Equixly for Developers
Zoran Gorgiev, Edoardo Zatti

APIs are everywhere—microservices, mobile backends, partner integrations, third-party services, and now AI agents. With 83.2% of organizations adopting an API-first approach, APIs have indeed become the basis of contemporary software development.
Developers are already juggling data models, business logic, system architecture, and performance. Adding security on top of everything can sometimes feel like carrying the weight of the world on your shoulders.
Equixly was created to relieve this burden. Its raison d’être is to empower developers to release secure code with high confidence, free from friction or complexity.
In this article, you’ll learn how the API security platform integrates into CI/CD, DevOps, and DevSecOps workflows, acting as an automated security professional that works behind the scenes to provide concise, practical solutions to the security challenges in API development.
Clarity and Actionable Feedback
Demystifying API security assessments is Equixly’s central design principle. The platform provides clear, accessible outputs that don’t require security expertise to use effectively. In other words, the learning curve for mastering Equixly is shallow—one of the rare cases where “shallow” is a good thing.
The user interface (UI) lets developers easily navigate the dashboard, manage tasks, and act on scan results. The design is clean, and the information is clear and easy to understand, with no confusing jargon.
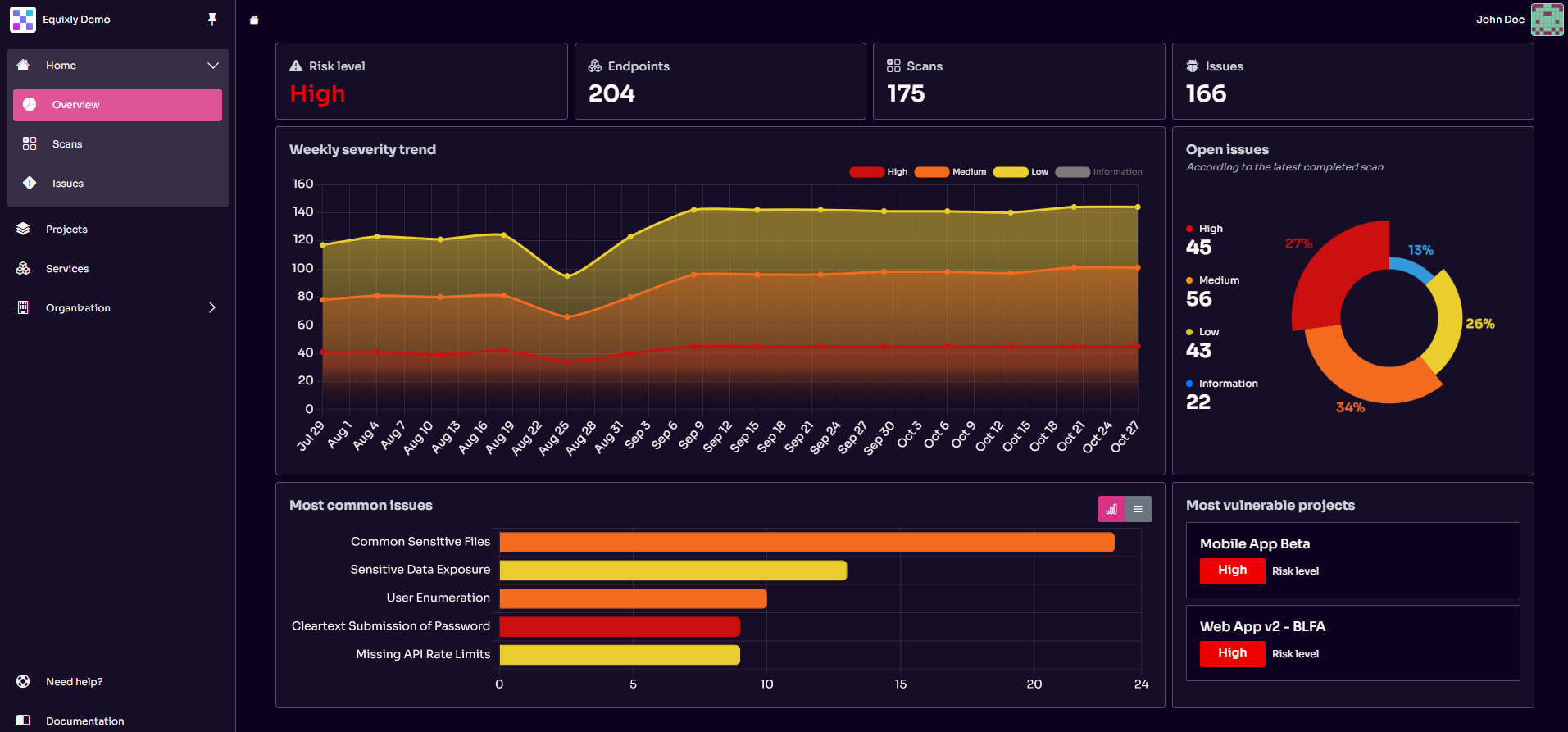
When the platform discovers a security issue, it alerts you with concise descriptions and actionable remediation suggestions, helping you understand the root cause and fix the problem promptly.
