API governance: Where Equixly delivers value and why it matters now
Zoran Gorgiev, Alessio Dalla Piazza

API governance remains an outlier in the modern enterprise. Recent research shows that only 14% of organizations have moved beyond ad hoc security measures to implement a dedicated governance framework.
In parallel, there is a pronounced gap between policies defined on paper and their practical execution. Even where standards exist, the production environment is often a fragmented reality of sprawling estates, undocumented (shadow) endpoints, and inconsistent controls.
To bridge this gap, the industry is currently moving from a simpler API management to a more mature API security governance model revolving around risk and integrity. This article examines how Equixly delivers strategic value within this current trend.
You will learn how, by making the most of a proprietary agentic AI model and the principles of adversarial testing, the platform helps you to validate the execution of security policies continuously against:
-
Authoritative security frameworks, such as OWASP API Security Top 10, ASVS 5.0.0, and OWASP Top 10 for LLM Applications
-
Existing regulatory and compliance demands, including:
Direct support:
General support:
-
Emerging API security frameworks / potential compliance requirements like NIST SP 800-228.
The case for enterprise API governance
API governance is the set of policies, processes, and standards you ought to define and follow to design, build, deploy, and manage APIs that are consistent, secure, compliant, and aligned with your organization’s goals.
Several converging factors have aligned to turn API risk from a niche technical problem to a vital boardroom-level concern. They send strong signals that robust API governance programs are necessary at the enterprise level.
What are those converging factors?
1. The API sprawl
Microservices and cloud-native architectures led to a massive, largely uncontrolled increase in APIs.
An organization can now have hundreds or thousands of API endpoints that span different environments, each with its own asset owner. This state easily leads to redundant development efforts, accumulated operational costs, and technical debt.
On top of that, API sprawl gives birth to undocumented or shadow APIs—endpoints that exist outside the knowledge or control of the IT or security teams.
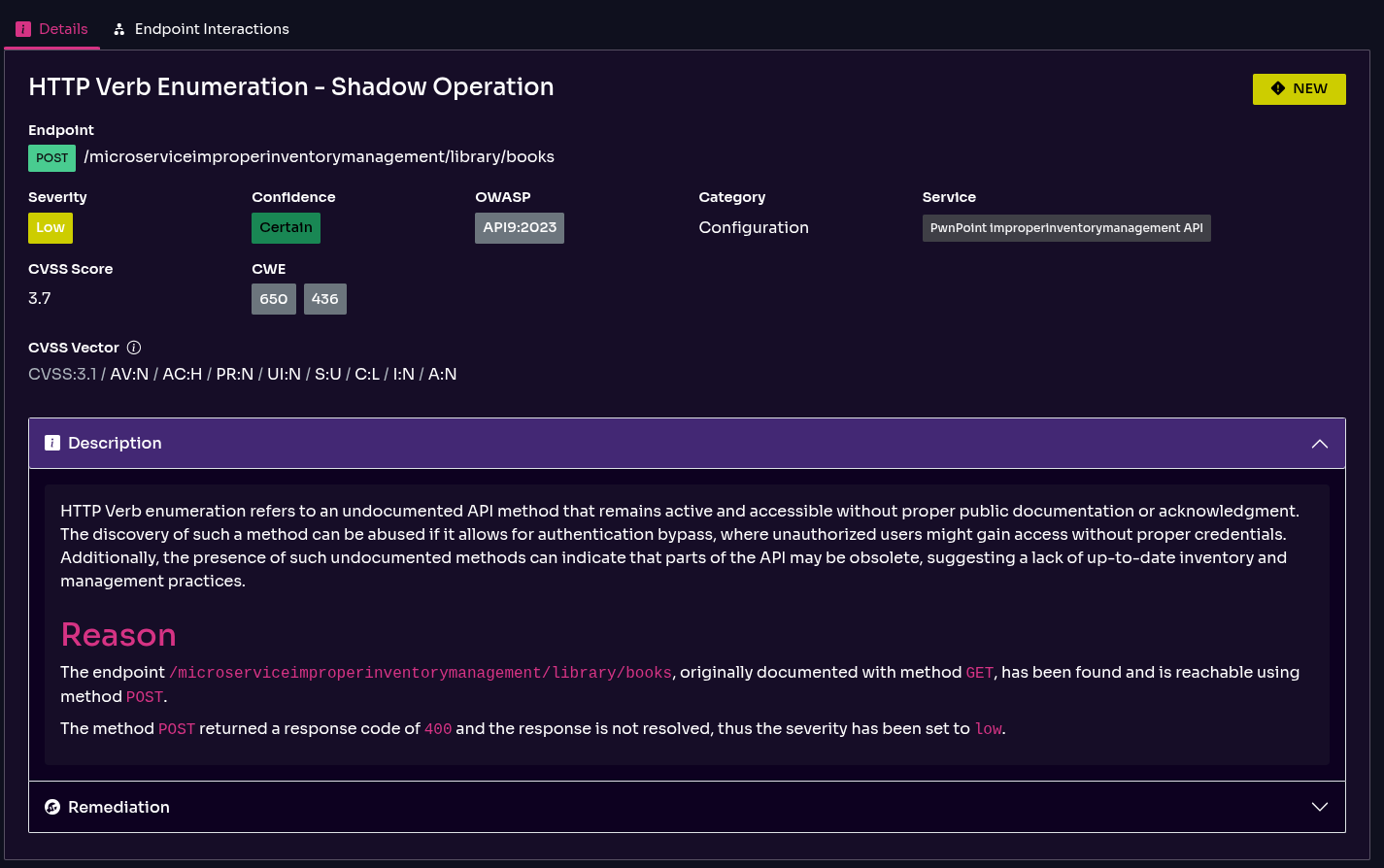
These endpoints have become a major source of security failures. Developers build them with a good intent, usually for quick testing or specific internal tasks. The problem is that they do so without informing the security team.
The consequence is severely impaired cybersecurity visibility, with an unacceptably large number of unknown and hence unprotected entry points.
2. The rise of agentic AI
In 2025, AI has become all about agents taking actions automatically (PwC, 2025). In such an environment, it’s key to understand that APIs are the ‘hands’ of AI (Postman, 2025).
AI applications use APIs to book flights, move data, or process payments. They act as more and more autonomous agents that will eventually execute these tasks without human oversight.
