APIs in the Automotive Industry
Carlo De Micheli, Zoran Gorgiev
The traditional car attack surface included:
- Wi-Fi/GSM
- TPMS
- CAN bus
The current and future vehicle attack surface expands drastically on top of the traditional:
- EV charging ports
- Fleet server/OTA
- Traffic management
- Mobile apps, including third-party apps (external and in-car app store applications)
- APIs
API incidents were third in the most frequent automotive incidents in 2023. With the continued battle for competitive advantage between automotive companies largely dependent on comprehensive digitalization and APIs playing a pivotal role in the process, it’s safe to assume that API security will be one of the priorities in the future.
In this article, you’ll learn about the precise role of APIs in the automobile industry, read about recent API-related incidents with automotive companies, and discover how an AI-powered hacker might help you assess and fortify automotive APIs.
Why APIs in the Automotive Industry?
What function does an API perform in the automotive industry? What is its role? Why do smart cars and other connected vehicles need an API at all?
The answer lies in the term connected.
Take smart cars as an example since they are the closest to our everyday experiences and hearts. They are indeed computers on wheels and cannot perform either of their typical functions—the ones that make them smart, not just cars—without being connected to a stack of other software and the internet.
And how is this connectedness possible? Through APIs. APIs are the backbone of the communication between digital systems and what makes connected in connected vehicles possible.
How are APIs precisely used in the automotive industry?
APIs play a crucial role in:
- Charging management
- Internal, web, tablet, and OEM (original equipment manufacturer) mobile apps
- Automobile companies ERP (enterprise resource planning), CRM (customer relationship management), and billing systems
- Automotive OTA (over-the-air) and vehicle telematics
- In-vehicle infotainment, i.e., in-car entertainment systems
An automobile API:
- Passes information such as VINs (vehicle identification numbers), manufacturing details, and car specifications.
- Provides essential information on possible fixes and spare part numbers in service and repair, helping mechanics to work quickly and efficiently.
- Shows a vehicle’s location, fuel consumption, and mileage, issue digital car keys, give remote access to a car, and make self-driving possible, thus contributing immensely to convenience and better customer experience.
Automotive APIs Incidents
Have any automotive APIs already been exploited, or has the discussion of automotive API vulnerabilities been strictly theoretical?
The well-known security researcher Charlie Miller demonstrated the dangers of hacking smart cars in 2015. He and his colleague managed to gain control over a 2014 Jeep entirely remotely. Among other things, the security researchers could turn off the brakes at will. Can you imagine what would’ve happened if malicious actors had carried out an attack like this?
That is precisely why smart cars are unique: If malicious actors hack them, the consequences are much more extreme and existential than typical in cybersecurity. Hacked cars are a safety hazard where human lives are directly at risk.
Miller’s attack took a year-long preparation and happened almost ten years ago. In the meantime, a lot has changed. APIs have become ubiquitous, including in the automotive industry. And in the race for larger market share and industry predominance, many automobile companies have pushed for lightning bolt development, presumably inadvertently at the expense of security.
Hacking smart vehicles has become much easier and faster. What’s truly concerning is that this is not an isolated incident, and Chrysler is not the only car company vulnerable to malicious exploits. That is why APIs in the automotive industry are increasingly becoming victims of successful hacks.
In 2023, a group of ethical hackers based in Berlin managed to jailbreak an electric Tesla vehicle by launching an attack called fTPM unsealing. It allowed them to unseal TPM objects and find car credentials, which let them access Tesla’s server endpoints for cars. As if that wasn’t bad enough, they extracted disk encryption keys and got access to private user data (phonebook and calendar) as well.
Ethical hackers and security researchers have demonstrated that all the big automotive names—Tesla, Mercedez, BMW, Ferrari, Porsche, Toyota, and the list continues—suffer from one exploitable vulnerability or another. And it’s right there, in APIs, where things usually go south.
Sam Curry’s Hacks
In January 2023, security researcher and ethical hacker Sam Curry disclosed critical vulnerabilities in tons of automotive companies. When we say tons, we mean it. With his friends and colleagues, he hacked the following companies (brace for impact):
- Vehicle manufacturers: Acura, BMW, Ferrari, Ford, Genesis, Honda, Hyundai, Infiniti, Jaguar, Kia, Land Rover, Mercedez, Nissan, Porsche, Rolls Royce, and Toyota
- Vehicle products and services: Reviver, SiriusXM Connected Vehicle Services, and Spireon
Needless to say (and yet we’re saying it), we can’t give even the most abridged versions of all the hacks. Instead, we’ll focus only on one—the Reviver hack.
