API Authorization Matrix: Automated Testing for BOLA and Access Flaws
Zoran Gorgiev, Alessandro Begal
For the modern enterprise, APIs represent a primary point of exposure. They are the new perimeter, and as digital transformation intensifies, security and business decision makers face a critical control issue: The complex, brittle challenge of authorization.
Failure to verify what an authenticated identity is permitted to do is not a simple bug. It’s a business logic flaw that undermines the principle of least privilege (PoLP). And it ends in non-compliance, data leakage, and breaches.
This article addresses the operational imperative of effectively managing API authorization. It
- Discusses in detail what an API authorization matrix is
- Explains why manual testing is a strategic liability
- Outlines the mandate for automated security testing as key to defeating security threats, such as Broken Object Level Authorization (BOLA)—the most common and severe API vulnerability in the OWASP Top 10 Security Risks.
The API Authorization Matrix: A Pillar of Security Governance
The API authorization matrix is the blueprint for access control. It maps roles to API permissions and resources, providing a structured way to enforce access policies across APIs.
While organizations rarely implement the authorization matrix as a literal table due to scalability issues, the concept still governs access decisions. Instead of maintaining a giant spreadsheet of rules, they translate the matrix into access policies coded into the application, where they become part of the server’s runtime logic.
The matrix captures three dimensions of access control:
- Identities (R): Roles such as Admin, Partner, or Customer
- Permissions (P): API operations like GET /account or POST /transaction
- Objects (O): Concrete resources such as Order ID 100 or User ID 25
The combination of the three dimensions (R × P × O) guarantees that every possible action has a defined outcome:
- Authorized requests result in 200 OK
- Unauthorized return 403 Forbidden
Role-based access control (RBAC) is the most widely used authorization model for APIs, representing a practical implementation of the authorization matrix. Other models, such as attribute-based access control (ABAC) or relationship-based access control (ReBAC), extend the same matrix principle with additional flexibility.
In practice, the matrix is enforced during an authorization lookup. After authentication—say via JWT or OAuth—the server checks the user’s role against the requested action and resource. It then evaluates the relevant policies coded into the application—for instance, “Managers may update any product.” If the request matches a policy, the API executes the business logic; if not, the system denies access.
It’s worth noting that the authorization matrix is not encoded in an OpenAPI specification (OAS) file. Still, it complements the matrix by defining what security requirements apply to each API endpoint, while the matrix specifies how those requirements are enforced in detail. Together, they provide both a specification-level view and a governance-level blueprint, ensuring consistency between documentation and runtime behavior.
The Strategic Threat: When Identity Fails Integrity
Authorization challenges dominate the modern API threat landscape, as attested by the OWASP API Security Top 10. These risks are subtle. They occur in the logical connections between users, data, and permitted actions rather than malformed requests. Among them, BOLA stands out as the most pervasive and damaging.
BOLA occurs when an API endpoint accepts an identifier—a user ID, account number, or order reference—but fails to perform a secondary server-side check to confirm that the authenticated user is authorized to access the requested resource. For an attacker, exploitation is straightforward:
- Authenticate as a standard user
- Send a legitimate request to view their own data, for instance: /api/v1/accounts/self_id
- Modify the object ID to target another user: /api/v1/accounts/victim_id
If the system responds with the victim’s data, authorization integrity has collapsed. Since the request is syntactically valid, traditional WAFs and signature-based defenses provide no protection. The failure is semantic, rooted in business logic.
The severity of BOLA is exacerbated by the ease with which attackers can harvest resource identifiers.
Even complex GUIDs are often revealed in regular API responses. That allows adversaries to collect IDs from multiple endpoints and automate large-scale attacks across read, update, and delete functions. What appears to be a narrow flaw becomes a mass data-exfiltration risk with consequences ranging from financial losses to reputational harm and class-action litigation tied to exposed personally identifiable information (PII).
Putting the onus on developers to implement perfect authorization checks in every function is unsustainable. In fast-changing microservices environments, role- or attribute-based access control introduces enormous complexity, and frequent updates increase the likelihood of authorization regressions.
The architecture itself—say the reliance on distributed services and multiple databases—further worsens the problem, as organizations often manage and enforce a user’s authorization state across various components.
Without an automated, authoritative system for verification, authorization vulnerabilities remain hidden in production, waiting silently for attackers to exploit them.
Why Manual Verification Is Lacking
Manual testing, or even relying on standard functional tests, is strategically inadequate for the matrix because of the
- Combinatorial explosion: A system with only five roles, 50 endpoints, and object-level permissions requires hundreds of thousands of individual test permutations to verify security logic, rendering manual audits cost-prohibitive and incomplete.
- Decoupled logic: The authorization rules are often decoupled from the API endpoint code, residing in separate policy engines or service layers. That improves architecture but complicates manual testing, as the tester must verify the outcome of two separate systems.
- Development drift: Without continuous, automated enforcement, the security policy is subject to developer interpretation and code changes, resulting in the deployed access control inevitably drifting from the documented security governance.