And as organizations rush to integrate AI into their environments, many do so without adequate API security measures, unaware that attackers can weaponize these APIs if an agent’s access is hijacked or an endpoint is left exposed.
3. From technical exploits to logic attacks
Injection, DoS, and other technical exploits remain relevant but are not the primary API security risks.
Broken Object Level Authorization (BOLA), on the other hand, has consistently been the number one risk since the first OWASP Top 10 API Security Risks list.
As essentially a logic flaw, it allows attackers to manipulate an API’s underlying sequencing or trust model, as well as legitimate methods and workflows, to provoke an unanticipated outcome.
4. The authenticated session paradox
In the first quarter of 2025, 95% of API attack attempts originated from authenticated sources (Salt Security, 2025, p. 11).
Attackers increasingly steal tokens rather than passwords, and when they have a session token, they appear to your system as a perfectly trustworthy user.
That makes traditional identity and access management (IAM) lacking on its own. It requires an additional security layer that deals with behavior, intent, and authorization as much as identity.
5. New regulations and higher board-level accountability
APIs are how businesses now integrate partners, monetize data, power mobile apps, and automate operations.
But APIs move volumes of regulated data, including PII, financial information, and health records. When they go down or experience data leaks, businesses come to a halt. Due to their central role in modern digital environments, regulatory scrutiny naturally follows.
In that spirit, governments have moved past simple data privacy to operational resilience requirements.
For example, DORA requires financial institutions to prove they have complete control over their digital interfaces, including APIs. It does not treat an API outage or breach as simply a data leak; it is, instead, a systemic failure of business continuity for which the organization itself is responsible.
 Equixly gives you thorough visibility into the data requested in the input, which is an essential requirement under DORA.
Equixly gives you thorough visibility into the data requested in the input, which is an essential requirement under DORA.
As new rules and laws hold board members and CISOs personally accountable for failing to disclose material risks, they turn API security from a Jira ticket into a principal boardroom agenda item.
Where Equixly helps with governance
Equixly approaches API governance as a continuous, extensively automated process given the nonlinear dynamics and scale of the contemporary digital ecosystem and its attack surface. It helps bridge the gap between high-level security policies and actual runtime behavior.
To be clear, the platform does not sit in the traffic path to block live attacks, as in runtime protection. Instead, it tests production application APIs to make sure their internal logic matches your governance standards.
