October Product Update

At Equixly, we are constantly evolving our platform to empower you with more insight and control over your API security. We’re thrilled to introduce our latest updates, designed to streamline authorization testing, provide real-time scan visibility, and enhance your overall project management experience.
Predicted Authorization Matrix
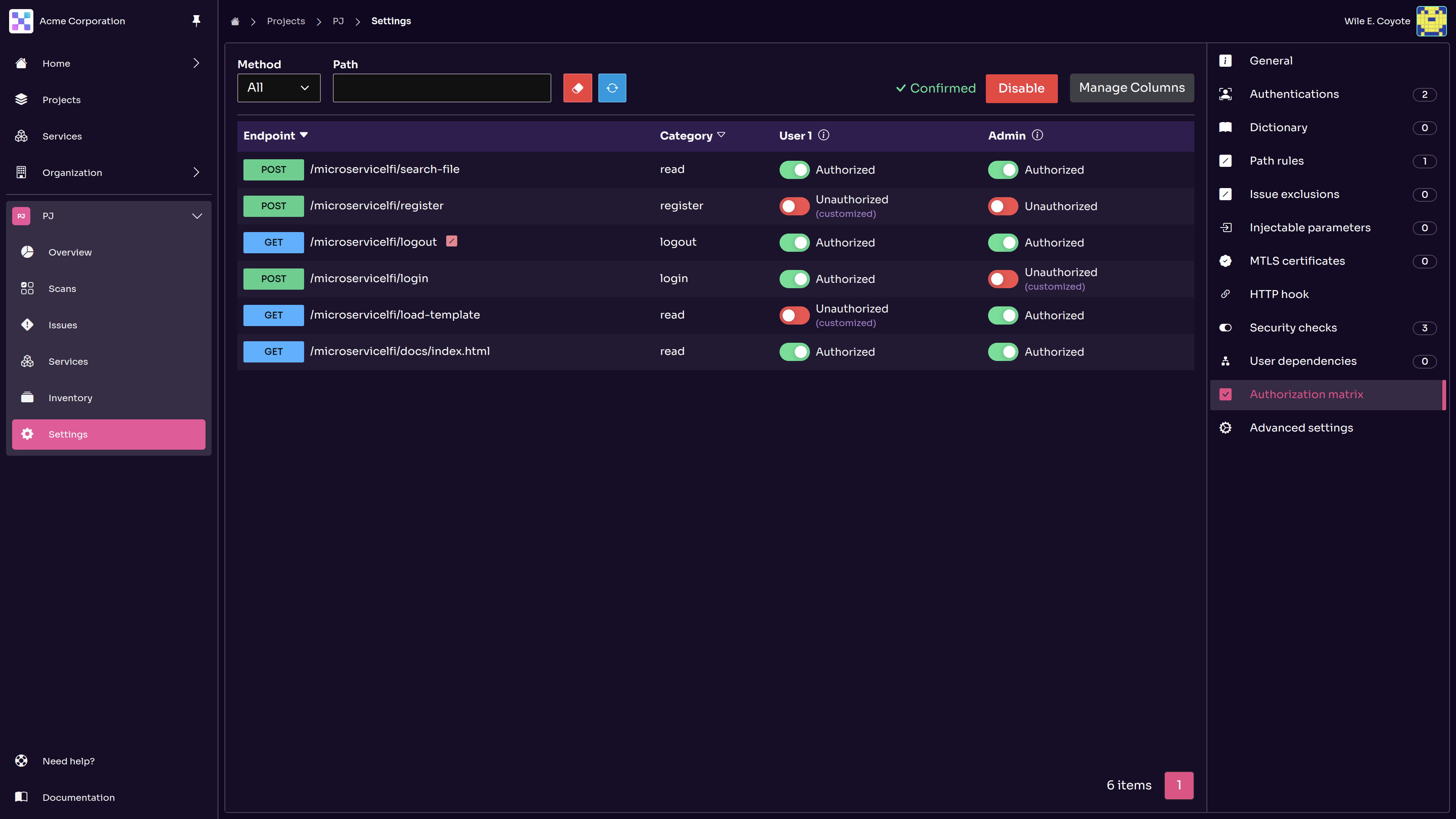
Broken Object Level Authorization (BOLA) remains one of the most critical and widespread API vulnerabilities. To combat this, we’ve introduced a new Predicted Authorization Matrix feature. This allows you to define role-based access rules in natural language, automatically generating a clear matrix of who should access what.
