Introducing Equixly: The Future of API Security
Alessio Dalla Piazza, Simone Businaro

Introducing Equixly: The Future of API Security
Preface
In the current age of digital transformation, APIs have emerged as the key components of connectivity and innovations. However, with this importance comes an increased vulnerability to cyberattacks. Traditional security measures are not sufficient to handle the dynamic nature of modern APIs, particularly when it comes to scaling security measures alongside application growth. Indeed, while preventive solutions such as WAFs play a pivotal role in protecting against a range of threats, they primarily focus on generic attack patterns and previously known vulnerabilities. This leaves them largely ineffective against business logic attacks, which exploit the expected behavior of an application rather than its technical flaws. Given the widespread nature of contemporary API ecosystems, a mere identification of entry points is no longer adequate. What’s essential is a deep dive into the intricacies of business logic, the nuances of data flow, and the identification of concealed vulnerabilities.
Enter Equixly. Born out of a recognized need to address the mentioned challenges, our mission is clear: revolutionize the API security landscape. Equixly is not just another security platform, but rather a transformative solution tailored for the modern software development lifecycle (SDLC). We envisioned a platform where API security testing seamlessly integrates within the SDLC, allowing for proactive flaw detection and bug fixing-related effective cost management.
What further elevates Equixly above its contemporaries is its pioneering utilization of cutting-edge machine learning. With the foundation built upon vast datasets from numerous security tests, our ML algorithm is poised to automate API attacks, delivering near real-time results. Developers are no longer left in reactive modes; they are equipped with proactive remediation strategies. For the CISOs, this translates to a security framework that is not just robust but anticipatory. For CTOs? They witness optimal resource distribution, ensuring both infrastructural resilience and a impressive line of defence against cyber threats.
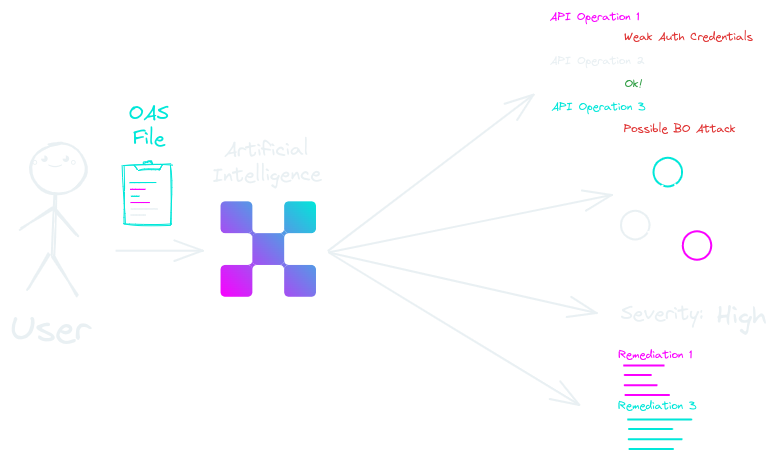
Deep Dive
The challenges to optimal API security are not solely rooted in technology–they are profoundly human. Delving into API penetration testing unveils a dual dilemma: the escalating human resource expenditure and a glaring tooling deficiency. These intertwined challenges amplify the vulnerabilities, demanding a revolutionary approach to bridge the divide.
Exploring the Human Gap in API Security
API security is paramount in the digital age, and while technology surges ahead, it is the human factor that often determines its effectiveness. Manual API penetration testing, though valuable, confronts a series of challenges rooted in human built-in limitations:
- Time Consumption: One of the most significant human costs associated with API penetration testing is time. Even when conducted by the most seasoned professionals, manual testing procedures can be slow. APIs, especially those powering complex applications, can have numerous endpoints, each with specific functionalities and potential vulnerabilities. Thoroughly testing each one requires meticulous effort and considerable time.
- Skill Set Shortage: Effective API penetration testing requires niche expertise. Not all security professionals can boast this specialized skill set, leading to a talent scarcity and added training costs.
- Scaling Issues: As the API landscape of an organization expands, the human resources needed to secure them escalates, often at unsustainable rates. This presents a considerable challenge for organizations that aims at maintaining a consistent security posture without continuous assessment.
- Human Error: Inherently, humans are prone to mistakes. Whether it’s overlooking a minor detail, misunderstanding a certain API behavior, or simply having an off-day, these oversights can leave critical vulnerabilities unchecked.