Loosely speaking, this is a function of an automated auditor that continuously validates whether runtime behavior deviates from the established policies, processes, and standards.
You can maintain control over your API ecosystem through six key governance functionalities offered by Equixly.
1. Shadow APIs, inventory, and visibility
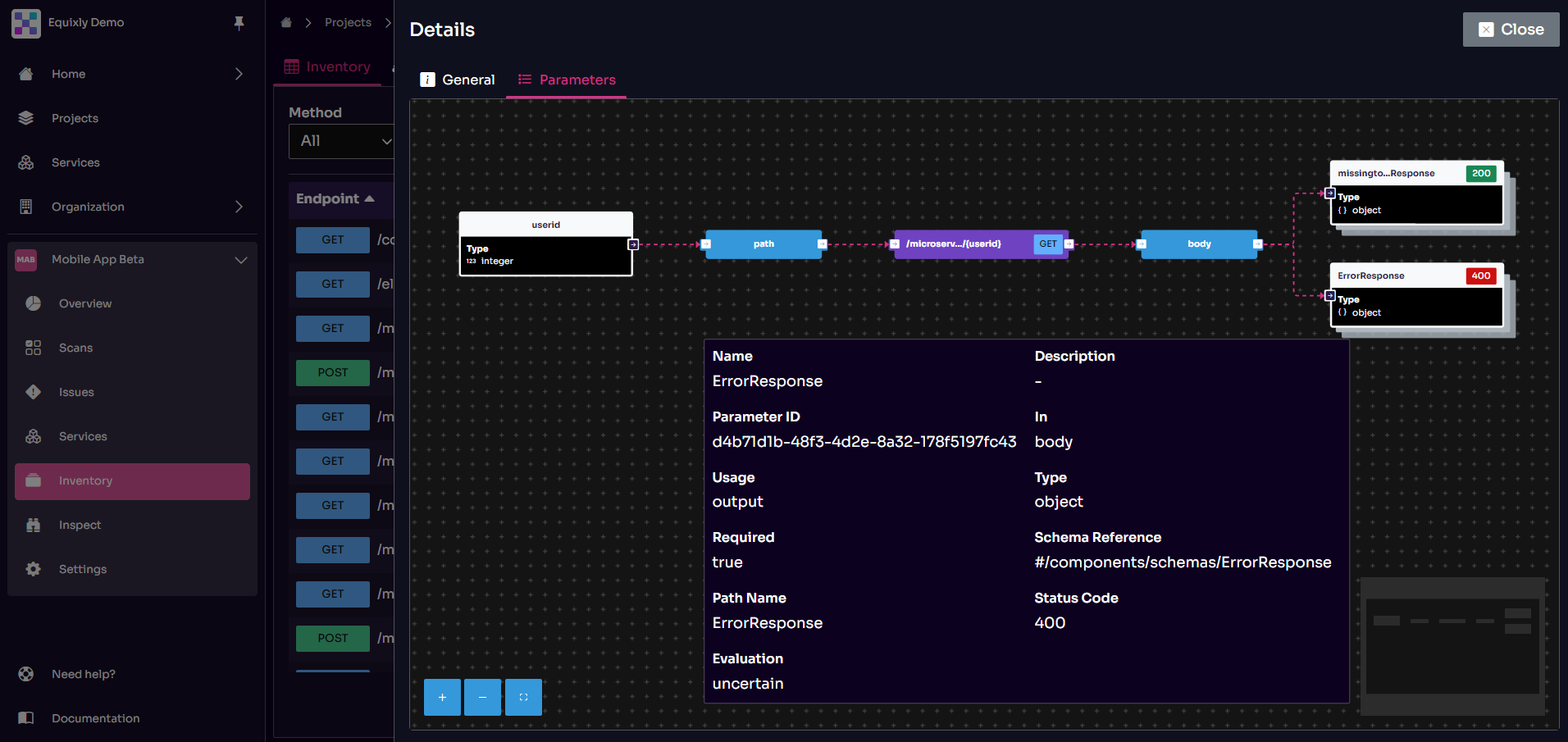
An elementary rule of security visibility and API governance is “you cannot protect what you don’t know.” With Equixly, the battle for visibility starts with finding shadow APIs, which are central to its “Inventory” functionality. Equixly now also supports importing HAR and Burp history files, offering users multiple ways to discover, import, and inventory APIs directly from recorded traffic.