This clarity stems from Equixly’s pragmatic approach: Everyone should be able to act on security findings, but to do so, they must first be able to interpret the data at a glance.
Extensive Testing Coverage
The API security terrain is rough, with unique risks that developers can overlook. Here are two examples:
-
Weak trust boundaries: Organizations sometimes place excessive trust in third-party APIs, which leads to relaxed security controls for integrated services. This risk is particularly pronounced in machine-to-machine interactions, where internal systems automatically call external APIs.
Without actively testing or scanning integrations, you may fail to detect when a third-party API returns unsafe data, exposes excessive information, or exhibits weak authentication or input validation. Simulating such API interactions during testing can reveal whether external services behave securely and how resilient internal systems are when faced with unexpected or malicious responses.
Attackers often exploit these weak points as a route to compromising internal systems.
-
Configuration oversight: Engineers may overlook the complex configurations inherent in APIs and their surrounding systems. Failing to apply security best practices during configuration leaves APIs wide open to exploitation.
-
Application instability and business continuity risks: APIs can behave unpredictably when subjected to unusual or high-volume requests, revealing hidden stability issues. Such behavior can disrupt critical processes and pose risks to business continuity if not identified early through rigorous testing.
Equixly helps bridge security gaps like these that creep in during development.
One way it does so is by classifying data during API specification parsing. The platform highlights API endpoints that handle sensitive data, such as credit card or personally identifiable information. That helps you prioritize security measures on the most critical endpoints.
Another key feature, probably the most important, is Equixly’s focus on the latest OWASP Top 10 API Security Risks. As a purpose-built API security testing platform, it makes sure that no risks, including business logic vulnerabilities, go undetected.
For instance, broken object-level authorization (BOLA), which often manifests as a logic flaw in the form of insecure direct object reference (IDOR), allows attackers to manipulate object identifiers in API calls to access or alter data belonging to other users.
The platform can detect this vulnerability, among others, by using its authorization matrix feature to emulate unauthorized access attempts and validate whether developers have enforced proper permissions server-side.
But Equixly doesn’t stop at unique API logic vulnerabilities. It includes extensions that help clients address more traditional risks, that is, technical vulnerabilities such as:
- SQL injection
- Insecure deserialization
- Command injection
- XML external entities (XXE)
- Directory traversal
- Elevation of privilege (via the authorization matrix feature)
By integrating security into development, Equixly prevents costly security oversights and weaknesses from becoming full-blown incidents during production.
Programmatic Integration and the CI/CD Pipeline
For DevSecOps teams, integrating security testing painlessly into the development life cycle is essential. The good news is that Equixly was built precisely with the shift-left approach and API security automation in mind.
API Access and Automation
The platform allows organizations to automate processes via its API. This programmatic access makes it easy to manage configurations and automatically trigger scans as part of your workflows.
Webhooks: Connecting Results to Workflows
Equixly supports webhooks to enable connectivity with your existing tools and workflows. After it completes a scan, the platform automatically sends a structured JSON payload containing the test details to designated third-party systems. That enables your team to:
- Integrate scan results into existing security and development pipelines.