Once confirmed, Equixly uses this matrix to test systematically for BOLA vulnerabilities by simulating privilege escalation attacks. This ensures that users cannot access data beyond their permissions, providing a level of automated coverage that is difficult to achieve manually. Now, you can proactively close critical security gaps and ensure your APIs are secure by design.
Real-Time Visibility with Scan Insights
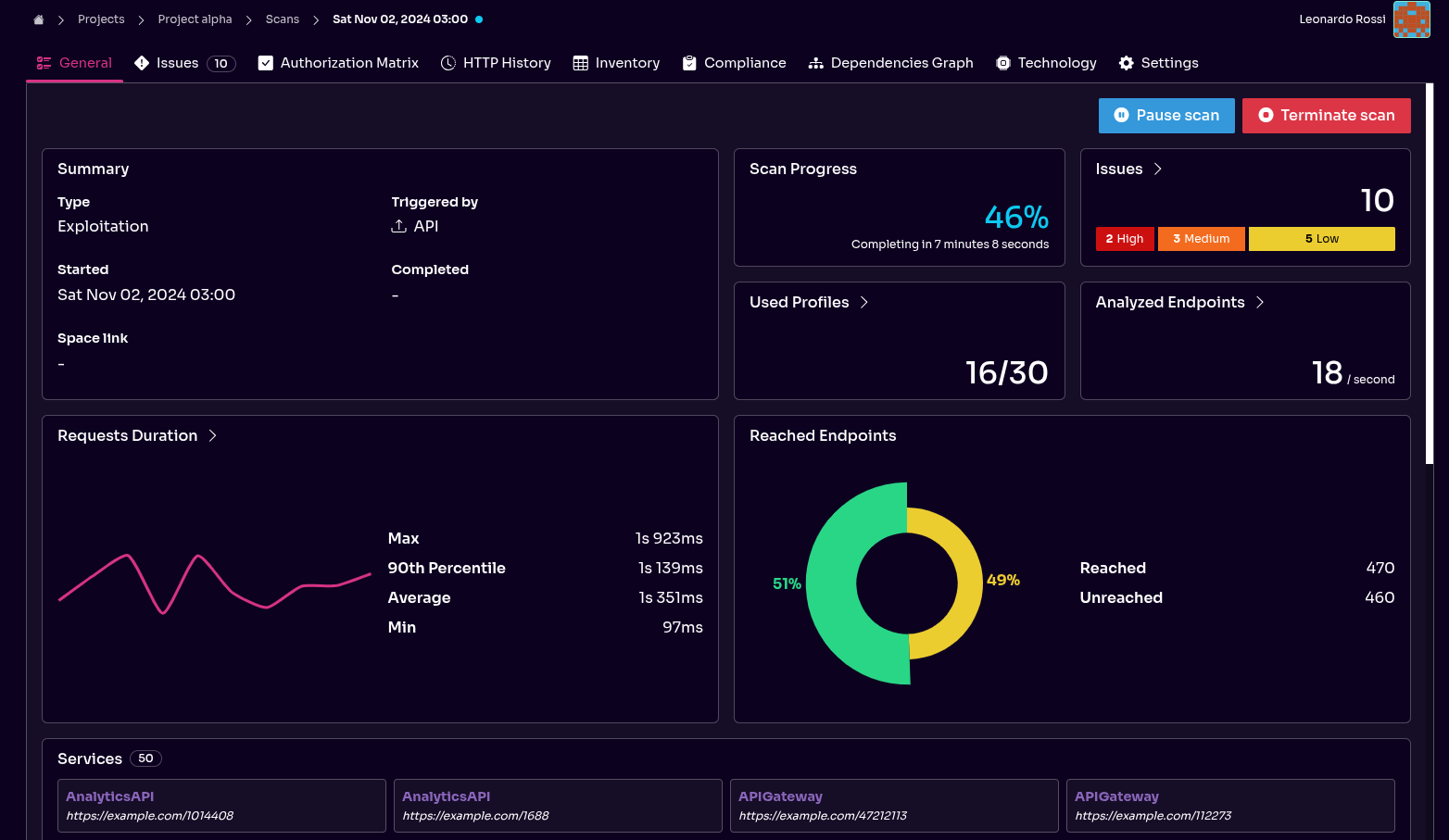
Waiting for a scan to complete to get feedback is a thing of the past. Our new Scan Insights feature gives you a real-time window into your security tests as they run. You can monitor scan progress with an estimated completion time, verify that authentication works correctly, and track which endpoints have been tested.