In this regard, Equixly takes a different route from runtime endpoint discovery tools. The platform identifies undocumented API versions by comparing its test results with your API specifications. It shows the differences in a real-time, automated inventory, just like in this image:
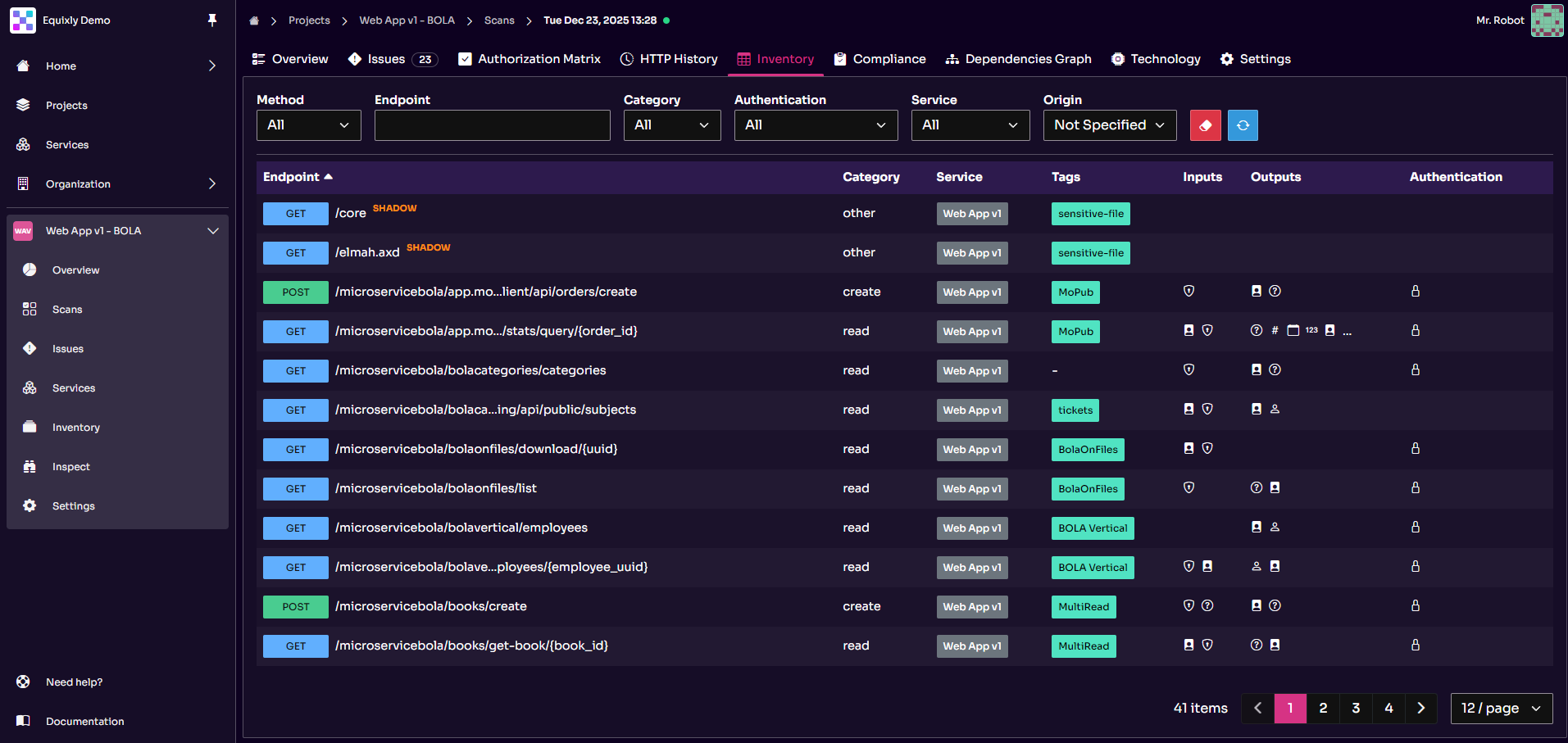
It’s worth noting that Equixly also identifies shadow parameters. The problem with these is that the backend can process and accept them, but because they are undocumented, the likelihood of them being unprotected is high. That means malicious actors can use them to bypass security and abuse the API. Here is one example:
POST /api/login
{
“username”: “john”,
“password”: “123”,
“isAdmin”: true // <-- UNDOCUMENTED: A common vector for privilege escalation
}
In addition, Equixly can detect verb tampering, the use of undocumented HTTP methods, and the coexistence of multiple accessible API versions (/v1, /v2, /beta). In this case, the older or non-official versions act like shadow APIs, as they shouldn’t be there and shouldn’t be accessible.