- Trigger custom actions in preferred tools based on the scan results.
- Automatically log results in security information systems.
- Automate workflows by connecting scan completion events to downstream processes.
- Enhance monitoring by forwarding scan data to dashboards and alerting systems.
It’s also worth noting that if you use Equixly’s Space Link agent on-premises, you can connect your webhook integration to concrete Space Link instances to guarantee delivery even in isolated network environments.
CI/CD Integration
You can integrate Equixly into your CI/CD pipeline using its provided container image. It’s a distroless image that offers:
- A compact image size (under 30 MB) that doesn’t affect performance or functionality
- A reduced attack surface by eliminating components that could introduce vulnerabilities
- Improved security with no shell or system tools included
Equixly’s compatibility is broad. It supports various environments, such as:
- GitHub Actions
- GitLab CI
- Bitbucket
- Jenkins
- Azure DevOps
Most importantly, the platform operates in both pre-production and production environments:
- In pre-production, the CI/CD integration enables automated scans and endpoint testing without exposing real production data.
- In production, the platform validates and reviews pre-production findings before deployment.
On-Premises Scanning
For testing internal endpoints, the Equixly Space Link acts as an agent installed within a customer’s private data center. It’s basically a Docker image that runs as a container on a server or within containerized platforms like Kubernetes/OpenShift. It makes it possible to perform exploration and exploitation scans on private endpoints.
Defining the Scan Scope and Managing Data
Securing your APIs starts with defining what to test and how to authenticate.
Service and Specification Support
The core unit for scanning is a Service. Each Service needs a unique name, description, and base URL. It’s directly linked to the API documentation—the specification or definition you want to test.
Equixly supports a wide range of specification formats:
| API Support Types | |
|---|---|
| Swagger | Yes |
| OAS | Yes |
| Postman Collections | Yes |
| WSDL | Yes |
| GraphQL | Yes |
For GraphQL, you can load a schema definition language (SDL) file or use the result of introspection, which dynamically explores your API’s types and structure.
Authentication and Access Control
Equixly supports common authentication methods like OAuth and AWS Cognito.
It also provides role-based access control (RBAC). For each profile, you can assign a role (regular user or admin) and optionally a group to manage multiple users or admins with varying access levels. This setup supports multi-project and multi-tenant environments.
For third-party integrations and pipeline automation, admins manage API keys—they can create or deactivate keys as needed for authentication.
Custom Hooks for Advanced Authentication
Developers can extend authentication logic using the JavaScript SDK, or optionally leverage the Playwright SDK for more advanced, browser-based scenarios. Together, these tools enable the creation of complex authentication flows—including those involving interactive logins or multi-factor steps—through custom scripts and hooks. They allow you to:
- Implement tailored authentication mechanisms such as token generation, session handling, or signature creation to match custom requirements.
- Authenticate requests securely and compliantly.
- Handle dynamic or runtime credentials like those from environment variables, IAM roles, or temporary tokens.
- Integrate with secured services and APIs under different environments and authentication schemes.
Scope Control and Safety
To define testing boundaries, developers can configure:
- Path rules—include or exclude specific endpoints from the scan.
- Production safeguards—such as the Production URL flag, used for staging environments that mirror production. These safeguards enable comprehensive and safe testing by preventing disruptive operations (e.g., form submissions that could modify live data).
API Inventory and Result Analysis
Equixly gives you exhaustive visibility into your APIs—from endpoint discovery to issue tracking—helping you understand how your services evolve and where potential risks lie.
