automated Penetration Testing?
Automation already plays a substantial role in every sector. That’s for good reasons: speed, scale, and efficiency.
We’re not beating around the bush with these generic statements. They’re just a reminder of a broad tendency and its rationale.
In cybersecurity, we often talk about the abysmal lack of workforce and the enormous expansion of the attack surface. Too many tasks and too much of everything—problems, threats, risks—but too few people. So much to do in so little time.
With piles of challenges to respond to and so many of them being recurrent or humanly impossible to process, it’s hard not to appreciate what automation brings to the table. The sheer volume of data passing through our information systems alone is sufficient to delegate aspects of our job to computers, more precisely, intelligent software solutions.
API security is no different in this respect. In line with that, the need for automation applies to API penetration testing as well as API testing in general.
We won’t even discuss the importance of penetration testing for securing your APIs. We consider that evident since you can truly protect an API from hackers only if you adopt their mindset and see it the way they do.
APIs change, evolve, and scale quickly, and new threats, vulnerabilities, and risks occur as you read these words. Just yesterday (January 17, 2024), the ethical hacker Eaton Zveare published his latest discovery: a vulnerability found in the email-sending API of Toyota Tsusho Insurance Broker India. A leaky API response eventually exposed 657k emails with customer information like insurance policy PDFs, OTPs, and more.
At the frequency rate of penetration testing, say, once a year, keeping up with all the API changes and lurking dangers is next to impossible.
No matter the virtues of manual API penetration testing, automated pentesting is becoming a necessity. Based on research, we calculated that an expert pentester needs 154 hours to test only 40% of an API with 40 endpoints. That’s six and a half days for testing less than half of your API. That’s a lot of time.
Let’s put aside the impact that the pentester’s expertise level will inevitably have on the testing results. Even with this variable not factored in, can you imagine how costly manual penetration testing would be, both in time and money, if you did it as often as necessary? For instance, after every significant change in your API or upon discovering a zero-day in the wild?
One way or another, you’ll have to pentest your APIs. When that’s a given, why not make pentesting more convenient, economical, rapid, and manageable?
Equixly in a Nutshell