2. The “Authorization Matrix”: access policy enforcement
Equixly’s “Authorization Matrix” for APIs transforms abstract access policies into testable concrete logic. It delineates and links identities (roles), permissions (operations), and objects (resources) to make sure that each action has a defined outcome, such as 200 OK or 403 Forbidden.
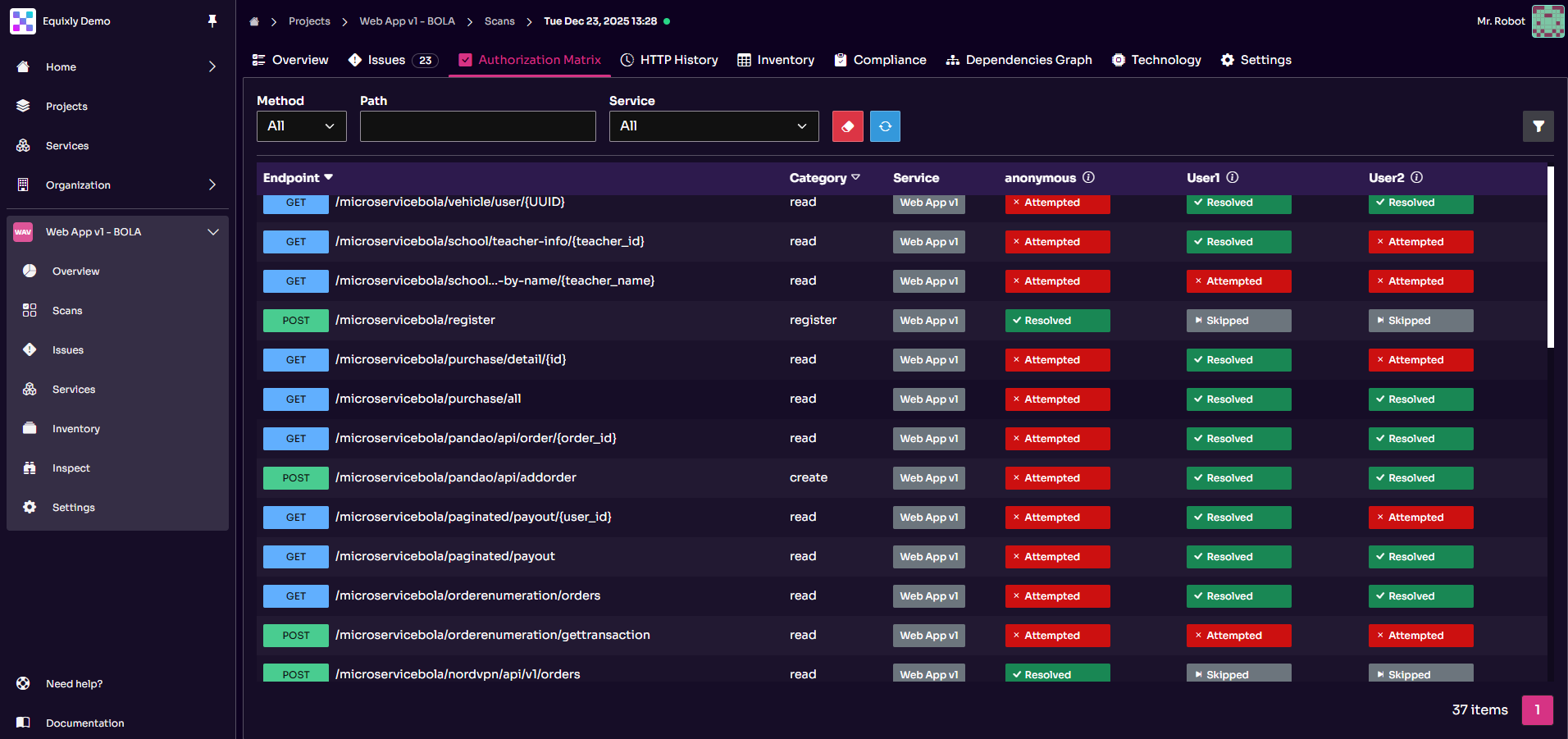
This feature also helps prevent development drift. Governance often fails when code changes deviate from documented policies. Equixly’s “Authorization Matrix” allows your deployed access mechanisms to stay consistent with your actual policies over time, focusing specifically on BOLA vulnerabilities.