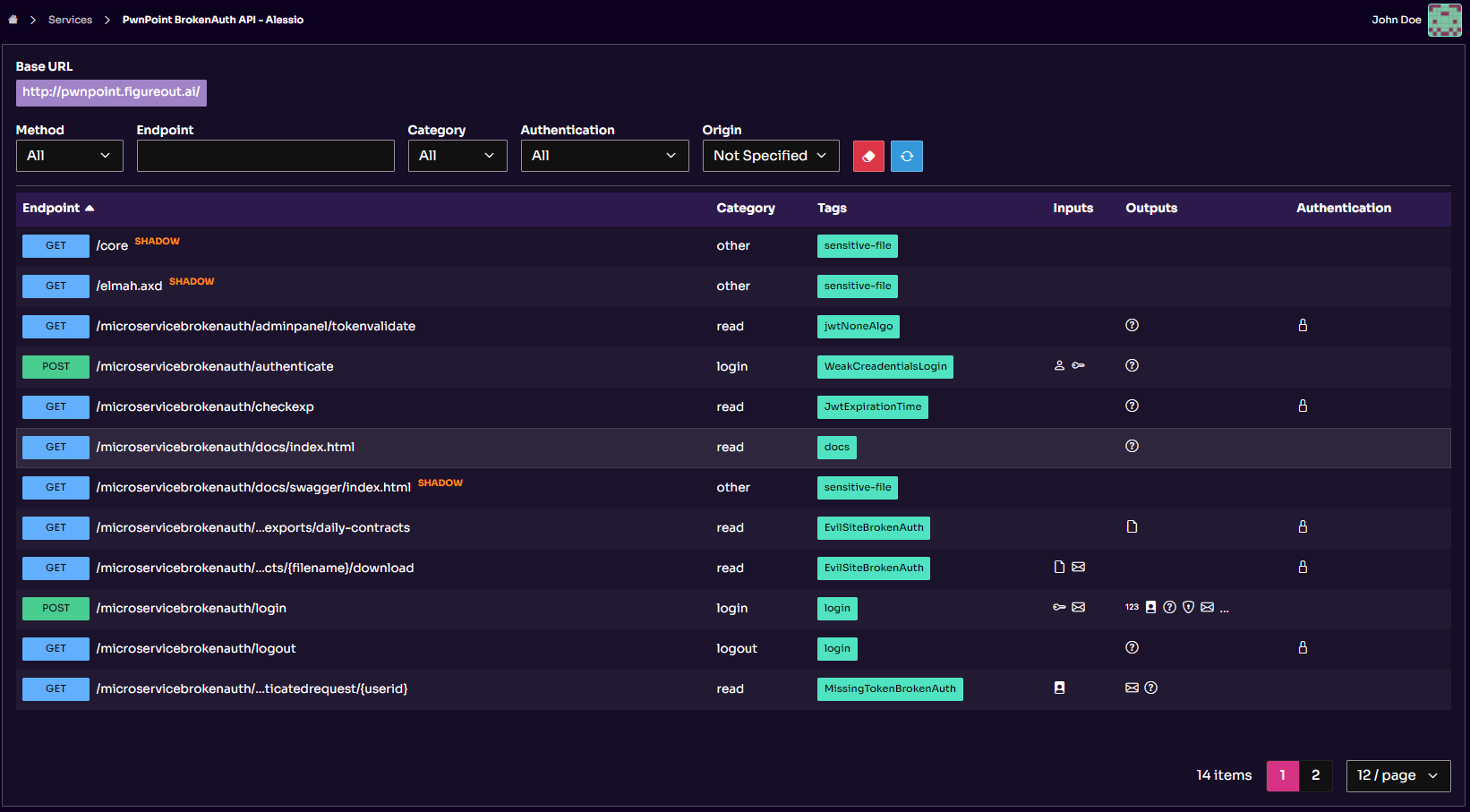
Exploring API Endpoints
The API inventory provides a continuously up-to-date overview of your service’s API data, automatically refreshed after every scan. It catalogues endpoints and displays key details, such as:
- Endpoint: The path and HTTP verb defined by the specification. Category: The type of endpoint automatically identified by Equixly, like Update, Create, Read, Login, or Delete.
- Input/Output: Data classification parameters identified through semantic data type recognition.
- Auth: An indicator of whether an endpoint is authenticated in the specification.
- Service: The service associated with the endpoint.
When you open an endpoint, the Parameters tab displays a graphical representation of the request. Hovering over elements reveals details such as the Oracle format, schema reference, usage information, and schema composition.
