Understanding NIST SP 800-228 and Its Role in API Compliance
Zoran Gorgiev, Alessandro Begal
Just a few months ago, in June 2025, the National Institute of Standards and Technology (NIST) released its Special Publication 800-228.
This document delineates fundamental guidelines for securing APIs in cloud-native systems. The objective is to help organizations protect application programming interfaces to the best of their abilities, considering these interfaces’ pivotal role in digitalization and the software ecosystems.
The following sections analyze NIST SP 800-228, Guidelines for API Protection for Cloud-Native Systems, providing answers to four key questions:
- Is NIST SP 800-228 mandatory?
- Why do these API security guidelines matter?
- How does the document relate to existing cybersecurity frameworks and regulations?
- What are the key contents of this document?
Let the words lead you onward.
Is NIST SP 800-228 a Mandatory Compliance Requirement?
The straightforward answer is: NIST SP 800-228 is an officially issued Special Publication, but it’s not a mandatory regulation. Organizations can adopt it as a reference for best practices, but no one is legally required to follow it unless a specific rule, contract, or agency policy mandates compliance.
Then, why does it matter, especially given its primary relevance to the US?
The simple answer is that SP 800-228 is an invaluable document because it provides a blueprint for a strong API security strategy. Even without a legal obligation to follow them, aligning with these guidelines is a prudent approach because they
- Spell out authoritative best practices, as the guidelines are the result of creative collaboration between NIST, US federal cybersecurity experts, industry leaders, academia, and standard bodies such as ISO.
- Help organizations strengthen risk management and resilience through a holistic approach to API security, covering everything from authentication and authorization to DevSecOps integration and cloud-native deployment patterns.
- Build trust and credibility, signaling strong security maturity and providing assurance that an organization aligns with robust API security principles.
- Demonstrate high levels of professional expertise among cybersecurity architects, cloud engineers, compliance analysts, and auditors who understand and put the guidelines into practice.
-
Map directly to existing or future compliance needs, such as:
- Pascoe, C., Quinn, S., & Scarfone, K. (2024, February). The NIST Cybersecurity Framework (CSF) 2.0 (NIST Cybersecurity White Papers CSWP 29). National Institute of Standards and Technology, U.S. Department of Commerce
- Joint Task Force (2020, September). Security and Privacy Controls for Information Systems and Organizations (NIST Special Publication 800‑53, Revision 5). National Institute of Standards and Technology, U.S. Department of Commerce
- Federal Information Security Modernization Act of 2014, Pub. L. No. 113–283, 128 Stat. 3073 (2014).
- Joint Task Force. (2018, December). Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy (NIST Special Publication 800-37, Revision 2). National Institute of Standards and Technology, U.S. Department of Commerce
- FedRAMP Program Management Office. (n.d.). Federal Risk and Authorization Management Program (FedRAMP). U.S. General Services Administration
- Rose, S., Borchert, O., Mitchell, S., & Connelly, S. (2020, August). Zero Trust Architecture (NIST Special Publication 800-207). National Institute of Standards and Technology, U.S. Department of Commerce.
This last point deserves a separate section, as the connection between existing compliance requirements and NIST SP 800-228 forms one of the most compelling and practical reasons for the importance of this document.
Mapping SP 800-228 to Compliance Requirements
If we had to put it into a few words, what NIST SP 800-228 does is translate existing NIST and federal frameworks into actionable API security practices.