3. Compliance and regulatory conformance
Equixly features a dedicated section for tracking how well your APIs meet compliance requirements. While the platform supports a wide range of frameworks, the interface currently offers native support for the following five:
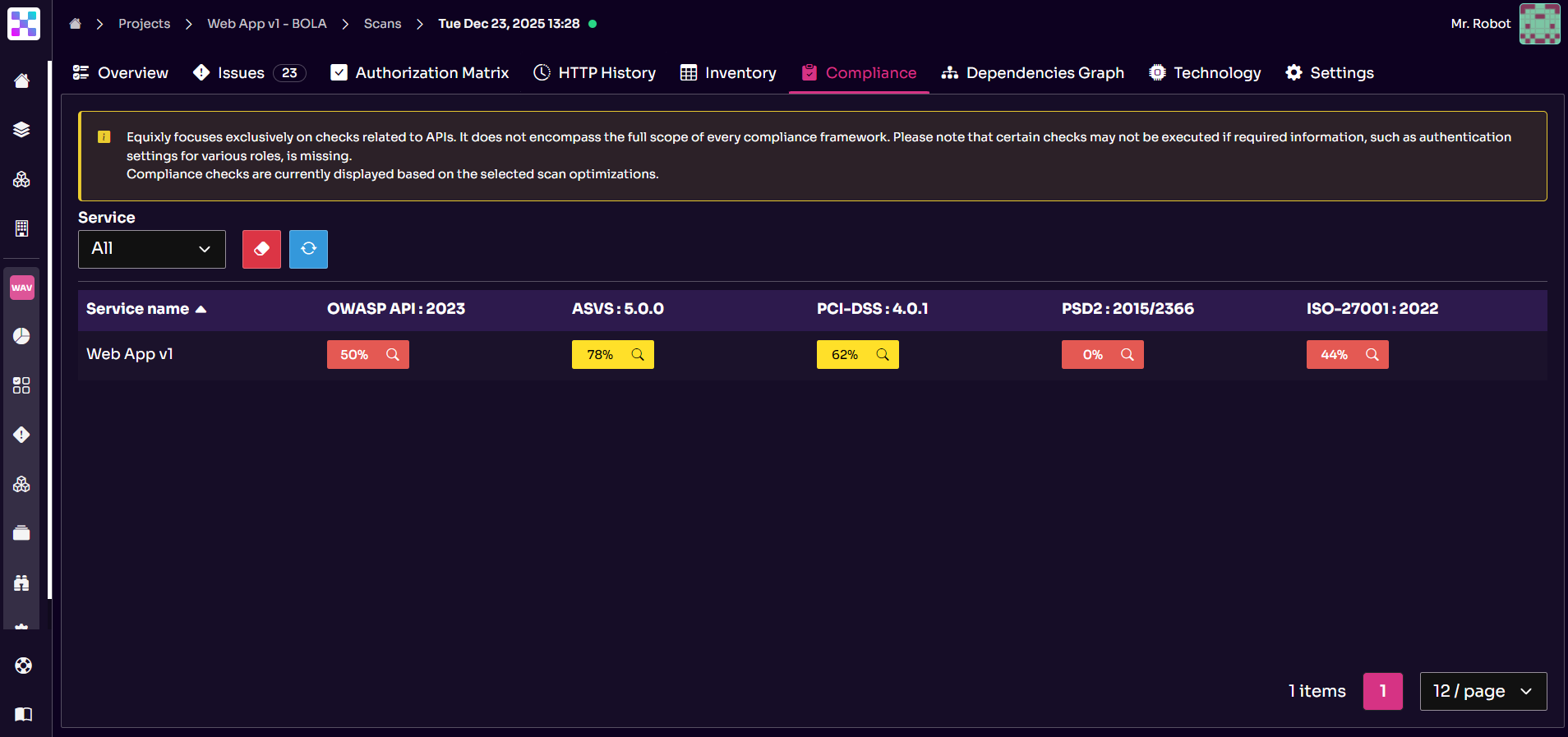
Keep in mind that, with general standards and regulations such as PCI DSS and ISO, the displayed percentage reflects only how much you meet API-specific requirements.