Equixly is an AI-powered hacker—an automated API (pen)testing solution you can run at regular intervals or whenever circumstances require. It’s built with the shift-left approach in mind, so it’s at home in SDLC (software development life cycle) as well as in your production environment.
A proprietary AI, more precisely, reinforcement learning algorithm, powers Equixly, allowing it to make inferences about unpredictable environments based on its interaction with them and how they respond. This capability helps it discover zero-days in addition to already known vulnerabilities.
Speaking of known vulnerabilities, Equixly covers the entire spectrum of OWASP’s top 10 API security risks. It’s worth noting that it’s developed to be particularly effective in detecting business logic vulnerabilities.
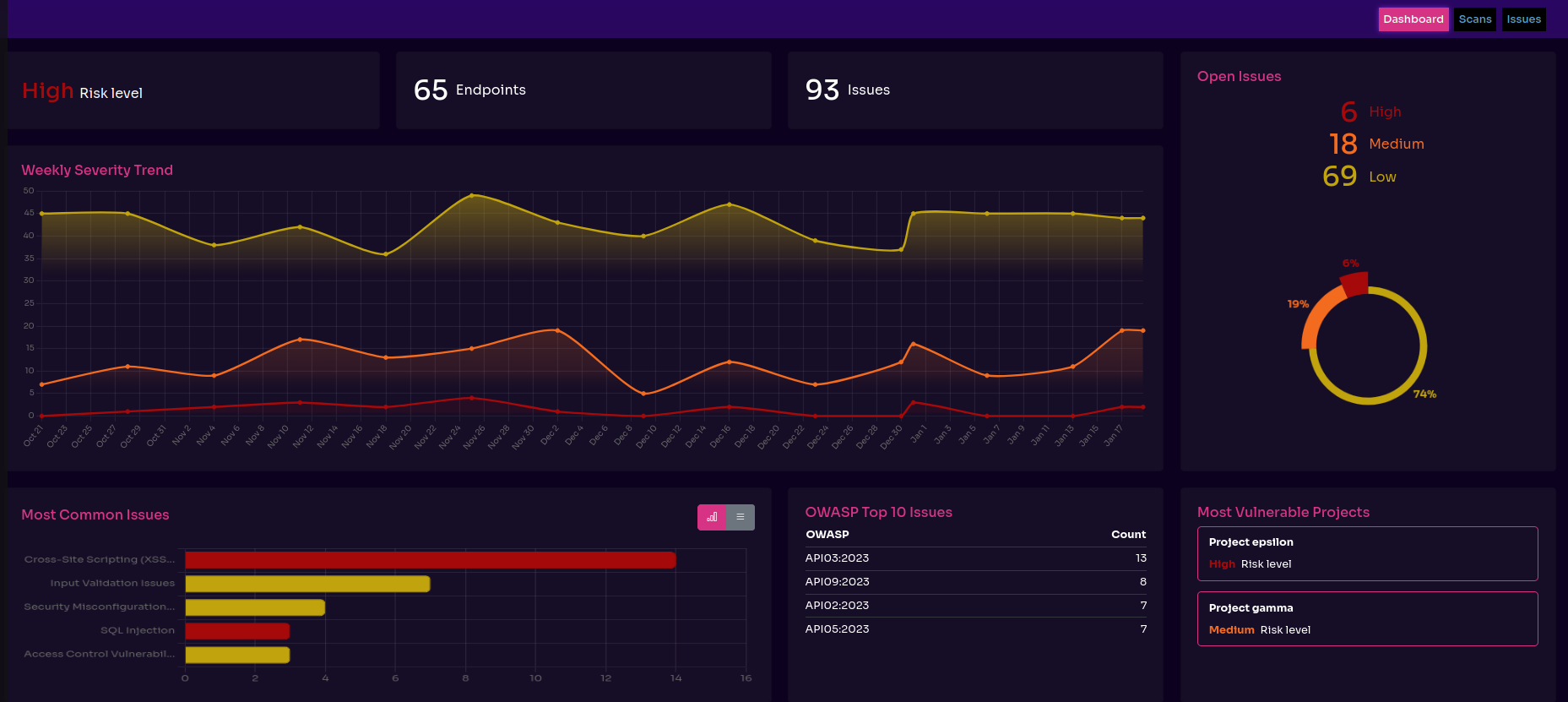
Equixly: Onboarding and Deployment
Cumbersome onboarding is more than just a nuisance. It smells of a clunky testing process done by unwieldy software.
Accordingly, as essential as the other functionalities are, we’ll focus exclusively on the processes of onboarding and deploying your API in Equixly for security testing. In other words, you’ll see how convenient it is to begin testing your APIs with this AI-powered hacker.
Equixly the SaaS Solution
Equixly is a SaaS solution running in the cloud. This type of software is known for being easy to start with and cost-effective, and Equixly is no exception.
A SaaS such as Equixly has a short time to value—the time it takes for customers to benefit from investing in the software. In addition, it’s easy to use, so you can employ it without much effort and quickly see how well it fits into your environment and security stack.
When you start with Equixly, you don’t need to configure anything in particular, nor should you take care of maintenance (updates and upgrades).
Also, Equixly being cloud-based means it’s readily scalable, which implies it’s a sound long-term solution.
Gray Box and Black Box Testing
Equixly follows the same logical mode of working as an ethical hacker (which is why we keep saying it’s a hacker). By that, we mean attacking and probing your APIs to find bugs, flaws, and risky business flows, but not just in any way.
A good penetration test aims to map out the threats to a specific API. Therefore, a pentester must approach this API methodically to attack it and, by extension, test it successfully.
The same principles apply to Equixly. Typically, it carries out gray box testing, and it does that the same way a human pentester would.
In gray box penetration testing, the API provider usually allows the pentester to bypass some security controls. The pentester gets specific information about the company and its API—such as which endpoints to target and which to exclude from testing—and could be provided access to API documentation and a user account.