Dashboard and Issue Management
When a scan is complete, you can see the results in the Equixly dashboard. There, the findings are shown into two key sections:
- Latest scan: Displays issues identified in the most recent scan for immediate review.
- Historical findings: Tracks issues from previous scans, providing a long-term view of your API’s security posture.
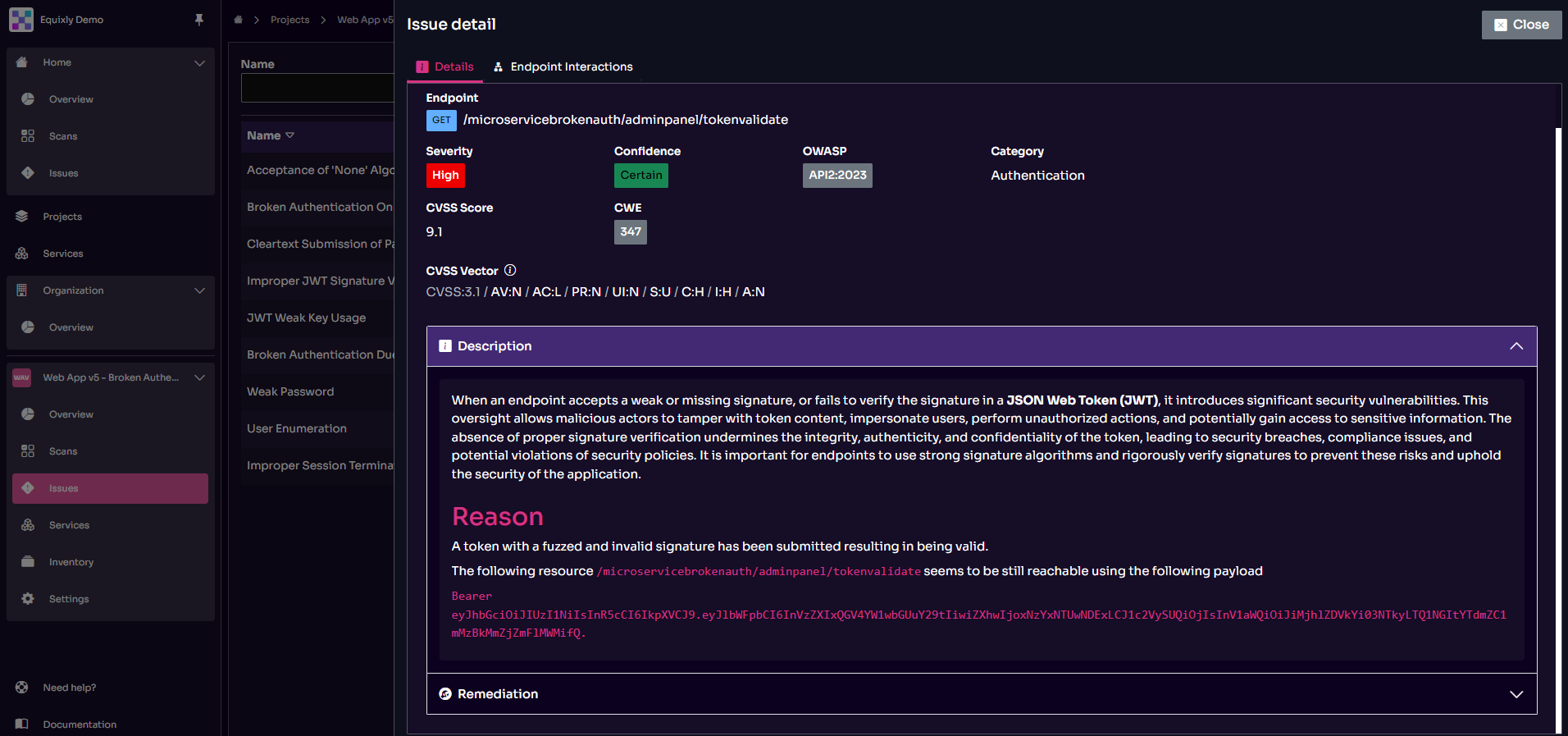
Selecting an issue opens a detailed view that includes:
- Problem description: A clear explanation of the identified issue.