In addition to these five frameworks, Equixly also acts as an automated technical evidence generator in support of your:
- GDPR compliance efforts: Performs data classification and identifies endpoints that handle PII, payment information, and other sensitive data
- NIST SP 800-228 alignment: Helps with API inventory and asset management, advances the implementation of security controls in the SDLC, offers continuous testing feedback, and provides schema enforcement and robust authorization checks.
- DORA and NIS2 compliance: Conducts API security testing in development and production, providing auditable, repeatable results necessary for managing security vulnerabilities and demonstrating operational resilience. In addition, it includes a suite of features that help you maintain a strong API security posture.
4. Executive insights and technical reporting
Equixly generates API security testing reports in PDF or CSV format to provide auditable, repeatable documentation.
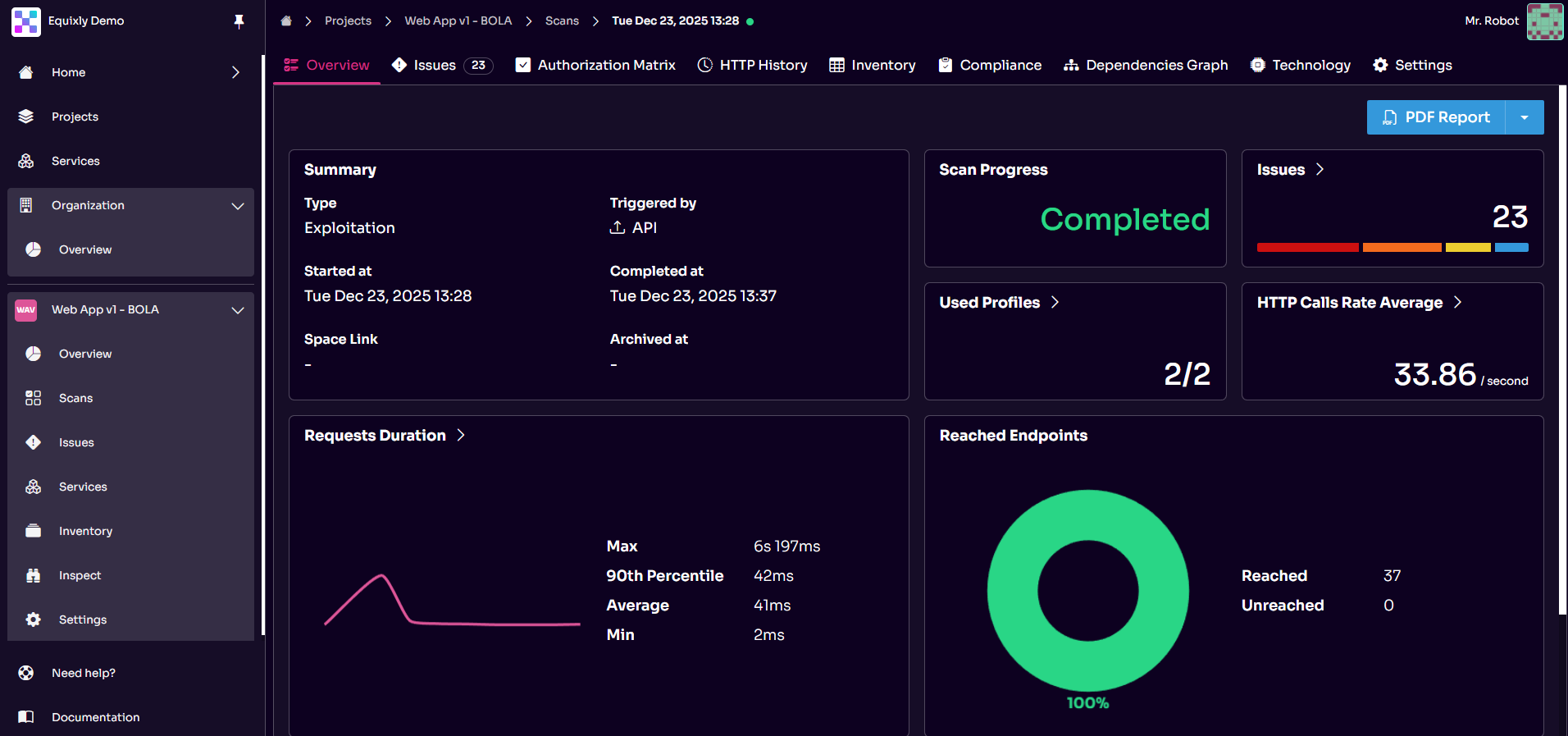
These reports comprise two sections:
- “Executive Summary”: Designed for risk visibility, this section is data-aware, business-aligned, and highly effective as a risk disclosure artifact. By bridging the gap between technical findings and business impact, it enables executives to make informed, data-driven decisions.