Similarly, to test your API, Equixly requires only the following information:
- API’s base URL, regardless of whether it’s a production or staging URL
- JSON or YAML API definition file, i.e., OAS (OpenAPI Specification) file that gives Equixly the structure of your API as well as the parameter, request, and response definitions
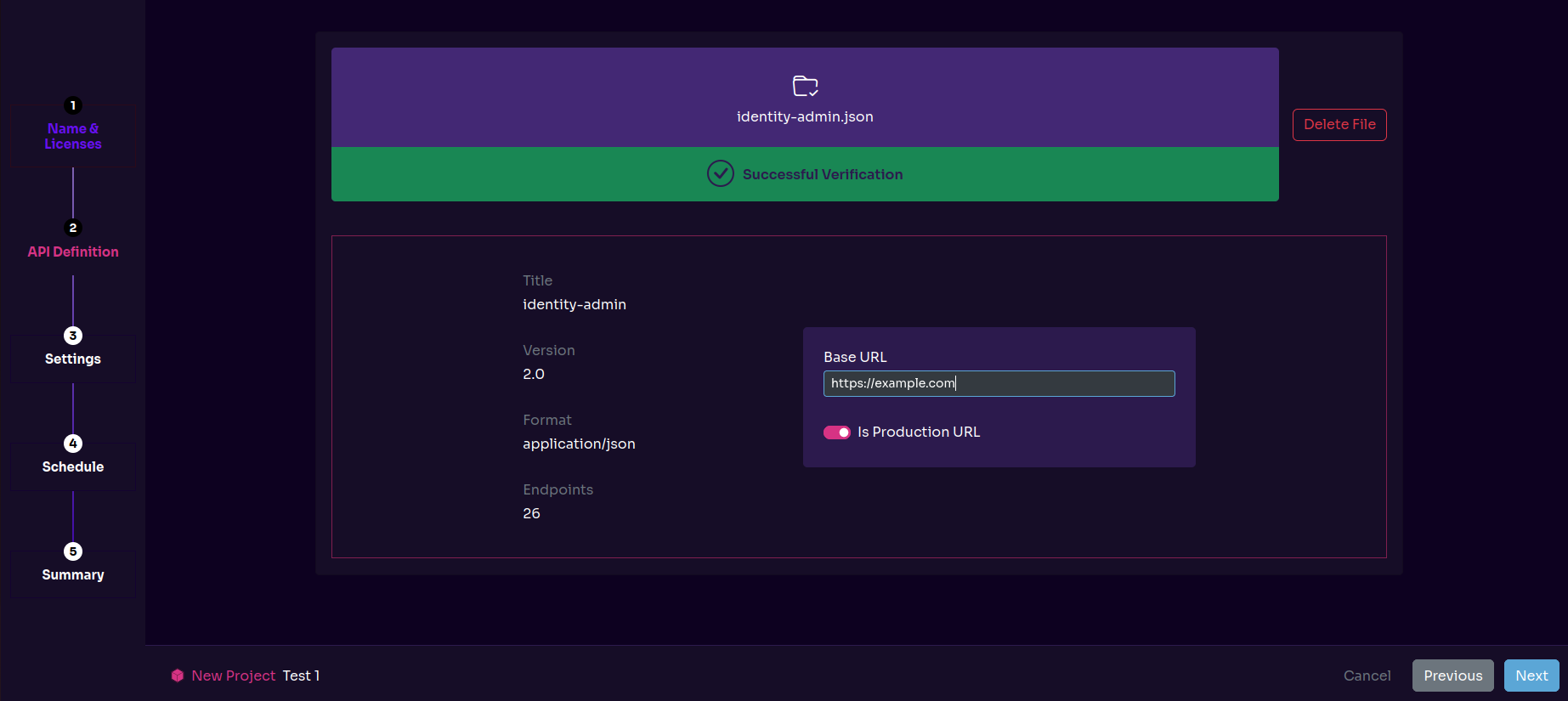
Optionally, you can provide:
- Authentication information, that is, the type of authentication—for example, JWT, basic authentication, or API key—and the appropriate token/credentials that define Equixly’s access privileges and allow the AI-powered hacker to interact with your API in the defined way
- Dictionary of API parameters (keys) and their values if you want specific parameters to have default values for testing purposes
- Excluded API paths and endpoints, that is, paths and endpoints that are out of scope for testing
You start a new project in Equixly, provide this information to the AI-powered hacker, schedule the date and frequency of the tests (one shot, weekly, or less frequently), and you’re good to go. The duration of the entire process can be measured in minutes.
In addition, Equixly can perform black box testing, but the coverage is limited in that case. That is, unless the tested API has an authentication vulnerability that lets the AI-powered hacker bypass the limitations imposed by a black box testing scenario. As a reminder, in black box testing, the pentester knows virtually nothing about the company and its API.
Conclusion
The current conditions in cyberspace are changing our overall approach to API security. Penetration testing is an integral part of API security. Hence, the new conditions dictate a shift in how we do API pentesting.
The merits of manual penetration testing are undeniable. However, manual penetration testing is contingent on scarce qualities, such as the pentester’s expertise, and is time-consuming. It’s high time to catch up with the pace of the evolving cyber threat landscape and include automation in API pentesting.
Equixly is an AI-powered hacker developed by ethical hackers. It helps you test your API in development and production. And it performs gray box and black box testing following the same tested and proven approach as manual pentesting.
Enroll for a personalized demonstration of Equixly to experience the convenience of automated API penetration testing in action.

Carlo De Micheli
Director of Product Marketing
Carlo is a versatile professional with extensive international experience. His enthusiasm for innovation extends across cybersecurity, automotive, and aerospace, where he actively engages in pioneering projects. Holding a technical background in aerospace engineering and supplementing it with independent studies in programming and security, Carlo has organized and presented at international conferences and established tech startups related to the sharing economy and fashion before embracing marketing and sales.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.