1. NIST Cybersecurity Framework (CSF 2.0)
| CSF 2.0 Core Function and SP 800-228 Guidance Mapping | ||
|---|---|---|
| CSF Core Function | Relevant SP 800-228 Guidance | Synthesis Point |
| Identify | Inventory APIs, understand their exposure surface, and classify data flows. | Advocates an API asset inventory consistent with the CSF ID.AM (Asset Management). |
| Protect | Implement authentication, authorization, encryption, schema validation, throttling, and secure DevOps pipelines. | Operationalizes PR.AA (Access Control), PR.DS (Data Security), and PR.MA (Maintenance). |
| Detect | Continuous API activity monitoring, anomaly detection, and centralized logging. | Extends DE.CM (Continuous Monitoring) to API telemetry and observability. |
| Respond | Integrates API incident handling, revocation of compromised tokens, and automated playbooks. | Strengthens RS.RP (Response Planning) and RS.AN (Analysis). |
| Recover | Guidance on rollback of vulnerable API deployments and re-establishing trust relationships. | Supports RC.IM (Improvements) and RC.RP (Recovery Planning). |
2. NIST SP 800-53 Rev. 5 Control Families
| 800-53 Control Family and SP 800-228 Guidance Mapping | ||
|---|---|---|
| 800-53 Control Family | How 800-228 Applies It | Example Mechanism |
| AC: Access Control | Defines OAuth 2.0 / OpenID Connect usage, token scopes, and API gateway enforcement. | Fine-grained, least-privilege access via JWTs or mTLS. |
| IA: Identification and Authentication | Requires strong authentication for both human and machine identities. | Mutual TLS, client certificates, and API keys management. |
| SC: System and Communications Protection | Secures data in transit, validates schemas, and prevents injection. | TLS 1.3, content-type allowlisting, and API firewalling. |
| SI: System and Information Integrity | Calls for input validation, error handling, and vulnerability management. | Schema enforcement, WAF rules, and secure error responses. |
| AU: Audit and Accountability | Prescribes API-level logging and correlation with SIEM. | Traceable event logs with unique identifiers. |
| CM: Configuration Management | Integrates security controls into CI/CD pipelines. | Infrastructure-as-Code with policy scanning. |
| IR: Incident Response | Establishes playbooks for API compromise scenarios. | Token revocation and rapid redeployment. |
| RA: Risk Assessment | Insists on threat modeling for APIs and microservices. | STRIDE-based risk analysis during design. |
3. Federal Information Security Modernization Act (FISMA)
FISMA mandates that federal information systems implement NIST controls. SP 800-228 gives agencies practical guidance on how to apply those controls to APIs.
4. Risk Management Framework (RMF; SP 800-37 Rev. 2)
SP 800-228 aligns directly with the RMF’s “Implement” and “Assess” steps, offering measurable security expectations for API interfaces.
5. Federal Risk and Authorization Management Program (FedRAMP)
FedRAMP baselines are built from NIST SP 800-53 Rev. 5. SP 800-228 complements them by
- Specifying API controls for cloud service providers (CSPs)
- Addressing shared responsibilities between CSPs and customers for API security in SaaS/PaaS environments
- Reinforcing FedRAMP’s goal of consistent, auditable control implementation in multi-tenant cloud systems
6. Zero-Trust Architecture (ZTA; SP 800-207)
SP 800-228 calls for
- Identity-centric access to APIs (never implicit trust)
- Continuous verification through runtime monitoring and policy enforcement at API gateways
- Micro-segmentation of services and contextual authorization
It functions practically as a zero-trust policy for API and microservice communication.
NIST SP 800-228: Overview
This section distills the central principles and protective measures advocated in NIST SP 800-228. It outlines the document’s thematic priorities and the recommended mechanisms for protecting your pre-runtime and runtime environments.
Central Themes
NIST SP 800-228 revolves around four topics:
- Zero-trust model: Champions robust authentication and continuous verification of users, services, and devices interacting with APIs.
- Security across the entire API life cycle: Promotes security as an integral part of the entire API life cycle—from design and development to testing, deployment, and beyond—to minimize the likelihood of security vulnerabilities slipping into production.
- Continuous monitoring and response: Emphasizes the benefits of monitoring API traffic in real-time to detect anomalies, responding to security events as they occur, and continuously improving API security practices based on insights gained from monitoring.
- Data protection: Requires strong encryption, input validation, and stringent controls to prevent unauthorized access to data.
Two Types of Protection
NIST SP 800-228 differentiates between pre-runtime and runtime protections.
Pre-Runtime Measures
These protect APIs during the design, development, and testing phases.
Basic
- REC-API-1, API specification: Every API must have a clear and well-documented specification.
- REC-API-2, Well-defined interface definition language (IDL): Adopt standardized IDLs like OpenAPI, gRPC, Thrift, or SOAP for API design.
- REC-API-3, Request and response schema: Define and validate the structure, field types, and validation rules for each API endpoint.
- REC-API-4, Centralized API governance framework: Keep an inventory of APIs, including documentation, ownership, and operational metadata.
Advanced
- REC-API-5, Request and response validation in the schema: Define and validate input and output parameters in API specifications to prevent malformed requests and responses.