A new performance graph also displays key request duration metrics, helping you identify performance bottlenecks during the test. These insights allow you to validate configurations on the fly, optimize scan performance, and make faster, more informed decisions without waiting for the final report.
Flexible Authentication for Targeted Testing
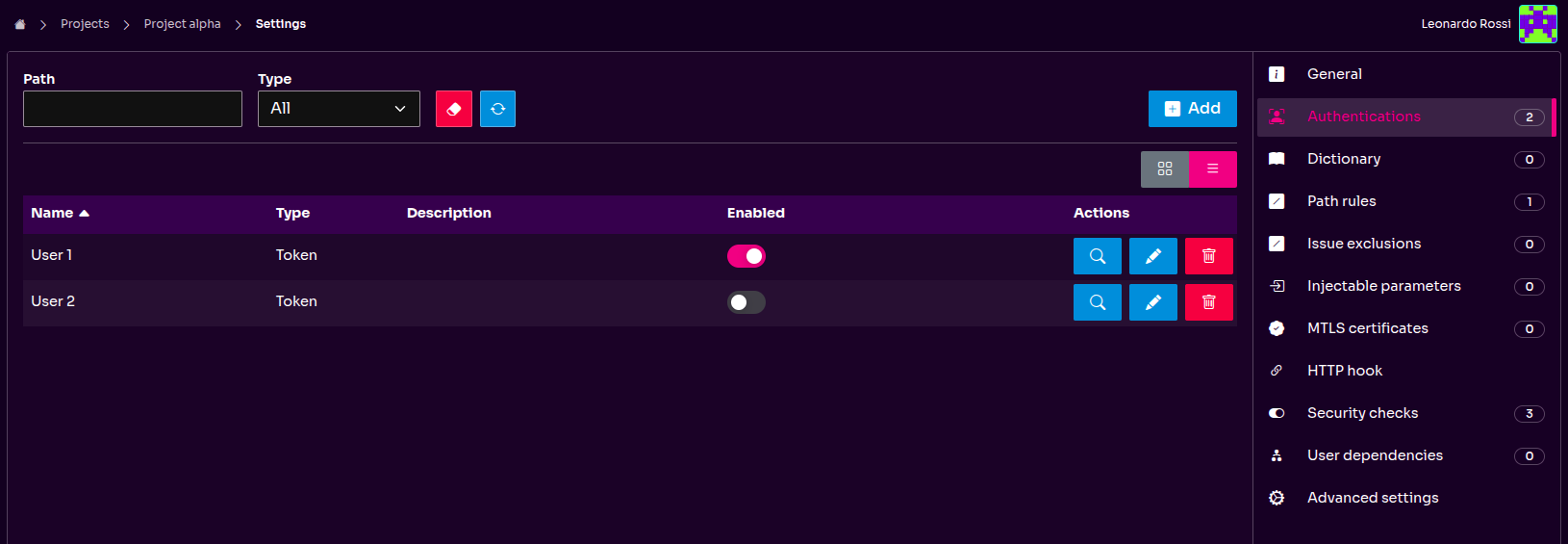
We’ve made it easier to test different access scenarios by allowing you to turn authentication settings on or off for each scan. You can now choose which authentication profiles to use without having to remove them from your project configuration.
This flexibility is perfect for testing unauthenticated endpoints, isolating specific user roles, or temporarily excluding a credential. It streamlines your workflow by allowing you to tailor each scan to your exact needs, enabling more targeted and efficient security assessments.