To put the combinatorial explosion into a quantifiable context: Imagine a medium-sized application with 500 API endpoints and 10 distinct user roles.
That immediately creates 5,000 unique function-level authorization vectors (R × P). Let’s say that only 10% of those endpoints handle object-level IDs (50 endpoints). If we test for GET, PUT, and DELETE BOLA attacks across two different unauthorized roles, the total number of security tests exceeds 30,000 distinct permutations.
A human penetration tester or manual QA team cannot execute, document, and repeat this scope of negative testing within any reasonable development sprint. The time required for full coverage makes the security sign-off the primary bottleneck, forcing a compromise on coverage that leaves critical BOLA flaws unaddressed.
The only logical conclusion is that assurance must be computational, that is, automated.
The Case for Automation and Shift Left
Efficient API authorization matrix testing depends on two complementary practices: Establishing automated, exhaustive testing and shifting authorization validation to the left by embedding it directly into the CI/CD pipeline. Together, these measures ensure that your organization continuously executes security, rather than retrofitting it late in the cycle.
Automation enables you to carry out two critical forms of checks against every deployed or updated API:
- Positive case testing: Authorized roles must successfully perform required functions, validating operability.
- Negative case testing: Unauthorized roles must be blocked at the object and function levels, confirming that 403 Forbidden responses are consistently enforced.
By covering both dimensions comprehensively, automated testing closes the security gap created by BOLA and other access flaws. It programmatically verifies that APIs remain resistant to privilege escalation, regardless of an attacker’s creativity.
Embedding these checks into the CI/CD pipeline is indispensable in modern DevSecOps. It changes security from being a stage-gate audit to becoming a continuous quality check that accompanies every code change. This integration is critical for three reasons:
- Immediacy of feedback: Developers learn of authorization failures within minutes of a commit, making fixes timely and cost-effective.
- Reliability of policy enforcement: The automated suite becomes the authoritative definition of access rules, far more dependable than static documentation.
- Auditability: Each run creates a verifiable record of compliance, satisfying regulatory and governance requirements.
Shifting left in this way reduces the burden on individual developer vigilance and instead enforces a centralized, automated authorization policy. As a result, organizations can retain a high deployment pace while preserving the integrity of their security posture.
Equixly: Continuous AI-Automated Authorization Testing
Using AI-fueled grey-box testing, Equixly systematically validates role-based access rules across API endpoints, with a special focus on BOLA and related access flaws.
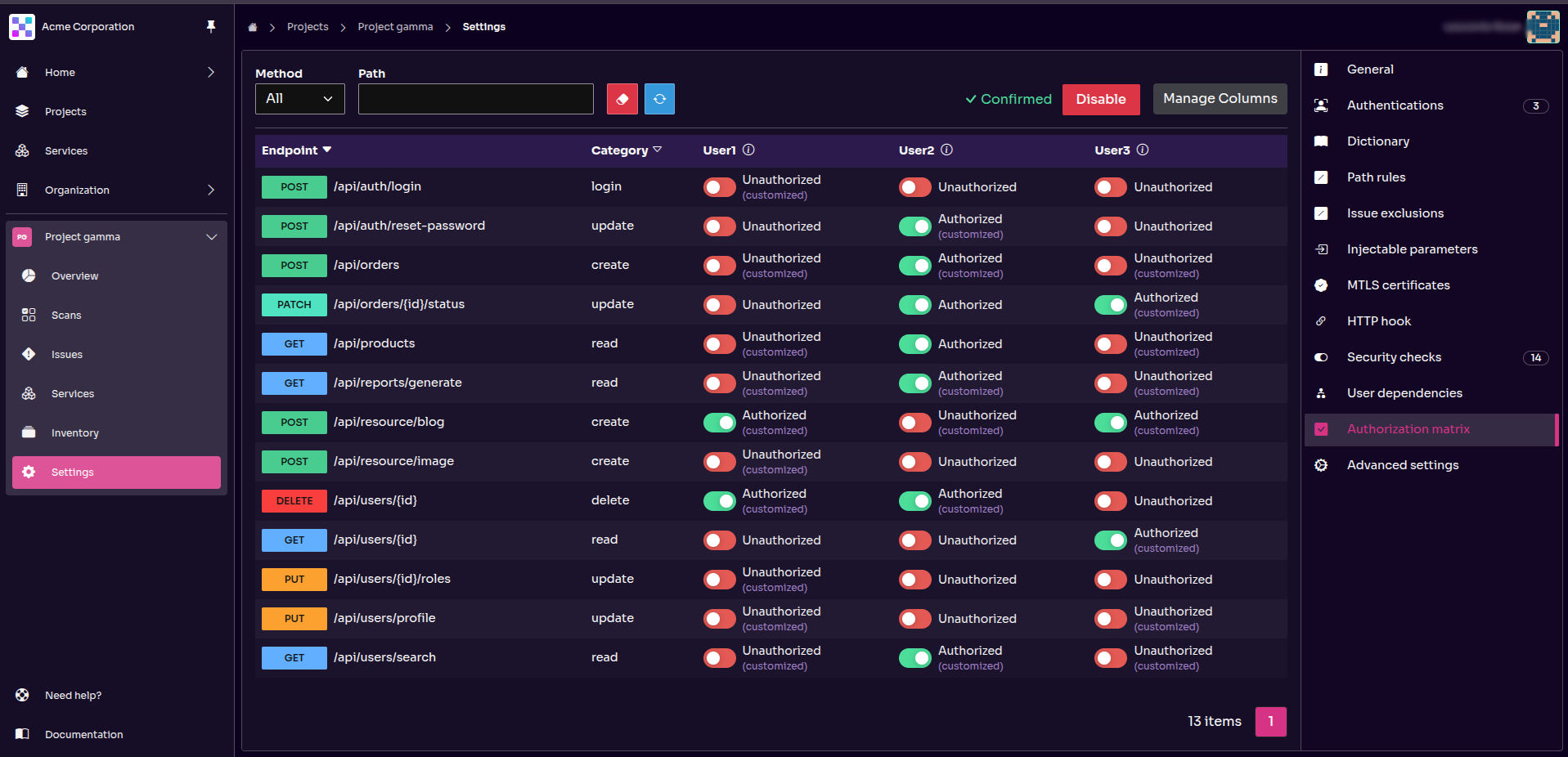
To harness this functionality, you need to access the ‘Authorization Matrix’ feature in the project settings.