- REC-API-6, Sensitivity and permission annotations: Tag fields as public or internal and annotate with permission levels for access control.
- REC-API-7, Semantic data type annotations: Annotate sensitive data fields, like personally identifiable information (PII) and protected health information (PHI), for secure data flow and leakage prevention.
- REC-API-8, Runtime information in the API inventory: Include detailed runtime information in the API inventory for operational and security auditing.
Runtime Measures
These center on continuous monitoring and securing live API environments.
Basic
- REC-API-9, Runtime communication encryption: All communication between API components must be encrypted, even if the data is not sensitive, to protect against tampering and eavesdropping.
- REC-API-10, General request and response validation: Put into practice general validation mechanisms, such as bot detection and DoS mitigation, to prevent malicious payloads and unrestricted resource consumption.
- REC-API-11, Robust authentication: Authentication credentials must be handled appropriately through rate limiting and lockouts, combined with multi-factor authentication (MFA).
- REC-API-12, Authorization checks: Each API request should be verified for proper authorization, confirming that the caller has the necessary permissions for the requested action.
- REC-API-13, Syntactic validation of request/response: Perform basic validation of the API request and response structure to be certain that they adhere to predefined formats and schemas.
- REC-API-14, Input length validation: Validate input length for all incoming requests to avoid buffer overflows and vulnerabilities associated with uncontrolled input sizes.
- REC-API-15, Rate limiting: Implement rate limiting per user or service to prevent excessive resource consumption or abuse.
- REC-API-16, Circuit breaking and resilience: Set thresholds on request concurrency and implement mechanisms like circuit breakers to protect APIs from overloads and failures.
Advanced
- REC-API-17, Fine-grained blocking of users: Implement fine-grained blocking at the user or network level, allowing for targeted mitigation during attacks or incidents.
- REC-API-18, API access monitoring: Monitor API access using telemetry, logging, and metrics to make sure that policies are being enforced and to detect anomalies or attacks as they happen.
- REC-API-19, Field-level validation: Perform field-level validation on incoming API requests and responses using API schema annotations to guarantee that data meets both syntactic and semantic expectations.
- REC-API-20, Authorization and filtering via API schema: Use annotations to define resource-level permissions within the API schema and enforce these checks at runtime.
- REC-API-21, Telemetry and audit logging: Collect detailed telemetry data, such as request/response logs, timestamps, and status, to facilitate real-time incident detection and post-event forensics.
- REC-API-22, Non-signature payload scanning: Analyze API responses for sensitive information using tools that perform content-based analysis to identify potential data leaks or exfiltration attempts.
- REC-API-23, Error code design: Design error codes to avoid revealing too much information that could aid attackers in enumerating resources or identifying weaknesses in the API.
- REC-API-24, Resource enumeration mitigation: Protect against resource enumeration attacks through rate limiting and anomaly detection techniques.
- REC-API-25, Data masking for sensitive information: Use data masking to prevent the exposure of sensitive information in API responses or logs.
- REC-API-26, Fine-grained request blocking: Apply fine-grained blocking for requests, particularly those that can lead to denial of service or crashes.
How Equixly Aligns with SP 800-228 and the NIST Ecosystem
Equixly is a platform that shines in two central API security areas (according to OWASP):
- API security testing
- API security posture
It is a feature-rich solution that aligns exceptionally well with the API security principles outlined in NIST SP 800-228.
API Discovery, Inventory, and Asset Management
SP 800-228 emphasizes maintaining visibility into an organization’s API surface. In practice, that translates to identifying what APIs exist, how they are exposed, and what data or functions they handle (Section 3, Recommended Controls for APIs).
Equixly’s platform supports these requirements by automating API discovery, including shadow APIs, and classifying endpoints by exposure and risk.