Streamlined Project Lifecycle Management
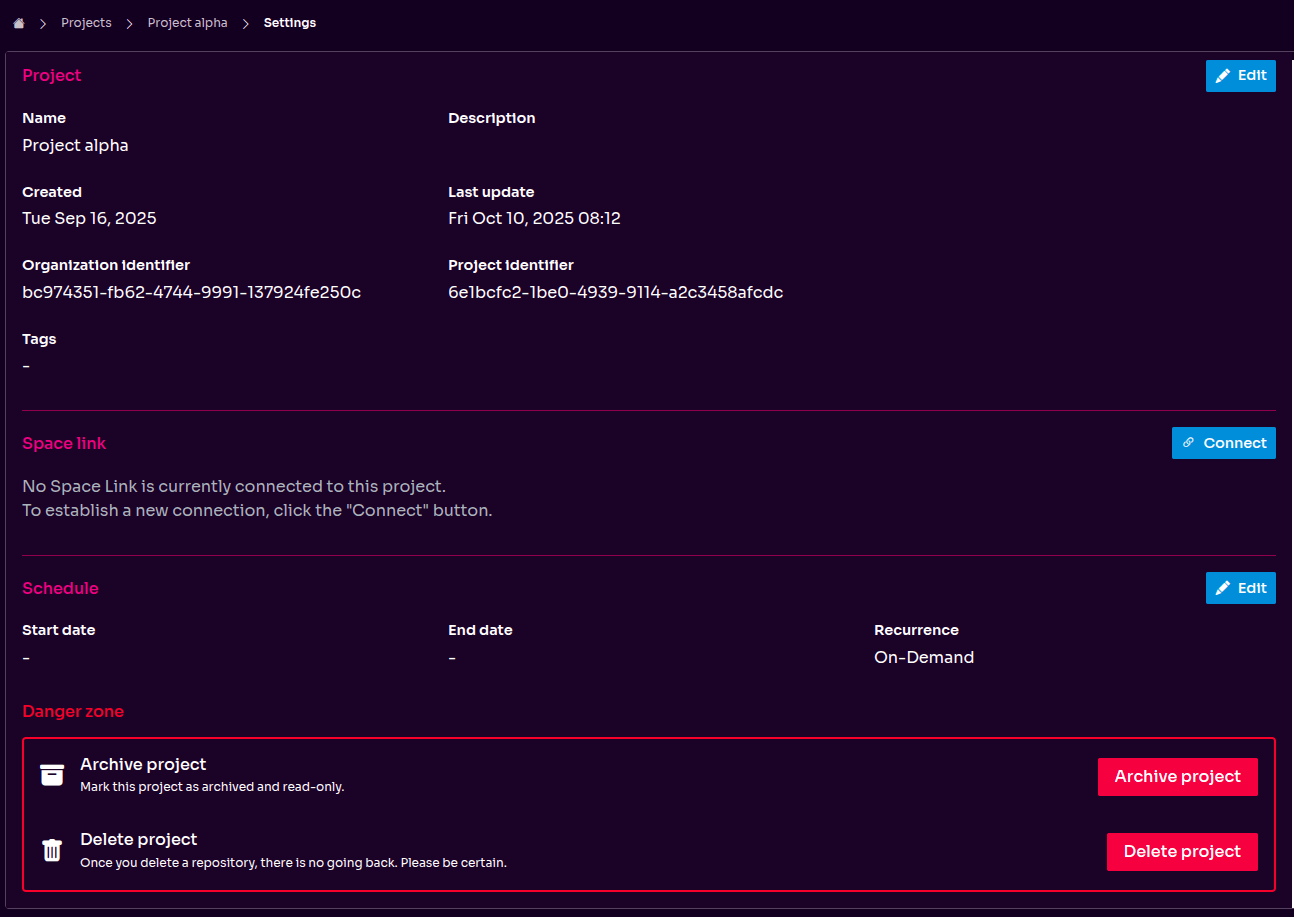
To help you maintain a clean and organized workspace, we’ve enhanced Project Lifecycle Management with new “Unarchive” and “Delete” capabilities. Archiving a project is no longer a permanent action—you can now restore projects whenever you need them.
We have also removed the 30-day waiting period for deleting projects, giving you immediate control over your workspace. These changes provide greater flexibility and efficiency in managing your projects, allowing your team to stay focused and organized.

Edoardo Zatti
Technical Product Manager
With a master's degree in Theoretical Physics, Edoardo has established a robust analytical thinking and problem-solving foundation. During the final year of his studies, he taught an integration course at the university, refining his communication skills and kindling his passion for education. His academic journey took an exciting turn during his master's program as he ventured into the field of computer science through relevant courses. These courses sparked his interest in IT and led him to specialize in backend development, where he sharpened his skills through involvement in complex projects and practical experience in other Tech companies.