- Test Recurrence: To ensure an unbreachable API front, regular penetration tests are essential, especially post-updates. Yet, mobilizing a skilled team for frequent evaluations is resource-intensive and often unfeasible.
Exploring the Tooling Gap in API Security
The domain of API security is continuously faced with emerging challenges. Despite the abundance of tools available in the market, there is still a clear mismatch between these tools and the specific needs of API security.
- One-Size-Fits-All Dilemma: The market is awash with overarching security solutions. However, the peculiarities of API security often get overshadowed. These generalist tools, while useful in broader contexts, are ill-equipped to pinpoint API-specific vulnerabilities, leaving critical gaps exposed.
- Overlooking Sequence Intricacies: Contemporary APIs often demand intricate call sequences to mirror particular user actions or operational processes. Yet, many of today’s tool exhibit a shortfall in grasping this layered complexity, resulting in potential security oversights.
- Basic Data Entry: While automated tools, like Spiders, tend to use basic default inputs, real-world user interactions encompass a vast array of data inputs. This variance can unveil unexpected vulnerabilities. For instance, while a spider might input a random string into a registration form requiring a valid email, a user might input a correctly formatted email, leading to a different application response and potentially revealing deeper security pitfalls.
- Patchy Remediation Insights: Uncovering vulnerabilities is a step in the right direction, but true security lies in timely and effective remediation. Nevertheless, many tools fall short, offering vague or insufficient insights for developers, making the path to patching vulnerabilities complex and uncertain.
How Equixly Makes the Difference
APIs demand a nuanced touch, not flooding the system with requests but knowing which requests to send, their precise sequence, and the correct parameters.
In the maze of API complexities, conventional tools often lose their way, inputting arbitrary data and bypassing the subtle intricacies of each API parameter. This results in a superficial overview that misses the intricate, deeper behaviors of the API.
APIs are not mere data channels. They are dynamic entities where:
- Multiple requests can access the same data point.
- Parameters nest and overlap, adding layers of complexity.
- The meanings behind API requests can blur, given wrong, sparse, or ambiguous documentation.
While traditional tools might skim the surface of RESTful APIs, Equixly dives deep. Through advanced natural language processing techniques, we discern the hidden connections, linking query arguments to their relevant object fields. This process of leveraging augmented introspection creates a more insightful roadmap for subsequent analyses.
Enter Equixly’s ‘Oracle’: a guiding light in the foggy API landscape. Acting as a dynamic compass, the Oracle continually fine-tunes request suggestions based on real-time feedback, pinpointing potential vulnerabilities.
Navigating APIs isn’t about traversing every possible route. It’s about identifying the most illuminating paths. Equixly’s proprietary algorithm efficiently prunes redundant requests, focusing on the most valuable probes for in-depth insight.
Equixly doesn’t chase volume—it seeks value. This approach amplifies the depth of API exploration, offering a holistic understanding with surgical precision.
In the grand chessboard of API security, Equixly thinks several moves ahead. Not just adapting, but anticipating. As API threats evolve, Equixly stands at the vanguard, ensuring your defenses are not just robust, but agile and future-proofed.
Equixly by the Numbers: A Statistical Insight
API testing is no minor task. It is an intricate process that is vital to ensuring robust security and seamless integration in the digital world. To better understand the depth required, let’s consider a scenario with a small to medium-sized API application that has 40 endpoints.
The testing process typically involves:
- Annotating Endpoints
Based on research and experience presented in USENIX publications, an expert penetration tester typically takes about 1 minute to understand and categorize each endpoint.
- Calculation:
40 endpoints × 1 minute/endpoint = 40 minutes
- Mapping Edges for Inputs/Outputs
Drawing from the analysis of over 2,000 public API specifications, we observed that each endpoint typically consists of an average of 5 input elements and 5 output elements. On average, an expert requires about 1 minute to map an edge for an input or output. Therefore, for 5 inputs and 5 outputs across 40 endpoints, the estimated time is 400 minutes.
- Calculation:
40 endpoints × 10 (5 inputs + 5 outputs) × 1 minute = 400 minutes
- Sequence Identification: Determining the correct sequence of operations
Sequences exhibit a spectrum of complexity. Straightforward sequences can often be delineated in roughly 2 minutes, while more intricate ones may demand over 60 minutes (let us assume an average of 31 minutes). The complexity of a sequence is influenced by the interplay of Functional Dependencies, Business Logic Workflows, and associated Edge Cases. Public data further suggests that longer sequences tend to harbor more bugs and generally take longer to be built when compared to shorter sequences.