The Reviver Hack
Reviver is a company that offers virtual license plates. And it’s not just any digital license plate firm but the one that stands behind the most (possibly all) of the issued digital plates in the United States.
The Reviver digital plates contain a SIM card that allows owners to track their vehicles. One use of this functionality is if a car is stolen, its owner can find the car’s whereabouts and update the license plate to STOLEN. Digital plate management is possible through the Reviver mobile app (available for both Android and iOS devices).
Curry and his friends proxied the app’s traffic and soon discovered that everything related to the Reviver API was taking place on the website pr-api.rplate.com.
They created a user account, and when analyzing the traffic, they noticed that each Reviver user account was assigned to a distinctive JSON object. The object allowed users to update different fields, including the user type, and add new users (sub-users) to the existing account. That is where things got particularly interesting.
At first, the security researchers couldn’t find another value for the user type except the default CONSUMER. However, they decided to check whether the reset password function would reveal interesting new user-type information.
They discovered that the password reset link led to a URL, essentially a website, much richer in API endpoints than the website they had explored earlier. They inspected the JavaScript code on this site and found another user account type, CORPORATE.
The ethical hackers assigned the user account the newly discovered higher privilege CORPORATE role but still couldn’t make the most of its permissions because the website threw authorization errors. To bypass this restriction, they invited new users to the elevated privileges account, to whom they assigned higher permissions in the usual way, i.e., not by users assigning higher privileges themselves.
That did the trick. The invited users could enjoy the newly assigned higher permissions without any obstacles, which led the researchers to believe they could use the same method to elevate user privileges even higher.
They used wordlists to brute-force the user type and discovered new user account types: REVIVER-ROLE and REVIVER. The latter turned out to be an admin-type account.
The researchers repeated the same steps as before—elevating an existing account to a higher role and then inviting new accounts to assign them higher privileges—to acquire admin accounts.
As administrators, they could access other users’ data and make API calls to view car locations, update plates at their whim, and add new users with unrestricted authorization. In short, they gained full access to the Reviver fleet management functionality.
Mass Assignment
This vulnerability is an example of mass assignment. It was a separate security risk on the OWASP API Security Top 10 2019 list—API6:2019. The new 2023 list of the most severe and common API vulnerabilities included it as part of the API3:2023 Broken Object Property Level Authorization (BOPLA).
What is mass assignment?
In the simplest terms, it means that (regular) users can change and manipulate server-side variables they shouldn’t be allowed to modify. For instance, a user with an online banking account should be able to change their email address or personal information but not change their balance at will.
In Sam Curry’s case, he shouldn’t have been able to manipulate the user type variable to change his user account role to a higher-privilege user, let alone elevate it to the admin account level.
Exploiting a mass assignment vulnerability can be as easy as adding the line “admin”=true to an API request. However, it usually takes much more work than that. In most cases, hackers must first figure out the variables, values, and conventions for updating those variables and only then attempt to manipulate them.
That’s because there’s little uniformity across the board, i.e., different APIs use different server-side variables for similar functions and user roles. Suitable wordlists and fuzzing are one common route attackers take to surmount this obstacle.
David Colombo’s Tesla Hack
Sam Curry claims that of all the famous car manufacturers, Subaru is the one with the most robust security. He says something similar about Tesla and Tesla’s APIs.
We’re not sure about Subaru, but despite Tesla’s hardened security, another security researcher and ethical hacker, David Colombo, found a way to hack over 25 Tesla cars in 13 countries. And how did that happen? Through a third-party app. So, technically, it’s not Tesla to blame. But wait, there’s more to it. We’ll get there, we promise.
TeslaMate: Not Your Average Mate
It all started with David discovering flaws in the popular open-source self-hosted data logger for Tesla vehicles, TeslaMate. This app:
- Connects to your Tesla
- Receives data from it, such as trips, software updates, energy expenditure, charges, and similar
- Records this information
Smart vehicles like Tesla can produce up to several terabytes of data per hour. For this reason, TeslaMate includes Grafana (another open-source software) dashboards that present these oceans of data in a visual, orderly, logical, and understandable fashion.
The problem with the dashboards was that they allowed unauthorized guest access, meaning they were basically publicly accessible. David could freely see someone else’s dashboards, revealing a wealth of information about that person and how they used their Tesla.