- Remediation advice: Practical guidance for resolving security concerns.
- API call chart: A visual map of the API calls Equixly carried out to detect the issue, helping with reproduction and debugging.
- Request/Response review: A full breakdown of the HTTP requests and responses involved.
Endpoint Interaction and Exploitation Insight
Equixly goes beyond detection by allowing developers to interact directly with vulnerable endpoints.
Through detailed request and response views, developers can trace exactly how Equixly, and by extension, adversaries exploit a specific vulnerability in their environment, step by step. This transparency helps them understand the attack path, reproduce the issue, and verify the fix after they implement it.
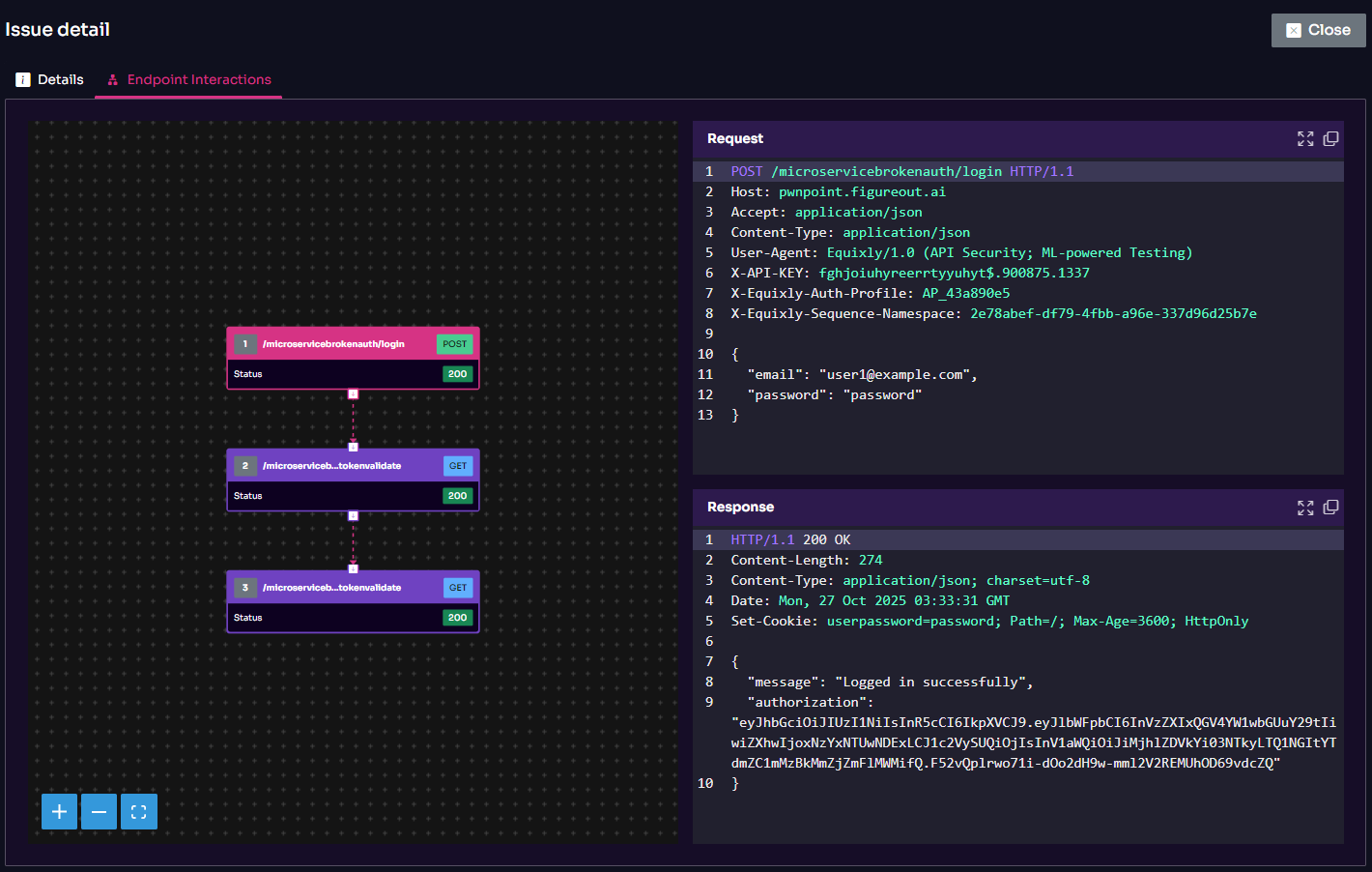
The ability to replay or modify requests within the interface lets development and DevSecOps teams validate their remediation efforts conveniently, without needing external tools or manual reconfiguration. This hands-on visibility transforms each finding into a clear learning opportunity, bridging the gap between automated testing and developer understanding.
