Adversarial testing: Why attacking APIs at scale is the best defense against real-world attacks
If you look up ‘adversarial testing’ today, you’ll find that generative AI has almost entirely captured the narrative. The digital conversation is so heavily skewed toward AI safety that it’s easy to forget where the concept comes from. To a casual observer, it might look like adversarial testing is a niche subset of large language model security.
But long before researchers conceived and introduced the first transformer architecture, the pioneers of computer science recognized that a system’s posture remains a theoretical construct until an adversarial mind(set) attempts to dismantle it.
Adversarial testing is the method of offensive security — a goal-oriented undermining of IT systems with security as the final objective. As such, it does apply to artificial intelligence / large language model systems but extends well beyond them.
As organizations move resolutely toward API-first architectures in software development and incorporate the Model Context Protocol (MCP) into AI system deployments, the need for scaled adversarial testing is becoming more of a baseline requirement for survival rather than a nice-to-have security practice.
Look beyond the frontend: APIs as the universal nervous systems of modern software
To understand the modern attack surface, you must look beyond the GUI.
The frontend in web apps today is typically a minimal layer that handles user input and displays data. The complex processing and, extremely importantly, application logic are delegated to backend systems via APIs. Consequently, it won’t be an exaggeration to say that APIs underpin the modern web application ecosystem:
- APIs make it possible for systems, services, and components to communicate with each other, which is especially important in distributed architectures such as microservices, where each service may be independent but still needs to exchange data with others.
- APIs enable integration with third-party services, platforms, and applications, allowing web apps to incorporate social media platforms, payment gateways, cloud storage, and other external services.
- APIs allow systems to scale efficiently and enable developers to build modular, reusable components.
- APIs are the enforcement surface where identity, authority, and business logic are exposed in modern architectures.
Modern web apps are essentially aggregators of API responses. When you load a dashboard, your browser might make 50 distinct API calls to 20 different microservices — one for user profile, another for inventory, another for payment processing, another for analytics, etc.
But APIs’ pivotal role doesn’t end with web applications:
- APIs are the mainstay of mobile apps, allowing them to request and receive data from servers or databases.
- APIs are crucial in the Internet of Things (IoT), enabling communication between smart devices, sensors, and backend systems for remote control and data exchange.
- APIs are essential for artificial intelligence, machine learning, and large language models, allowing them to expose capabilities such as natural language processing, image recognition, text generation, and predictive analytics to applications.
- APIs are crucial for automated systems and robotics, enabling communication across industries like manufacturing and logistics for tasks like predictive maintenance, inventory management, and process automation.
- APIs are critical in cloud computing for managing distributed resources, interacting with machine learning services, storage, computing, and networking, and enabling scalable infrastructure.
- APIs are integral to blockchain, enabling decentralized applications to interact with blockchain networks for tasks like cryptocurrency transactions, smart contract execution, and data verification.
With APIs now playing such an integral role within IT environments, the security perimeter is much more porous: each API endpoint is a possible entry point into the core business logic.
The birth of offensive security and the Tiger Team legacy
The lineage of adversarial testing goes back at least to the early 1970s.
In 1972, James P. Anderson published the seminal “Computer Security Technology Planning Study” for the US Air Force. This study introduced the concept of the ‘malicious user,’ helping to establish the need for an offensive perspective in security.
Anderson understood that effective security comes from actively trying to break systems, as well as building them to function well, to find vulnerabilities before malicious actors do. That laid the groundwork for penetration testing, red teaming, and adversarial testing.
This conceptual framework led to the formation of Tiger Teams. These were groups of elite researchers whose goal was to find flaws in the most secure systems of the era, most notably the Multics operating system (Karger & Schell, 2002).
The 1974 paper by Paul A. Karger and Roger R. Schell, “Multics Security Evaluation: Vulnerability Analysis,” documented the first systematic penetration exercises. Security evaluation teams simulated, or better, emulated the actions of a creative and persistent adversary to subvert system kernels.
They demonstrated that an apparently secure system would not deter hackers who understood the underlying rules as well as, or even better than, the architects from compromising it.
The scaling asymmetry in cybersecurity
The cybersecurity industry has been facing a concerning workforce shortage for some time now. There are indications that this predicament is particularly pronounced in the adversarial testing context, with a severe lack of pentesters, red teamers, and bug bounty hunters.
As if that was not concerning enough, the volume and momentum of threats keep rising, now facilitated by developments in AI, as the Fortinet 2025 Global Threat Landscape Report suggests.