But like any curious mind, David didn’t stop there. He wanted to see if he could use TeslaMate to establish remote control over Tesla vehicles. After all, the app gave away volumes of information on individual cars, so maybe it would allow prying eyes not just to track but also to control a vehicle remotely.
The app and Teslas communicated via API, so the ethical hacker needed authorized API access to execute remote commands. Authorized access meant possessing a user authentication token for the Tesla API.
Upon code inspection, David discovered that TeslaMate stored unencrypted API tokens in the same PostgreSQL database as the rest of the data.
Since, as we’ve seen, the car data was accessible through Grafana, the ethical hacker knew he might get his hands on API tokens through the Grafana Explore functionality. Unfortunately, this functionality required only default credentials (admin:admin), so David could enter and create custom queries to get Tesla API tokens without any hiccups.
Tesla API tokens are the equivalent of digital car keys for remote control. The leaked API tokens enabled him to send commands to Teslas remotely and perform the following actions:
- Unlock doors
- Flashed lights
- Find out the vehicle location
- Controlled the temperature in the car
- Turn out the Tesla’s security Sentry mode
- Start keyless driving despite the PIN to Drive option and without a user password
The Tesla API: It Happens Even to the Best of Them
David discovered over 300 potential targets. However, for legal reasons, he didn’t hack more than 25 since he had already discussed the security flaws he had found with the Tesla security team.
Tesla began revoking the API tokens for all the possibly impacted vehicles—which, by the way, were counted in thousands—right after David contacted the company.
However, the ethical hacker discovered another problem. This time, it wasn’t a third-party app that was vulnerable but the Tesla API itself. More specifically, David found that the API returned the requested email addresses of Tesla owners even when he used revoked API tokens to make the API calls.
Again, What Went Wrong?
Many things went wrong in this Tesla situation.
Starting with TeslaMate, the primary problem was improper authentication, as the National Institute of Standards and Technology (NIST) defines it in its National Vulnerability Database (NVD).
The app also relied on an insecure storage method, with unencrypted API tokens stored in the same database along with all other data.
Another problem was that there were no restrictions on what a single user could do from their geolocation. David should not have been able to make API calls for a vehicle in India from, say, the Netherlands or Germany. Even worse, one IP address accessed tens of cars in different parts of the world.
Regarding the Tesla API, it seemed that Tesla didn’t have an inventory of revoked API tokens, or the API wasn’t in sync with this inventory, which allowed the ethical hacker to call API endpoints with no longer valid API tokens.
In addition, the keyless driving endpoint allowed for the PIN to Drive security mechanism to be bypassed and called without the API requiring a password.
The Virtues of an AI-Powered Hacker
What is an AI-powered hacker?
Imagine the virtues of all the hackers we mentioned combined in one expert. Only this expert is not quite a typical representative of the human species. OK, not a human at all… more like a machine. In fact, a computer but with the same curious approach as Curry and Colombo, plus fueled by artificial intelligence. Well, that’s an AI-powered hacker.
It is an automated penetration tester or ethical hacker. It uses the same principles of work as (ethical) hackers, probing APIs and attacking them just like a hacker would. Why? To find vulnerabilities and oversights, inform you before threat actors find them and bring chaos to your cosmos.
One such example of an AI-powered hacker is Equixly. It alleviates pain points where there are budget and time restrictions and fills gaps where there’s a staffing void and missing expertise.
Since the team behind Equixly knows that, in many cases, the context determines whether an API action is legitimate, Equixly goes one step further than testing only for common API vulnerabilities. On top of testing for the OWASP Top 10 API Security Risks, it also searches for subtle context indicators that point to a barely perceptible business logic flaw or the omens for the birth of a zero-day.