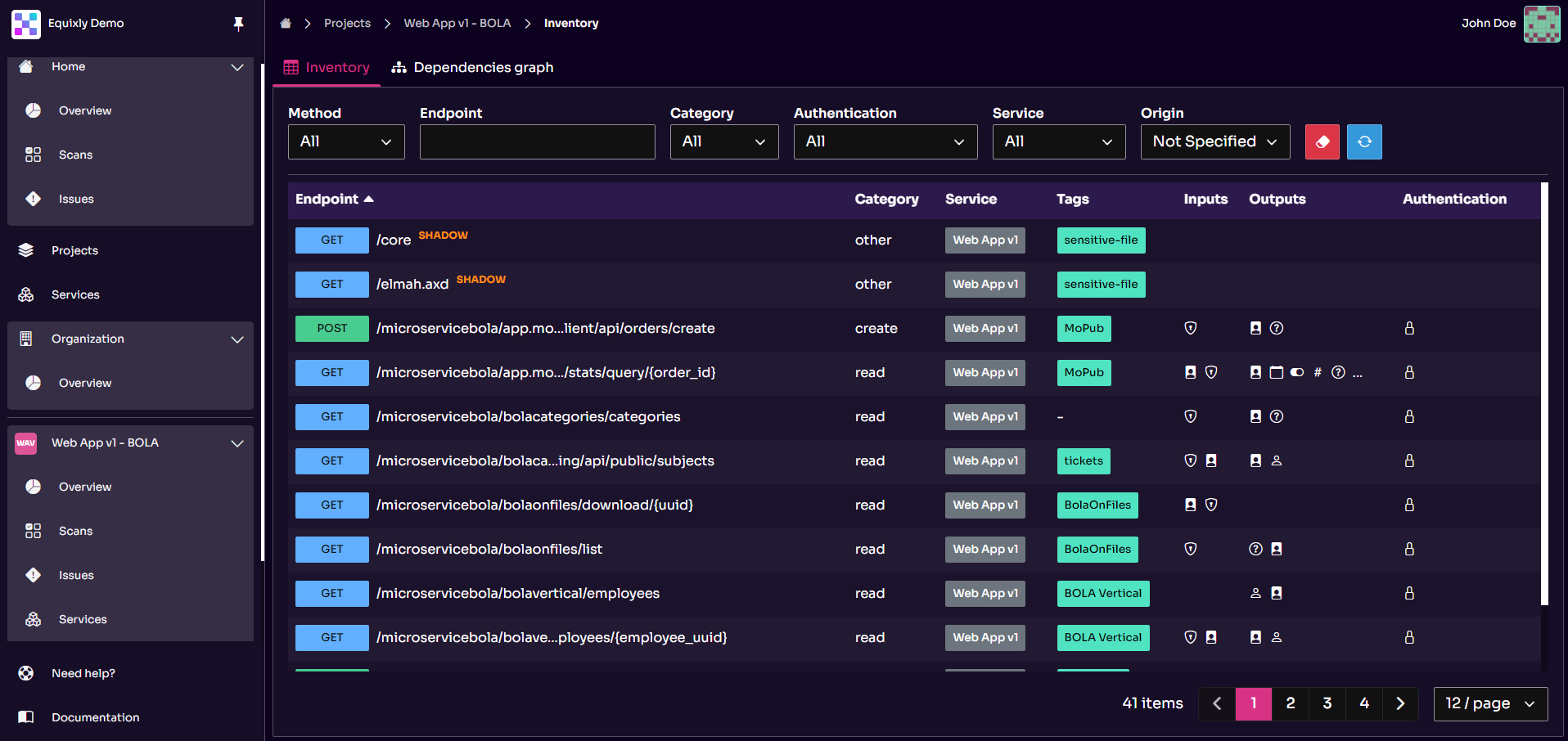
These capabilities, in turn, align with the “Identify” function of the NIST Cybersecurity Framework (CSF) 2.0 and asset/inventory controls in NIST SP 800-53 Rev. 5 (e.g., CM-8).
Protect and Implement Controls in the Software Development Life Cycle
SP 800-228 (Sections 2 and 3, and Appendix B) recommends integrating authentication, authorization, input validation, and similar protective controls into the software development and deployment life cycle (DevSecOps).
Equixly integrates into CI/CD pipelines to perform continuous, automated API security (pen)testing early, which helps you put those design-time and pre-deployment protections in place.
This Equixly capability aligns with the “Protect” function of CSF 2.0 and with SP 800-53 Rev. 5 control families, including IA (Identification and Authentication), SC (System and Communications Protection), and SI (System and Information Integrity).
Detect and Improve Through Continuous Testing Feedback
SP 800-228 emphasizes the importance of runtime monitoring, logging, and anomaly detection as part of comprehensive API security (Section 3.2).