Consider this formula:
Tᵢ = (Nₜ · (Aᵤ + AI)) / (W꜀ · Rₜ)
Where:
Tᵢ(Number of Threats): The sheer volume of threats organizations face.Aᵤ + AI(Automation + Artificial Intelligence): The increasing role of automation and AI in making threats faster, more scalable, and more persistent.W꜀(Human Workforce Capacity): The limited number of skilled cybersecurity professionals available to address these threats.Rₜ(Security Response Time): The speed at which human teams can detect, analyze, and mitigate threats.
Imagine answering this “Mount Doom” security challenge depending primarily on the restricted resources in the workforce, skills, time, and budget at your disposal. Of course, these vary from organization to organization.
But the general sentiment is that there’s an extreme asymmetry between the mounting security risk and the options available to human security teams. It’s like bringing a knife to a gun fight.
Besides, human-led adversarial testing — as indispensable as it is for its deep, creative insights — is a “point-in-time” assessment. A human team might test an API once a year.
However, the code they test changes every few hours via CI/CD pipelines. Accordingly, a human tester who visits once every 12 months or even quarterly is, statistically, we dare say, insignificant compared to an adversary who uses AI-fueled automation to probe your infrastructure 24/7/365.
This extreme asymmetry in scaling simply calls for an offensive capability that matches the adversary’s. Scaled adversarial testing is a continuous, autonomous, AI-assisted process that you can shift left and integrate as early as possible into the SDLC, as well as in the production environment.
Why scaled attack works as the best defense
The argument for attacking your own APIs at scale rests on, at a minimum, three factual pillars of security logic:
- Logical exhaustion: Modern attacks target predominantly logic vulnerabilities, such as BOLA is unique to every application, you can discover and address logic flaws effectively only through systematic, adversarial analysis of every possible state change in the API. And this is where AI, trained specifically for adversarial testing, becomes indispensable.
- Contextual awareness: Attacks at scale enable a system to learn an API’s behavioral norms. Given the speed and scale at which an AI model (or ML model) typically operates, an adversarial AI engine is more than equipped to identify an edge case — that one-in-a-million parameter combination — that leads to a potential compromise.
- Feedback loop: Security is a race of information. Attacking at scale and continuously enables you to generate a constant stream of threat intelligence that reflects the factual state of your codebase and its implemented logic. That, in turn, makes it possible to find and, by extension, remediate security vulnerabilities before an external actor discovers those vulnerable endpoints or inadvertently skewed API workflows.
The ‘Agentic AI Hacker’
Equixly offers a scaled adversarial testing solution in its Agentic AI Hacker. It is a system of autonomous agents built on proprietary reinforcement learning algorithms that emulate the reasoning and persistence of an AI-assisted human adversary.
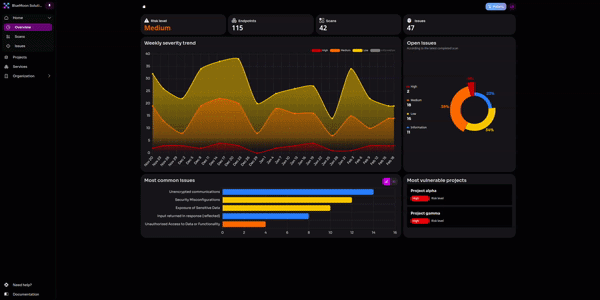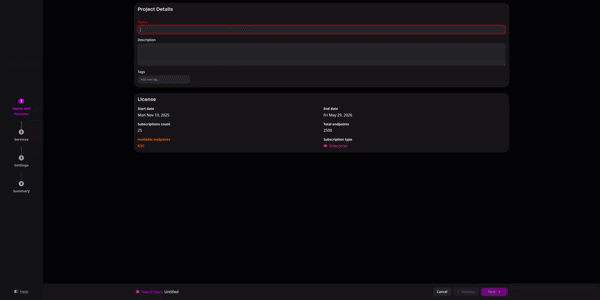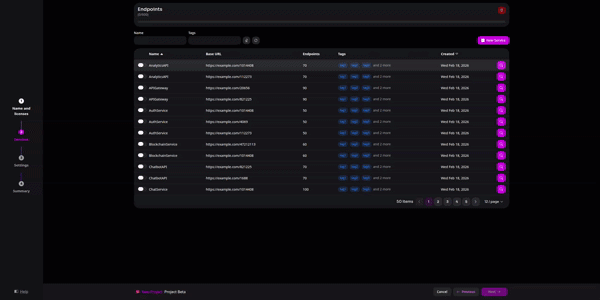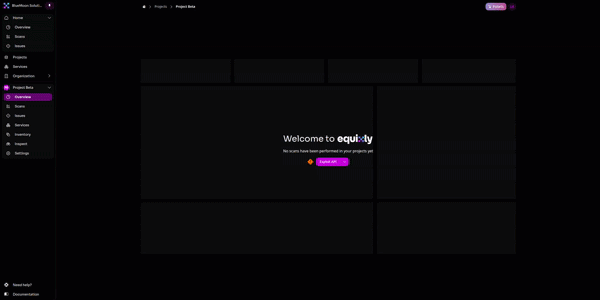
How does the Agentic AI Hacker work?