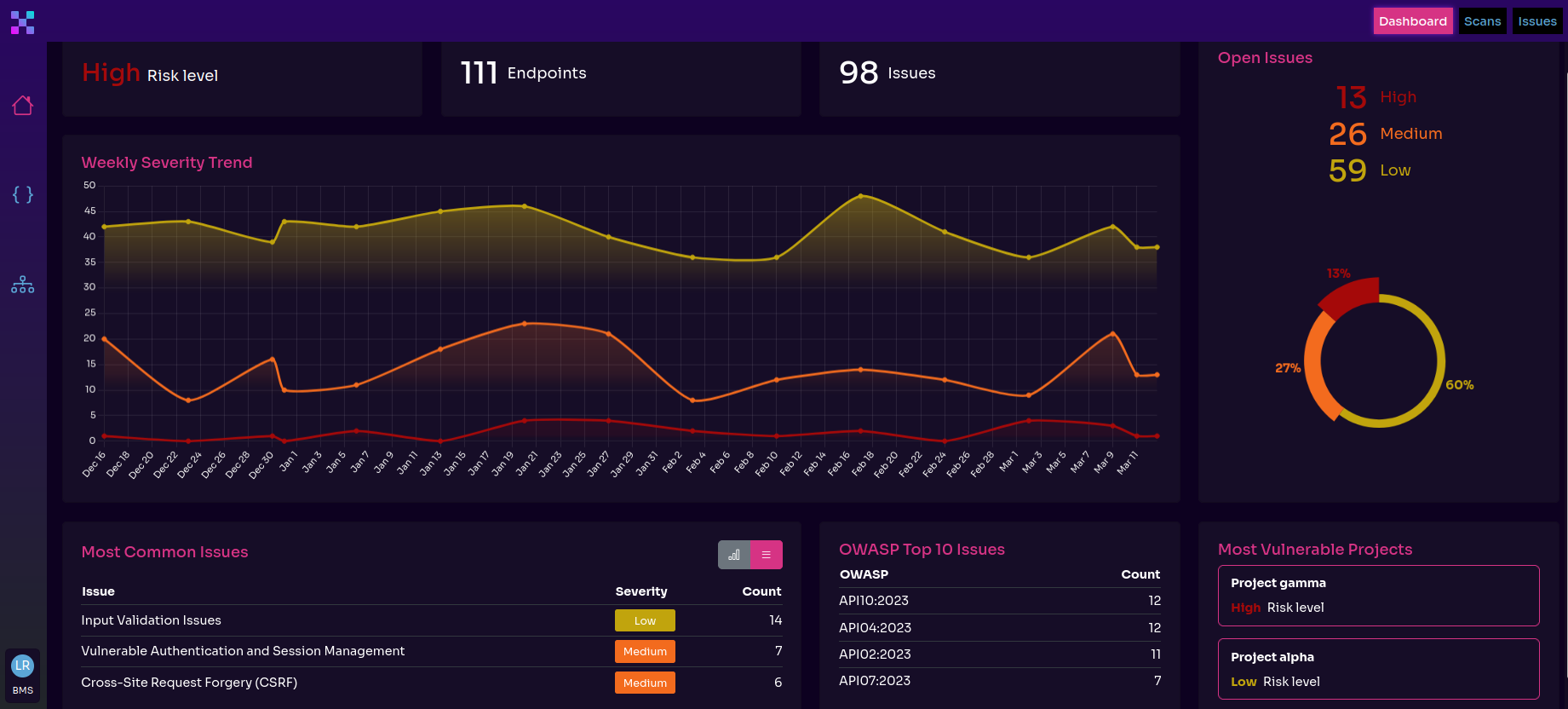
Besides, Equixly was meant for continuous testing, i.e., security testing in development for organizations that believe in proactive security and the shift left approach. And it makes the shadow and zombie API discovery possible and helps mend security weaknesses after significant software updates.
Conclusion
The automotive industry is flourishing with new digital technologies that are largely reliant on APIs. We don’t enjoy being the party-breakers here, but car API security mishandling often casts a shadow over the many joys of smart and connected vehicles, as Curry’s and Colombo’s hacks showed.
Security first must be the standard approach automotive companies and developers take when creating a better tomorrow through APIs. Better simply requires safe.
Download Equixly’s Automotive brochure:

Carlo De Micheli
Director of Product Marketing
Carlo is a versatile professional with extensive international experience. His enthusiasm for innovation extends across cybersecurity, automotive, and aerospace, where he actively engages in pioneering projects. Holding a technical background in aerospace engineering and supplementing it with independent studies in programming and security, Carlo has organized and presented at international conferences and established tech startups related to the sharing economy and fashion before embracing marketing and sales.

Zoran Gorgiev
Technical Content Specialist
Zoran is a technical content specialist with SEO mastery and practical cybersecurity and web technologies knowledge. He has rich international experience in content and product marketing, helping both small companies and large corporations implement effective content strategies and attain their marketing objectives. He applies his philosophical background to his writing to create intellectually stimulating content. Zoran is an avid learner who believes in continuous learning and never-ending skill polishing.