Equixly does not perform runtime monitoring; however, its continuous testing and vulnerability discovery help reduce the unknown attack surface and provide practical remediation insights for downstream detection systems, such as SIEM.
That, further, supports the “Detect” and “Respond” functions of CSF 2.0 and relates to SP 800-53 families such as AU (Audit and Accountability) and IR (Incident Response), by contributing data that informs incident analysis and remediation.
Compliance Readiness and Maturity
To reiterate a key point, SP 800-228 is voluntary but designed to harmonize with other NIST frameworks. Implementing its guidance helps demonstrate sound API security governance consistent with FedRAMP, FISMA, and RMF expectations.
Using a platform like Equixly provides evidence artifacts—like testing reports, findings, and remediation tracking—that can support documentation for 800-53 controls, continuous monitoring, and risk management reviews.
| Equixly’s Alignment with SP 800-228 and Other Frameworks | ||
|---|---|---|
| Equixly | NIST SP 800-228 | Frameworks & Controls |
| API Discovery | Section 3 “Recommended Controls for APIs” — REC-API-4.2 (Organizational API inventory incl. shadow/zombie) | Identify, CM-8, FISMA / FedRAMP, NIST.SP.800-228 |
| Threat Modeling | Section 2 “API Risks: Vulnerabilities and Exploits”; Section 3.1 “Pre-Runtime Protections” | Identify, RA-3, RA-5, RMF, NIST.SP.800-228 |
| DevSecOps Testing | Appendix B “DevSecOps Phases and Associated Classes of API Controls”; Section 3 “Recommended Controls for APIs” | Protect, SI-2, CM-3, Zero Trust, FedRAMP, NIST.SP.800-228 |
| Auth/Access Testing | Section 3.2 “Runtime Protections”; Section 2.7 “Credential Canonicalization: Preparatory Step for Controls” | Protect, AC-3, IA-2, FedRAMP, ZTA, NIST.SP.800-228 |
| Data Validation | Section 2.6 “Insufficient Verification of Input Data” (2.6.1 Input Validation; 2.6.2 Malicious Input Protection); Section 3.2 “Runtime Protections” | Protect, SI-10, SC-7, All frameworks, NIST.SP.800-228 |
| Testing Results Supporting Monitoring and Detection | Section 3.2 “Runtime Protections” (telemetry, logging, anomaly detection); Section 4.4 “Related Technologies” (WAF, bot detection, DDoS mitigation, WAAP, API endpoint protection) | Detect, AU-6, SI-4, CDM, ZTA |
| Reporting / Remediation | Section 3 “Recommended Controls for APIs” (feedback/continuous improvement); Appendix B (DevSecOps feedback phase) | Respond / Recover, IR-4, CA-7, FedRAMP POA&M, NIST.SP.800-228 |
Final Thoughts
NIST SP 800-228 is not a regulation, at least not yet. Its value lies in operationalizing frameworks such as CSF 2.0, SP 800-53, and zero-trust to real-world API ecosystems.
A platform like Equixly translates the principles of these API security guidelines into reality. It helps you bridge design-time controls, continuous testing, and compliance evidence, turning best practices into measurable security outcomes.
Let’s continue the conversation: See how Equixly empowers teams to tackle the OWASP Top 10 API Security Risks and confidently deliver secure, compliant APIs.
FAQs
What is NIST SP 800-228, and who should use it?
NIST SP 800-228 consists of guidelines designed to help organizations secure APIs in cloud-native systems. It is not mandatory, but it is a highly valuable set of API security best practices, especially for federal agencies, contractors, and private organizations in regulated sectors like government, healthcare, and finance.
How does SP 800-228 relate to other NIST frameworks?
SP 800-228 supports existing controls in areas like access control, system protection, continuous monitoring, and response planning, aligning with NIST frameworks such as SP 800-53 and the Cybersecurity Framework (CSF), among others.
How can organizations start implementing NIST SP 800-228?
Begin by assessing your API inventory and implementing DevSecOps practices. Regular security testing, monitoring, and compliance audits are also essential.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.

Alessandro Begal
Head of Solution Engineering
Alessandro has developed a broad technical background over the last 15 years in IT managed services, focusing on infrastructure management, data center modernization, network, and security. He has held various international leadership roles at an IBM company, emphasizing the importance of automation, with a proven track record of managing complex IT environments and leading teams to drive innovation and efficiency.