As an example:

Considering the primary sequence of “1. Register -> “2. Login” -> “3. Browse Product”, once a user has browsed a product, a range of subsequent actions can evolve:
- Add the product to the cart
- View product details
- Add the product to a wishlist
- Write a review or rating for the product
- Share the product
- View related products
- Search for other products … among other potential actions.
For a quick calculation:
- After the operation “Browse Product”, assume there are 10 potential actions a user might initiate.
- Subsequent to those, for each action, consider another 5 possible actions.
- Following those, consider 3 more possible actions for each.
The sequences branching from “3. Browse Product” can then be calculated as:
Sequences = 10 (first-level actions) + 10 x 5 (second-level actions) + 10 x 5 x 3 (third-level actions)
Resulting in: Sequences = 10 + 50 + 150 = 210
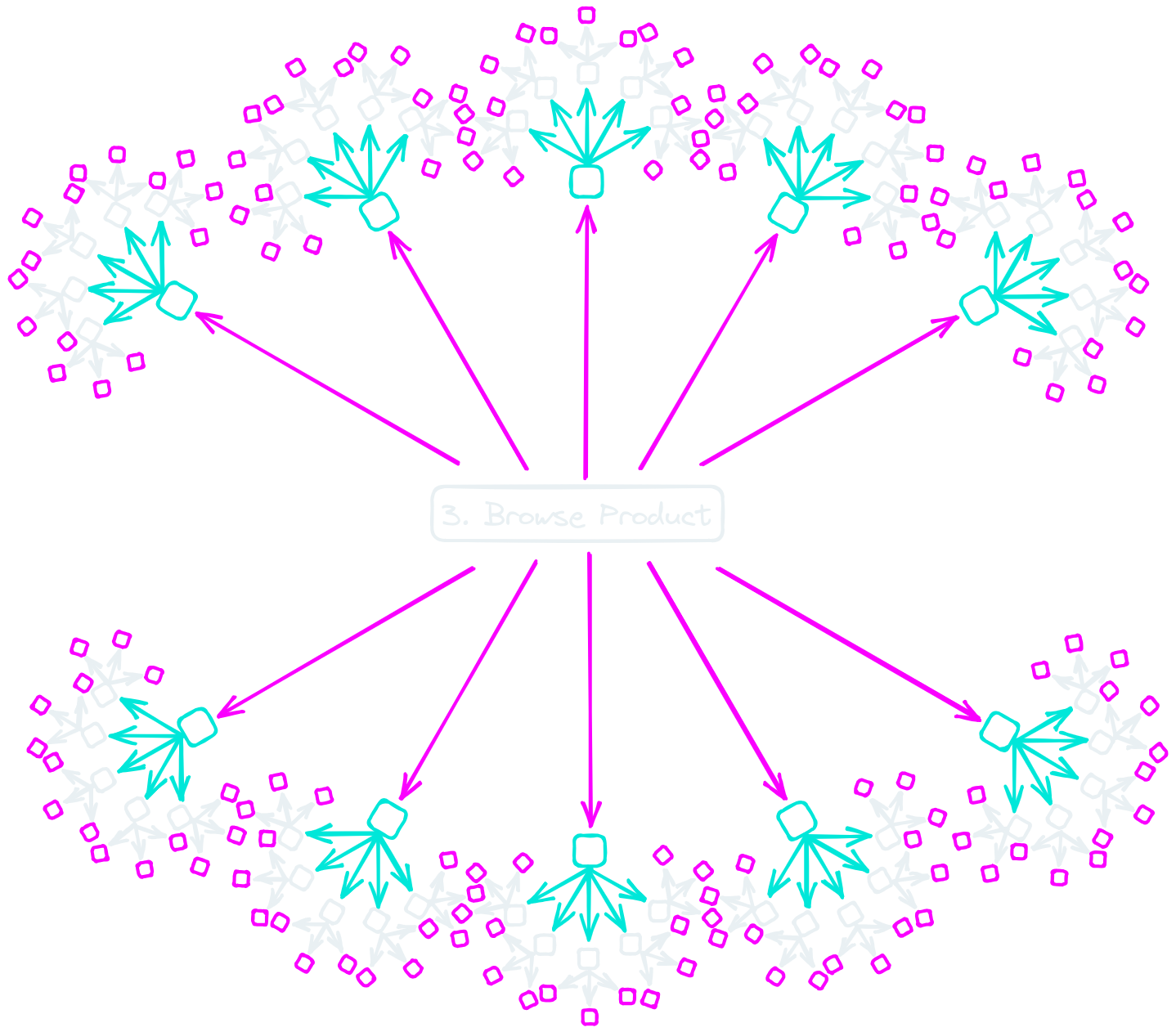
Extrapolating this to the entire API (assuming “Browse Product” typifies endpoint complexity), with 40 primary endpoints, we get:
40 endpoints x 210 sequences/endpoint = 8,400 sequences
Hence, for an API featuring 40 endpoints, where following a prime action there exist 10 potential secondary actions, 5 tertiary actions thereafter, and then 3 quaternary actions, approximately 8,400 user action sequences might be created.