- “Detailed Security Issues Report”: This section provides a granular analysis of discovered vulnerabilities, including affected endpoints, vulnerability explanations, and proof-of-concept demonstrations. It also delivers to-the-point remediation guidelines necessary for addressing security risks and meeting remediation SLAs (Service Level Agreements).
5. Shift left and continuous governance
The critical role of continuous security testing in newer compliance requirements is, by now, broadly recognized. Shifting left, continued risk management, ongoing vulnerability identification, and security integrated in CI/CD pipelines are vital in the age of cloud-native systems and rapid release cycles.
Equixly has long emphasized the limitations of annual risk assessments, point-in-time penetration tests, and periodic audits when used as standalone measures.
Accordingly, the platform allows you to embed security tests directly into your development pipelines—it integrates with GitHub Actions, GitLab, Jenkins, and more—to execute policies on every code commit. Apart from this being in harmony with DevSecOps practices, it supports governance throughout the entire API life cycle.
6. LLM Governance
As organizations move toward LLM-powered applications, where APIs act as the primary interface, Equixly extends governance to these specialized environments.
How?
Equixly provides continuous security testing for LLM-integrated APIs, specifically targeting high-impact risks from the OWASP Top 10 for LLM Applications. That includes identifying vulnerabilities such as Prompt Injection, Sensitive Information Disclosure, and Insecure Output Handling, with broader coverage consistently added to address the evolving LLM threat landscape.
Conclusion
API governance has become a business necessity. As organizations tackle the growing API sprawl, the rise of agentic AI, and logic-based attacks, the gap between written policy and practical implementation is becoming an increasingly pronounced liability.
Equixly helps you address the API governance challenge head-on with continuous, automated validation that reconciles governance standards and operational execution. It leverages agentic AI and adversarial testing to support:
- Continuous visibility: Find shadow APIs and parameters that bypass traditional discovery methods.
- Logic validation: Enforce strong access policies to mitigate BOLA and other severe access weaknesses.
- Regulatory conformance: Generate reporting evidence that helps you meet compliance requirements such as ISO/IEC, PCI DSS, 27001:2022, DORA, and NIS2.
- SDLC integration: Embed security testing into CI/CD pipelines to make sure that governance keeps pace with the speed of development.
In short, Equixly enables your organization to move beyond ad hoc security and transform API governance into a repeatable process that drives operational resilience and compliance in our increasingly digitalized world.
If you’re looking to align your production reality with your governance standards, get in touch to learn the details of how Equixly helps you reconcile the two.
FAQs
What has turned API governance from a technical security issue into a primary board-level concern?
APIs are now at the heart of business operations and regulated data flows. Hence, problems caused by shadow APIs, logic flaws, or outages translate directly into tangible business risk, regulatory penalties, and executive accountability.
What prevents organizations from turning API security policies into real-world governance?
Phenomena such as fragmented API estates, undocumented shadow endpoints, and elusive logic-based authorization flaws make it difficult to verify that production behavior matches documented standards.
How does Equixly validate that API governance policies are executed in practice?
Equixly supports API governance by continuously and automatically testing both development and production APIs with agentic AI and adversarial techniques to verify that API authorization, logic, behavior, and security controls are in line with defined security policies, standards, and compliance requirements.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.

Alessio Dalla Piazza
CTO & FOUNDER
Former Founder & CTO of CYS4, he embarked on active digital surveillance work in 2014, collaborating with global and local law enforcement to combat terrorism and organized crime. He designed and utilized advanced eavesdropping technologies, identifying Zero-days in products like Skype, VMware, Safari, Docker, and IBM WebSphere. In June 2016, he transitioned to a research role at an international firm, where he crafted tools for automated offensive security and vulnerability detection. He discovered multiple vulnerabilities that, if exploited, would grant complete control. His expertise served the banking, insurance, and industrial sectors through Red Team operations, Incident Management, and Advanced Training, enhancing client security.