Before generating an authorization matrix in Equixly, you must define at least one access rule for a service and a user within the dashboard. The detail, granularity, and clarity of your rules directly affect the depth and accuracy of both the matrix and the resulting security tests.
Access rules can be written in natural language—no specialized syntax is required. However, the clearer and more precise the rules, the more comprehensive and accurate the generated matrix and tests will be.
Once your rules are defined, you can generate the matrix. Before using it in scans, you must confirm the matrix; you may edit it beforehand if needed. Note that rewriting an access rule requires regenerating the matrix, as it fundamentally alters both the matrix and the testing process.
You’ll also need to regenerate the matrix whenever you add new users, since Equixly automatically invalidates the existing one in that case.
When everything is set, the platform runs automated attack simulations to test for vertical privilege escalation, where a low-privilege user attempts to access admin-only resources. These tests depend on the authorization matrix—without it, you cannot execute vertical BOLA testing, as the matrix defines which access relationships to validate.
During simulation, Equixly creates authenticated user sessions and identifies potentially vulnerable endpoints that use object identifiers. Each scenario verifies that unauthorized requests are correctly denied (HTTP 403/401), preventing unintended data exposure.
Equixly’s AI agents bring logic-aware reasoning that traditional scanners lack. They recognize semantic equivalence between endpoints—e.g., /users/123/data and /records?user_id=123—and generate context-aware payloads using UUIDs, sequential IDs, or encoded formats. The system also maintains multiple user states simultaneously, enabling large-scale “create as one, attack as another” testing.
Integrated directly into CI/CD pipelines, Equixly runs exhaustive retests whenever code changes touch authorization boundaries. Each run generates an auditable record, supporting compliance and eliminating regression risk.
For security engineers, this means automated coverage of thousands of test permutations that would be impossible to execute manually. For security leaders, it delivers verifiable assurance that authorization policies are consistently enforced across the API ecosystem—at scale and with speed.
Conclusion: Authorization as the Foundation of Digital Trust
The proliferation and complexity of modern APIs have made authorization the single most critical point of failure in the enterprise attack surface. The persistent threat of BOLA and other access flaws is a direct consequence of relying on inadequate methods to verify complex business logic.
The API authorization matrix provides the essential, verifiable discipline for modern security governance. Adopting AI-automated, exhaustive testing capabilities and integrating them into the CI/CD pipeline enables you to gain the strategic control needed to eliminate critical logic flaws, achieve non-repudiable compliance, and secure your most valuable asset: the integrity of your data access.
Transition from retrospective auditing to continuous, AI-automated authorization assurance with Equixly. Build resilient trust—get in touch to learn more.
FAQs
Why is manual or audit-based authorization testing insufficient for detecting BOLA and access flaws?
Because the combinatorial complexity of modern APIs makes exhaustive negative testing impossible for humans to perform consistently or at scale.
How can automated authorization matrix testing be integrated into CI/CD pipelines without slowing down deployments?
By running as a parallelized, policy-driven test suite, it delivers immediate feedback within the pipeline, guaranteeing speed and security are maintained simultaneously.
What makes AI-fueled authorization testing more effective than traditional scanners or penetration testing?
Testing carried out by AI agents, such as the one provided by Equixly, applies logic-aware reasoning to simulate real-world privilege escalation attempts across thousands of permutations, uncovering flaws that signature-based tools and manual tests routinely miss.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.

Alessandro Begal
Head of Solution Engineering
Alessandro has developed a broad technical background over the last 15 years in IT managed services, focusing on infrastructure management, data center modernization, network, and security. He has held various international leadership roles at an IBM company, emphasizing the importance of automation, with a proven track record of managing complex IT environments and leading teams to drive innovation and efficiency.