The Agentic AI Hacker performs reconstructive analysis:
- Scrutinizes API behavior
- Maps data flows
- Infers underlying logic
- Launches targeted attack emulations, which are multi-step sequences based on observations from the first three steps
The purpose is to discover weaknesses that allow authentication bypass, unauthorized access, privilege escalation, data exfiltration, and similar compromises, but without causing material damage to your systems. Instead, the Agentic AI Hacker presents the discoveries from its adversarial testing endeavors in reports that contain:
- Identified security vulnerabilities
- Summarized as well as detailed vulnerability explanations
- Affected API endpoints
- Technical PoC demonstrations
- Straightforward remediation guidelines
Evaluating the Agentic AI Hacker in practice
Equixly’s AI Hacker has demonstrated exceptional effectiveness and efficiency in multiple empirical security evaluations and performance benchmarks:
- Pentesters vs. the Agentic AI Hacker:
- 15 human testers solved 14 out of 30 challenges in over 2 hours, performing well mostly on easier tasks, such as basic SQL injection.
- The Agentic AI Hacker identified 230 vulnerabilities in 1 hour, covering all 30 challenges, demonstrating much higher coverage and speed.
- ZAP-based DASTs vs. the Agentic AI Hacker
- The AI Hacker discovered 80% more security issues than traditional ZAP-based DAST solutions.
- 8 high-severity vulnerabilities found by it were not detected by the DAST engines at all.
- The DASTs failed to detect critical logic vulnerabilities.
- The Agentic AI Hacker finds a 0-day
- During routine API security testing, the AI Hacker discovered CVE-2026-0773, a critical RCE zero-day vulnerability
- This 0-day has a CVSS of 9.8.
- The AI Hacker discovers vulnerabilities in popular MCP servers
- 43% of the tested popular MCP server implementations had command injection vulnerabilities
- 30% had SSRF issues
- 22% suffered from path traversal vulnerabilities.
Final thoughts
As counterintuitive as it sounds, adversarial testing was conceived and established as a primary mechanism for cyber defense. The legacy of the 1970s Tiger Teams was the realization that defense is incomplete without offense.
In 2026, with APIs underpinning everything in the digital realm, from web apps to IoT to LLM systems, the scale of the threat has changed. But the need for adversarial testing has remained the same. The only new requirement is scale. Organizations need a powerful, scalable hacker who never sleeps to find the cracks in their API-supported software before the adversary does.
We deliver expert-level automated AI penetration testing, the kind that previously required your most senior, most expensive consultants. Our platform matches the depth and rigor of a seasoned pentester at a fraction of the time and is infinitely repeatable.
The only scenarios we don’t optimize for are those requiring a top 1% specialist spending days on bespoke research. Everything else, the testing that actually impacts your risk posture, we handle automatically.
If we revisit the calculation from the earlier section, we can reduce the threat index as follows:
Tᵢ = (Nₜ · (Aᵤ + AI)) / (W꜀ · Rₜ · Eₐ)
Where Eₐ is ‘Efficiency gained from automated AI pentesting‘
** Our customers have reported an 80% improvement in the Threat Index through the application of Equixly’s scaled adversarial testing approach.
Defense starts with offense. Reach out to experience the Agentic AI Hacker in action.
FAQs
Is adversarial testing used only for identifying vulnerabilities in an AI model?
No, adversarial testing is a security methodology that applies to all IT systems, including APIs, networks, and web applications, by adopting an attacker’s mindset to find logical and technical flaws.
Why is testing APIs at scale more effective than traditional point-in-time penetration testing?
Since modern software is updated continuously via CI/CD pipelines, only automated, high-volume adversarial testing can keep pace with these changes and match the persistence and speed of real-world attackers who probe infrastructure around the clock.
How does the Agentic AI Hacker differ from a standard automated vulnerability scanner?
The Agentic AI Hacker uses autonomous reasoning and reinforcement learning to reconstruct an application’s unique business logic and execute multi-step adversarial attack simulations, which is a capacity absent from traditional scanners.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.