Dictionary for Testing
Equixly’s dictionary consists of predefined keys derived from your OAS or Postman specification files. This dictionary provides example values during testing, allowing for faster setup and consistent test execution.
You can also mark specific values as sensitive in case you want to add a layer of control and security during test runs.
Scheduling and Reporting
The scheduling feature automates scan execution. It allows you to set start and end dates, and choose how often scans run—daily, weekly, monthly, yearly, or a custom cron expression. All scheduled scan results appear in the dashboard.
For formal review, you can generate a report based on a specific scan. The output is a downloadable, password-protected ZIP file containing a PDF or CSV report.
Consider that you can generate reports even when Equixly doesn’t find any security issues. The point of this option is to provide you with a comprehensive view of data classification and scan coverage, each of which has its own merits.
Conclusion
Equixly is designed to integrate into the development and operations processes, shifting security left without requiring developers to be full-time security experts. Through automation, actionable feedback, and contextual intelligence—from custom authentication hooks and API specifications to clear remediation advice—Equixly enables developers and DevSecOps teams to manage API risk effectively and continuously, without friction across teams.
Does integrating Equixly into your workflow sound like the right move?
Get in touch with our team—we’d be happy to answer your questions.
FAQs
What API and SDK options does Equixly provide for programmatic integration?
Equixly provides a REST API that lets you programmatically trigger scans, retrieve results, and manage configurations.
For advanced or custom workflows, Equixly also offers a JavaScript SDK that supports custom scripting. The SDK allows you to implement dynamic authentication logic—such as generating AWS SigV4 signatures through custom hooks—making it easy to integrate with APIs that use advanced or security-enforced authentication.
How does Equixly handle sensitive data, and what is its approach to testing different environments?
Equixly incorporates data classifications during the scan to highlight the presence of sensitive information, such as PCI and PII, requested or obtained via APIs. To further protect this information, Equixly applies data masking techniques during analysis, ensuring that sensitive values are never exposed in reports or logs.
Also, the platform’s Is Production URL flag provides a critical safeguard: When enabled, Equixly bypasses potentially destructive operations, such as form submissions, to preserve data integrity in production-like settings.
For internal networks, the Equixly Space Link agent allows secure scanning of private endpoints.
How can I ensure continuous security testing and integrate results into my existing tools?
Equixly supports scheduling for automated scan execution (daily, weekly, monthly, or custom). And it uses a lightweight distroless container image for integration into CI/CD pipelines (GitHub Actions, Jenkins, etc.).
After a scan completes, webhooks automatically send a structured JSON payload with scan details, allowing you to trigger custom actions, log results in issue trackers, or forward data to security monitoring systems.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.

Edoardo Zatti
Technical Product Manager
With a master's degree in Theoretical Physics, Edoardo has established a robust analytical thinking and problem-solving foundation. During the final year of his studies, he taught an integration course at the university, refining his communication skills and kindling his passion for education. His academic journey took an exciting turn during his master's program as he ventured into the field of computer science through relevant courses. These courses sparked his interest in IT and led him to specialize in backend development, where he sharpened his skills through involvement in complex projects and practical experience in other Tech companies.