Remember, the average time used is 31 minutes, as mentioned above.
For simplification, let’s assume we test only a representative 0.5% of these sequences (based on critical user flows) and operation order.
0.5% of 8,400 sequences = 42 sequences
42 sequences at 31 minutes each = 1302 minutes or roughly 21 hours.
- Data Manipulation: Adjusting or tampering data to match specific testing scenarios
Each input parameter can be a potential vulnerability gateway. If an expert penetration tester evaluates 10 different vulnerabilities for each injectable input and spends an average of 10 minutes per value, the total time for this activity becomes significant.
-
Calculation:
- 10 checks × 10 minutes/check = 100 minutes for one input
- 100 minutes/input × 2 inputs = 200 minutes for both inputs for one endpoint
- 200 minutes/endpoint × 40 endpoints = 8000 minutes or 133 hours
Adding up the sequence identification and data manipulation times: 21 hours (for sequences) + 133 hours (for data manipulation) = 154 hours.
Factoring in all the activities, an expert would need 154 hours to test an API with 40 endpoints. Interestingly, this does not account for every input. About 60% of the inputs remain untested in this scenario and only a small combination of sequence where created, posing potential unchecked vulnerabilities.
- Calculation for untested inputs:
(5 total inputs - 2 tested inputs) / 5 total inputs × 100 = 60%
Conclusion
In today’s interconnected world, security threats constantly shift, challenging businesses to keep up with thorough API system testing. Consider a typical API system – our studies revealed it takes over 154 hours to test 40% of it. With each added feature, testing time expands. Within hours, Equixly achieves what traditionally took days with near-real-time reporting.
Equixly is revolutionizing the security testing paradigm. For penetration testers, Equixly is a trusted aide, automating time-consuming tasks and enabling them to focus on critical human-led interventions. As machine learning algorithms identify vulnerabilities, the future of penetration testing will be centered on exploiting these findings rather than tedious sequence tests. For developers, Equixly operates as an unobtrusive security auditor, ensuring system robustness. And for leadership roles like CISOs and CTOs, Equixly presents a holistic snapshot of security health and potential vulnerabilities.
Concisely, Equixly doesn’t just speed up the testing process; it redefines what’s possible in security, turning exhaustive days into efficient hours and fortifying defenses like never before.

Alessio Dalla Piazza
CTO & FOUNDER
Former Founder & CTO of CYS4, he embarked on active digital surveillance work in 2014, collaborating with global and local law enforcement to combat terrorism and organized crime. He designed and utilized advanced eavesdropping technologies, identifying Zero-days in products like Skype, VMware, Safari, Docker, and IBM WebSphere. In June 2016, he transitioned to a research role at an international firm, where he crafted tools for automated offensive security and vulnerability detection. He discovered multiple vulnerabilities that, if exploited, would grant complete control. His expertise served the banking, insurance, and industrial sectors through Red Team operations, Incident Management, and Advanced Training, enhancing client security.

Simone Businaro
Head of Solution Architecture
Simone is a seasoned Cloud and Solution Architect with extensive experience in leading transformation projects for major enterprise customers such as UniCredit and Generali. He specializes in Private and Public Cloud adoption, as well as designing Cloud Native platforms including Kubernetes and OpenShift. He is adept at crafting comprehensive automation solutions that seamlessly integrate service lifecycle with customers' internal ITIL and financial processes, ensuring streamlined, efficient, and scalable solutions.